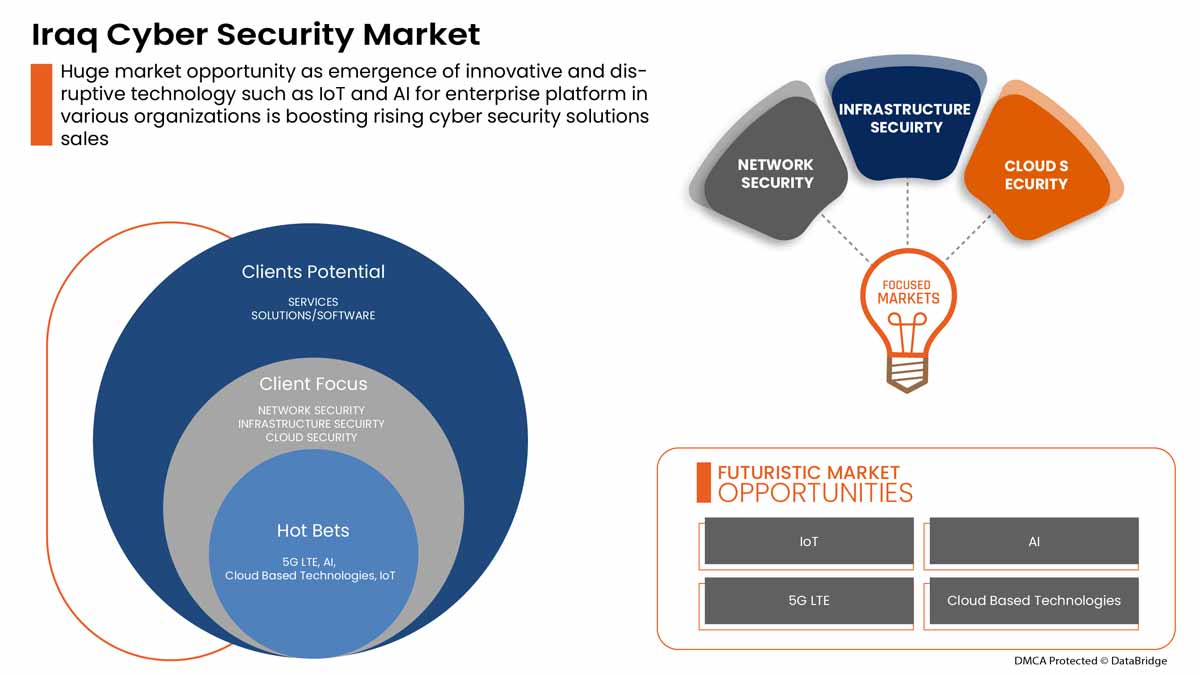
이라크 사이버 보안 시장, 제공 서비스(서비스 및 솔루션/소프트웨어), 애플리케이션(ID 및 액세스 관리, 데이터 보안 및 개인 정보 보호 서비스 제공, 거버넌스 위험 및 규정 준수, 통합 취약성 관리 서비스 제공 및 기타), 보안 유형(인프라 보안, 네트워크 보안 , 애플리케이션 보안, 클라우드 보안, 엔드포인트 보안 및 기타), 배포 모델(클라우드 및 온프레미스), 기업 규모(대기업 및 중소기업), 최종 사용자(산업, 상업, 정부 및 주거) - 업계 동향 및 2029년까지의 예측.
이라크 사이버 보안 시장 분석 및 통찰력
사이버 보안은 하드웨어, 소프트웨어 및 데이터와 같은 인터넷 연결 시스템을 사이버 위협 및 침해로부터 보호합니다. 클라우드 서비스 사이버 보안 솔루션의 증가와 원격 근무 문화의 출현이 시장을 주도하고 있습니다. 그러나 사이버 보안 위협의 증가와 사이버 보안 솔루션의 랜섬웨어가 성장을 제한할 수 있습니다.
사이버 보안에 대한 수요는 증가하고 있으며 앞으로도 증가할 것입니다. Data Bridge Market Research는 이라크 사이버 보안 시장이 2022년부터 2029년까지 연평균 성장률 6.3%로 성장할 것이라고 분석했습니다.
|
보고서 메트릭 |
세부 |
|
예측 기간 |
2022년부터 2029년까지 |
|
기준 연도 |
2021 |
|
역사적 연도 |
2020 (2019-2014까지 사용자 정의 가능) |
|
양적 단위 |
백만 단위의 값 |
|
다루는 세그먼트 |
제공(서비스 및 솔루션/소프트웨어), 애플리케이션(ID 및 액세스 관리, 데이터 보안 및 개인 정보 보호 서비스 제공, 거버넌스 위험 및 규정 준수, 통합 취약성 관리 서비스 제공 및 기타), 보안 유형(인프라 보안, 네트워크 보안, 애플리케이션 보안, 클라우드 보안 , 엔드포인트 보안 및 기타), 배포 모델(클라우드 및 온프레미스), 기업 규모(대기업 및 중소기업), 최종 사용자(산업, 상업, 정부 및 주거) |
|
적용 국가 |
이라크 |
|
시장 참여자 포함 |
BAE Systems, Microsoft, McAfee, LLC, Thales, Rapid7, Trend Micro Incorporated, Accenture, Cisco Systems, Inc., IBM Corporation, Oracle, Splunk Inc., Check Point Software Technologies Ltd., Palo Alto Networks, Fortinet, Inc., Juniper Networks, Inc., Micro Focus 및 Johnson Controls 등 |
시장 정의
사이버 보안은 하드웨어, 소프트웨어 및 데이터와 같은 인터넷 연결 시스템을 사이버 위협 및 침해로부터 보호합니다. 개인과 기업은 이 관행을 사용하여 데이터 센터 및 기타 지능형 시스템에 대한 무단 액세스를 보호합니다. 성공적인 사이버 보안 접근 방식은 안전하게 유지하려는 컴퓨터, 네트워크, 프로그램 또는 데이터에 분산된 여러 계층의 보호 기능을 갖추고 있습니다.
이라크 사이버 보안 시장 역학
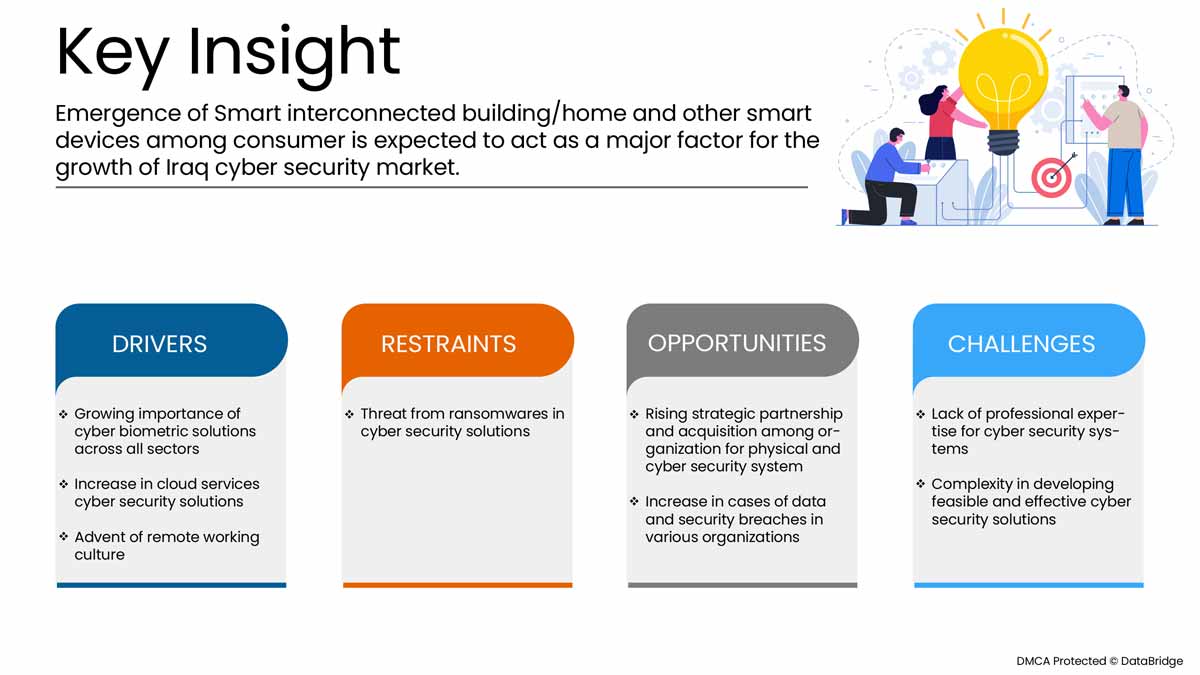
이 섹션에서는 시장 동인, 이점, 기회, 제약 및 과제를 이해하는 것을 다룹니다. 이 모든 내용은 아래에서 자세히 설명합니다.
운전자
- 원격근무 문화의 도래
최근 팬데믹으로 인해 직원들이 각자의 위치에서 원격으로 일해야 했기 때문에 원격 근무가 증가하고 있습니다. 수십 년 전만 해도 회사 사무실 밖에서 일하는 것은 덜 효율적이라고 여겨져 실현 불가능하다고 여겨졌습니다. 강력한 인터넷 연결과 같은 기술적 발전으로 인해 원격 근무가 이제야 주류가 되고 있으며, 이는 솔루션과 기타를 기반으로 할 수 있습니다.
- 클라우드 서비스 사이버 및 물리적 보안 솔루션 증가
클라우드 기술은 전 세계적으로 사용되는 필수적인 온라인 기술입니다. 클라우드 기술을 사용하면 사용자가 인터넷에 연결된 장치를 사용하여 저장소, 파일, 소프트웨어 및 서버에 액세스할 수 있습니다. 또한 인터넷을 통해 데이터와 프로그램을 저장하고 액세스할 수 있는 기능을 의미합니다. 기존의 하드웨어 및 소프트웨어 방법과 달리 클라우드 기술은 기업이 기존 방법에 많은 비용을 들이지 않고도 기술의 선두에 설 수 있도록 도울 수 있습니다.
기회
-
물리적 및 사이버 보안 시스템을 위한 조직 간 전략적 파트너십 및 인수 증가
물리적 및 사이버 보안 시장에서 지속적인 개선을 이루기 위해서는 프로젝트를 조정하고 투자하는 것이 필수적입니다. 이로 인해 정부와 기타 민간 기관은 파트너십과 인수를 통해 노력하고 있으며, 이를 통해 산업의 성장을 가속화하고 있습니다. 이를 통해 조직의 인지도와 이익을 구축하고, 이를 통해 산업에서 새로운 발명을 위한 범위를 만드는 데 도움이 됩니다. 또한 파트너십을 통해 회사는 고급 기술에 더 많이 투자하여 보다 안전하고 신뢰할 수 있는 물리적 및 사이버 보안 시장 서비스와 솔루션을 제공할 수 있습니다.
제지/도전
- 사이버 보안 위협 증가 및 물리적 및 사이버 보안 솔루션의 랜섬웨어
COVID-19로 인해 2020년 사이버범죄와 사이버보안 문제가 600% 증가했습니다. 네트워크 보안의 결함은 해커가 시스템 내에서 승인되지 않은 작업을 수행하는 데 악용하는 약점입니다. Purple Sec LLC에 따르면 2018년 모바일용 모바일 맬웨어 변종이 54% 증가했으며, 이 중 98%의 모바일 맬웨어가 Android 기기를 대상으로 합니다. 25%의 기업이 크립토재킹의 희생자가 된 것으로 추정됩니다. 다양한 회사에는 보안 산업도 포함됩니다.
Covid-19가 이라크 사이버 보안 시장에 미치는 영향
COVID-19는 이라크 사이버 보안 시장에 긍정적인 영향을 미쳤습니다. COVID-19로 인해 2020년에 사이버 범죄와 사이버 보안 문제가 600% 증가했습니다. 네트워크 보안의 결함은 해커가 시스템 내에서 승인되지 않은 작업을 수행하는 데 악용하는 약점입니다. Purple Sec LLC에 따르면 2018년에 모바일용 모바일 맬웨어 변형이 54% 증가했으며, 그 중 98%의 모바일 맬웨어가 Android 기기를 표적으로 삼았습니다. 25%의 기업이 크립토재킹의 희생자가 된 것으로 추정됩니다. 다양한 회사에도 보안 산업이 포함됩니다.
최근 개발
- 2022년 8월 Fortinet, Inc.는 기업이 분산된 인력을 보호할 수 있도록 돕는 새로운 SASE(Secure Access Service Edge) 및 SSE(Security Service Edge) 솔루션을 제공하기 위해 Comcast Business와의 파트너십을 발표했습니다.
- 2022년 5월, Cisco Systems, Inc.는 고급 사이버 보안 평가 도구를 출시했습니다. 솔루션 출시의 주요 목적은 중소기업(SMB)이 전반적인 보안 태세를 더 잘 이해할 수 있도록 하는 것이었습니다.
이라크 사이버 보안 시장 범위
사이버 보안 시장은 제공, 애플리케이션, 보안 유형, 배포 모델, 기업 규모 및 최종 사용자를 기준으로 세분화됩니다. 이러한 세그먼트 간의 성장은 산업의 빈약한 성장 세그먼트를 분석하고 사용자에게 핵심 시장 애플리케이션을 식별하기 위한 전략적 결정을 내리는 데 도움이 되는 귀중한 시장 개요와 시장 통찰력을 제공하는 데 도움이 됩니다.
헌금
- 서비스
- 솔루션/소프트웨어
이집트 사이버 보안 시장은 제공 항목을 기준으로 서비스와 솔루션/소프트웨어로 구분됩니다.
애플리케이션
- ID 및 액세스 관리
- 데이터 보안 및 개인 정보 보호 서비스 제공
- 거버넌스 위험 및 규정 준수
- 통합 취약성 관리 서비스 제공
- 기타
이집트 사이버 보안 시장은 응용 프로그램을 기준으로 신원 및 액세스 관리, 데이터 보안 및 개인 정보 보호 서비스 제공, 거버넌스 위험 및 규정 준수, 통합 취약성 관리 서비스 제공 및 기타로 구분됩니다.
보안 유형
- 인프라 보안
- 네트워크 보안
- 애플리케이션 보안
- 클라우드 보안
- 엔드포인트 보안
- 기타
보안 유형을 기준으로 이집트 사이버 보안 시장은 인프라 보안, 네트워크 보안, 애플리케이션 보안, 클라우드 보안, 엔드포인트 보안 등으로 구분됩니다.
배포 모델
- 구름
- 온프레미스
이집트 사이버 보안 시장은 배포 모델을 기준으로 클라우드와 온프레미스로 구분됩니다.
기업 규모
- 대기업
- 중소기업
기업 규모를 기준으로 이집트 사이버 보안 시장은 대기업과 중소기업으로 구분됩니다.
최종 사용자
- 산업
- 광고
- 정부
- 주거용
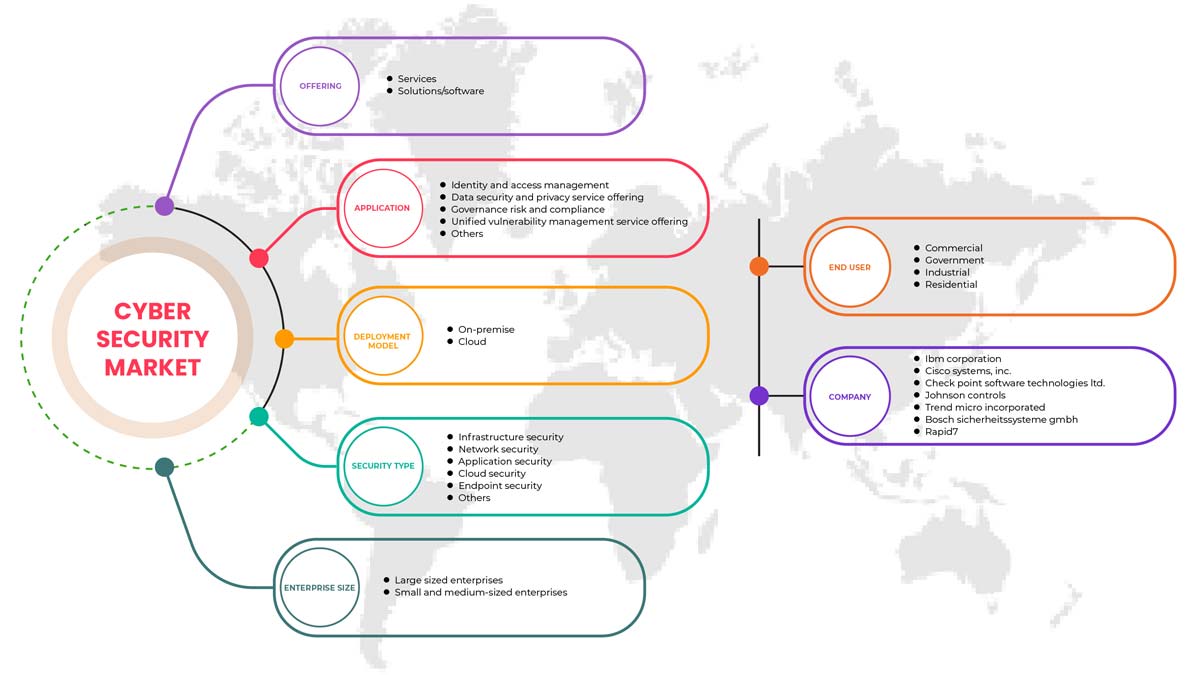
배포 모델을 기준으로 이집트의 사이버 보안 시장은 산업, 상업, 정부 및 주거용으로 구분됩니다.
이라크 사이버 보안 시장 지역 분석/통찰력
이라크 사이버 보안 시장을 분석하고, 국가, 제공 서비스, 애플리케이션, 보안 유형, 배포 모델, 기업 규모 및 최종 사용자별로 시장 규모에 대한 통찰력과 추세를 제공합니다.
보고서의 국가 섹션은 또한 개별 시장 영향 요인과 국내 시장의 현재 및 미래 트렌드에 영향을 미치는 규제 변경 사항을 제공합니다. 신규 판매, 교체 판매, 국가 인구 통계, 질병 역학 및 수출입 관세와 같은 데이터 포인트는 개별 국가의 시장 시나리오를 예측하는 데 사용되는 중요한 포인터 중 일부입니다. 또한 글로벌 브랜드의 존재 및 가용성과 현지 및 국내 브랜드와의 실질적 또는 희소한 경쟁으로 인해 직면한 과제는 판매 채널에 영향을 미치고 국가 데이터에 대한 예측 분석을 제공합니다.
경쟁 환경 및 이라크 사이버 보안 시장 점유율 분석
이라크 사이버 보안 시장 경쟁 구도는 경쟁자에 대한 세부 정보를 제공합니다. 포함된 구성 요소는 회사 개요, 회사 재무, 창출된 수익, 시장 잠재력, 연구 개발 투자, 새로운 시장 이니셔티브, 글로벌 입지, 생산 현장 및 시설, 생산 용량, 회사의 강점과 약점, 제품 출시, 제품 폭과 범위, 애플리케이션 우세입니다. 제공된 위의 데이터 포인트는 회사가 이라크 사이버 보안 시장에 집중하는 것과만 관련이 있습니다.
이라크 사이버 보안 시장의 주요 기업으로는 BAE Systems, Microsoft, McAfee, LLC, Thales, Rapid7, Trend Micro Incorporated, Accenture, Cisco Systems, Inc., IBM Corporation, Oracle, Splunk Inc., Check Point Software Technologies Ltd., Palo Alto Networks, Fortinet, Inc., Juniper Networks, Inc., Micro Focus 및 Johnson Controls 등이 있습니다.
SKU-
세계 최초의 시장 정보 클라우드 보고서에 온라인으로 접속하세요
- 대화형 데이터 분석 대시보드
- 높은 성장 잠재력 기회를 위한 회사 분석 대시보드
- 사용자 정의 및 질의를 위한 리서치 분석가 액세스
- 대화형 대시보드를 통한 경쟁자 분석
- 최신 뉴스, 업데이트 및 추세 분석
- 포괄적인 경쟁자 추적을 위한 벤치마크 분석의 힘 활용
목차
1 INTRODUCTION
1.1 OBJECTIVES OF THE STUDY
1.2 MARKET DEFINITION
1.3 OVERVIEW OF IRAQ PHYSICAL AND CYBER SECURITY MARKET
1.4 CURRENCY AND PRICING
1.5 LIMITATIONS
1.6 MARKETS COVERED
2 MARKET SEGMENTATION
2.1 MARKETS COVERED
2.2 GEOGRAPHICAL SCOPE
2.3 YEARS CONSIDERED FOR THE STUDY
2.4 DBMR TRIPOD DATA VALIDATION MODEL
2.5 PRIMARY INTERVIEWS WITH KEY OPINION LEADERS
2.6 DBMR MARKET POSITION GRID
2.7 VENDOR SHARE ANALYSIS
2.8 MARKET END USER COVERAGE GRID
2.9 MULTIVARIATE MODELING
2.1 COMPONENT TIMELINE CURVE
2.11 OFFERING TIMELINE CURVE
2.12 SECONDARY SOURCES
2.13 ASSUMPTIONS
3 EXECUTIVE SUMMARY
4 PREMIUM INSIGHTS
4.1 INVESTMENT POLICY
4.1 CASE STUDY
4.1.1 SECURE SOFTWARE DEVELOPMENT INFRASTRUCTURE
4.1.2 SOC-AS-A-PLATFORM (SOCAAP)
4.1.3 RANSOMWARE & FORENSICS ANALYSIS
4.1.4 WISCONSIN'S DEER DISTRICT SECURITY PLAN
4.1.5 LICENSE PLATE READERS IN SCHOOLS
4.1.6 K-12 SCHOOLS
4.2 VALUE CHAIN ANALYSIS
4.3 PORTERS FIVE FORCES
4.4 PESTLE ANALYSIS
4.5 TECHNOLOGICAL LANDSCAPE
4.5.1 AI AND MACHINE LEARNING
4.5.2 IOT
4.5.3 BLOCKCHAIN
4.6 REGULATORY STANDARDS
4.6.1 CYBER SECURITY
4.6.2 PHYSICAL SECURITY
4.7 LOCAL PLAYERS LIST
5 MARKET OVERVIEW
5.1 DRIVERS
5.1.1 ADVENT OF REMOTE WORKING CULTURE
5.1.2 INCREASE IN CLOUD SERVICES CYBER AND PHYSICAL SECURITY SOLUTIONS
5.1.3 GROWING IMPORTANCE OF PHYSICAL BIOMETRIC SOLUTIONS ACROSS ALL SECTORS
5.1.4 EMERGENCE OF SMART INTERCONNECTED BUILDING/HOME
5.2 RESTRAINTS
5.2.1 RISE IN CYBER SECURITY THREAT AND RANSOMWARE IN PHYSICAL AND CYBER SECURITY SOLUTIONS
5.3 OPPORTUNITIES
5.3.1 RISING STRATEGIC PARTNERSHIP AND ACQUISITION AMONG ORGANIZATIONS FOR PHYSICAL AND CYBER SECURITY SYSTEM
5.3.2 EMERGENCE OF VARIOUS DISRUPTIVE TECHNOLOGY SUCH AS IOT AND AI FOR VARIOUS INDUSTRIES
5.3.3 INCREASE IN CASES OF DATA AND SECURITY BREACHES IN VARIOUS ORGANIZATIONS
5.4 CHALLENGES
5.4.1 LACK OF PROFESSIONAL EXPERTISE FOR CYBER SECURITY SYSTEMS
5.4.2 COMPLEXITY ASSOCIATED WITH THE INTEGRATION OF VARIOUS PHYSICAL SECURITY SYSTEMS
6 IRAQ CYBER SECURITY MARKET, BY OFFERING
6.1 OVERVIEW
6.2 SERVICES
6.3 SOLUTIONS/SOFTWARE
7 IRAQ PHYSICAL SECURITY MARKET, BY COMPONENT
7.1 OVERVIEW
7.2 HARDWARE
7.2.1 VIDEO SURVEILLANCE SYSTEM
7.2.1.1 CAMERAS
7.2.1.2 RECORDERS
7.2.2 PHYSICAL ACCESS CONTROL SYSTEM
7.2.2.1 BIOMETRICS
7.2.2.2 LOCKS
7.2.2.2.1 ELECTRONIC LOCKS
7.3 SERVICES
7.3.1 MANAGED SERVICES
7.3.2 PROFESSIONAL SERVICES
7.4 SOFTWARE
8 IRAQ PHYSICAL SECURITY MARKET, BY AUTHENTICATION
8.1 OVERVIEW
8.2 SINGLE- FACTOR AUTHENTICATION
8.3 TWO- FACTOR AUTHENTICATION
8.4 THREE- FACTOR AUTHENTICATION
9 IRAQ CYBER SECURITY MARKET, BY APPLICATION
9.1 OVERVIEW
9.2 IDENTITY AND ACCESS MANAGEMENT
9.3 DATA SECURITY AND PRIVACY SERVICE OFFERING
9.4 GOVERNANCE RISK AND COMPLIANCE
9.5 UNIFIED VULNERABILITY MANAGEMENT SERVICE OFFERING
9.6 OTHERS
10 IRAQ CYBER SECURITY MARKET, BY SECURITY TYPE
10.1 OVERVIEW
10.2 INFRASTRUCTURE SECURITY
10.3 NETWORK SECURITY
10.4 APPLICATION SECURITY
10.5 CLOUD SECURITY
10.6 ENDPOINT SECURITY
10.7 OTHERS
11 IRAQ PHYSICAL AND CYBER SECURITY MARKET, BY DEPLOYMENT MODEL
11.1 OVERVIEW
11.2 ON-PREMISE
11.3 CLOUD
12 IRAQ PHYSICAL AND CYBER SECURITY MARKET, BY ENTERPRISE SIZE
12.1 OVERVIEW
12.2 LARGE SIZED ENTERPRISES
12.3 SMALL AND MEDIUM-SIZED ENTERPRISES
13 IRAQ PHYSICAL AND CYBER SECURITY MARKET, BY END USER
13.1 OVERVIEW
13.2 COMMERCIAL
13.3 GOVERNMENT
13.4 INDUSTRIAL
13.5 RESIDENTIAL
14 IRAQ CYBER SECURITY MARKET, COMPANY LANDSCAPE
14.1 COMPANY SHARE ANALYSIS: IRAQ
15 IRAQ PHYSICAL SECURITY MARKET, COMPANY LANDSCAPE
15.1 COMPANY SHARE ANALYSIS: IRAQ
16 SWOT ANALYSIS
16.1 DBMR ANALYSIS
16.1.1 STRENGTH
16.1.2 WEAKNESS
16.1.3 THREATS
16.1.4 OPPORTUNITY
17 COMPANY PROFILE
17.1 THALES GROUP
17.1.1 COMPANY SNAPSHOT
17.1.2 REVENUE ANALYSIS
17.1.3 PRODUCTS PORTFOLIO
17.1.4 RECENT DEVELOPMENTS
17.2 HANGZHOU HIKVISION DIGITAL TECHNOLOGY CO., LTD
17.2.1 COMPANY SNAPSHOT
17.2.2 REVENUE ANALYSIS
17.2.3 PRODUCT PORTFOLIO
17.2.4 RECENT DEVELOPMENTS
17.3 ACCENTURE
17.3.1 COMPANY SNAPSHOT
17.3.2 REVENUE ANALYSIS
17.3.3 SERVICE PORTFOLIO
17.3.4 RECENT DEVELOPMENTS
17.4 IDEMIA
17.4.1 COMPANY SNAPSHOT
17.4.2 PRODUCT PORTFOLIO
17.4.3 RECENT DEVELOPMENTS
17.5 BAE SYSTEMS
17.5.1 COMPANY SNAPSHOT
17.5.2 REVENUE ANALYSIS
17.5.3 SERVICE PORTFOLIO
17.5.4 RECENT DEVELOPMENT
17.6 FORTINET, INC.
17.6.1 COMPANY SNAPSHOT
17.6.2 REVENUE ANALYSIS
17.6.3 SERVICE PORTFOLIO
17.6.4 RECENT DEVELOPMENTS
17.7 PALO ALTO NETWORKS
17.7.1 COMPANY SNAPSHOT
17.7.2 REVENUE ANALYSIS
17.7.3 PRODUCT PORTFOLIO
17.7.4 RECENT DEVELOPMENT
17.8 AWARE, INC.
17.8.1 COMPANY SNAPSHOT
17.8.2 REVENUE ANALYSIS
17.8.3 PRODUCT PORTFOLIO
17.8.4 RECENT DEVELOPMENTS
17.9 AXIS COMMUNICATIONS AB
17.9.1 COMPANY SNAPSHOT
17.9.2 REVENUE ANALYSIS
17.9.3 PRODUCT PORTFOLIO
17.9.4 RECENT DEVELOPMENT
17.1 BOSCH SICHERHEITSSYSTEME GMBH
17.10.1 COMPANY SNAPSHOT
17.10.2 REVENUE ANALYSIS
17.10.3 PRODUCTS PORTFOLIO
17.10.4 RECENT DEVELOPMENT
17.11 CHECK POINT SOFTWARE TECHNOLOGIES LTD.
17.11.1 COMPANY SNAPSHOT
17.11.2 REVENUE ANALYSIS
17.11.3 PRODUCTS PORTFOLIO
17.11.4 RECENT DEVELOPMENTS
17.12 CISCO SYSTEMS, INC.
17.12.1 COMPANY SNAPSHOT
17.12.2 REVENUE ANALYSIS
17.12.3 PRODUCTS PORTFOLIO
17.12.4 RECENT DEVELOPMENTS
17.13 HEXAGON AB
17.13.1 COMPANY SNAPSHOT
17.13.2 REVENUE ANALYSIS
17.13.3 OFFERING PORTFOLIO
17.13.4 RECENT DEVELOPMENT
17.14 HID GLOBAL CORPORATION
17.14.1 COMPANY SNAPSHOT
17.14.2 PRODUCT PORTFOLIO
17.14.3 RECENT DEVELOPMENT
17.15 IBM CORPORATION
17.15.1 COMPANY SNAPSHOT
17.15.2 REVENUE ANALYSIS
17.15.3 PRODUCTS PORTFOLIO
17.15.4 RECENT DEVELOPMENTS
17.16 JOHNSON CONTROL
17.16.1 COMPANY SNAPSHOT
17.16.2 REVENUE ANALYSIS
17.16.3 PRODUCTS PORTFOLIO
17.16.4 RECENT DEVELOPMENTS
17.17 JUNIPER NETWORKS, INC.
17.17.1 COMPANY SNAPSHOT
17.17.2 REVENUE ANALYSIS
17.17.3 PRODUCTS PORTFOLIO
17.17.4 RECENT DEVELOPMENTS
17.18 MCAFEE, LLC
17.18.1 COMPANY SNAPSHOT
17.18.2 REVENUE ANALYSIS
17.18.3 PRODUCTS PORTFOLIO
17.18.4 RECENT DEVELOPMENTS
17.19 MICRO FOCUS
17.19.1 COMPANY SNAPSHOT
17.19.2 REVENUE ANALYSIS
17.19.3 PRODUCT PORTFOLIO
17.19.4 RECENT DEVELOPMENT
17.2 MICROSOFT
17.20.1 COMPANY SNAPSHOT
17.20.2 REVENUE ANALYSIS
17.20.3 PRODUCT PORTFOLIO
17.20.4 RECENT DEVELOPMENTS
17.21 ORACLE
17.21.1 COMPANY SNAPSHOT
17.21.2 REVENUE ANALYSIS
17.21.3 SERVICE CATEGORY
17.21.4 RECENT DEVELOPMENT
17.22 PELCO CORPORATIONS
17.22.1 COMPANY SNAPSHOT
17.22.2 REVENUE ANALYSIS
17.22.3 PRODUCTS PORTFOLIO
17.22.4 RECENT DEVELOPMENTS
17.23 RAPID7
17.23.1 COMPANY SNAPSHOT
17.23.2 REVENUE ANALYSIS
17.23.3 PRODUCT PORTFOLIO
17.23.4 RECENT DEVELOPMENTS
17.24 SPLUNK INC.
17.24.1 COMPANY SNAPSHOT
17.24.2 REVENUE ANALYSIS
17.24.3 PRODUCTS PORTFOLIO
17.24.4 RECENT DEVELOPMENT
17.25 TREND MICRO INCORPORATED
17.25.1 COMPANY SNAPSHOT
17.25.2 REVENUE ANALYSIS
17.25.3 PRODUCTS PORTFOLIO
17.25.4 RECENT DEVELOPMENTS
18 QUESTIONNAIRE
19 RELATED REPORTS
표 목록
TABLE 1 LIST OF LOCAL CYBER SECURITY PLAYERS
TABLE 2 LIST OF LOCAL PHYSICAL SECURITY PLAYERS
TABLE 3 IRAQ CYBER SECURITY MARKET, BY OFFERING, 2020-2029 (USD MILLION)
TABLE 4 IRAQ SERVICES IN CYBER SECURITY MARKET, BY TYPE, 2020-2029 (USD MILLION)
TABLE 5 IRAQ SOLUTIONS/SOFTWARE IN CYBER SECURITY MARKET, BY TYPE, 2020-2029 (USD MILLION)
TABLE 6 IRAQ PHYSICAL SECURITY MARKET, BY COMPONENT, 2020-2029 (USD MILLION)
TABLE 7 IRAQ HARWARE IN PHYSICAL SECURITY MARKET, BY TYPE, 2020-2029 (USD MILLION)
TABLE 8 IRAQ VIDEO SURVEILLANCE SYSTEM IN HARDWRAE PHYSICAL SECURITY MARKET, BY TYPE, 2020-2029 (USD MILLION)
TABLE 9 IRAQ CAMERAS IN VIDEO SURVEILLANCE SYSTEM PHYSICAL SECURITY MARKET, BY TYPE, 2020-2029 (USD MILLION)
TABLE 10 IRAQ RECORDERS IN VIDEO SURVEILLANCE SYSTEM PHYSICAL SECURITY MARKET, BY TYPE, 2020-2029 (USD MILLION)
TABLE 11 IRAQ PHYSICAL ACCESS CONTROL SYSTEM IN PHYSICAL SECURITY MARKET, BY TYPE, 2020-2029 (USD MILLION)
TABLE 12 IRAQ BIOMETRICS IN PHYSICAL ACCESS CONTROL SYSTEM PHYSICAL SECURITY MARKET, BY TYPE, 2020-2029 (USD MILLION)
TABLE 13 IRAQ LOCKS IN PHYSICAL ACCESS CONTROL SYSTEM PHYSICAL SECURITY MARKET, BY TYPE, 2020-2029 (USD MILLION)
TABLE 14 IRAQ ELECTRONIC LOCKS IN LOCKS PHYSICAL SECURITY MARKET, BY TYPE, 2020-2029 (USD MILLION)
TABLE 15 IRAQ SERVICES IN PHYSICAL SECURITY MARKET, BY TYPE, 2020-2029 (USD MILLION)
TABLE 16 IRAQ MANAGED SERVICES IN SERVICES PHYSICAL SECURITY MARKET, BY TYPE, 2020-2029 (USD MILLION)
TABLE 17 IRAQ PROFESSIONAL SERVICES IN SERVICES PHYSICAL SECURITY MARKET, BY TYPE, 2020-2029 (USD MILLION)
TABLE 18 IRAQ SOFTWARE IN PHYSICAL SECURITY MARKET, BY TYPE, 2020-2029 (USD MILLION)
TABLE 19 IRAQ PHYSICAL SECURITY MARKET, BY AUTHENTICATION, 2020-2029 (USD MILLION)
TABLE 20 IRAQ CYBER SECURITY MARKET, BY APPLICATION, 2020-2029 (USD MILLION)
TABLE 21 IRAQ CYBER SECURITY MARKET, BY SECURITY TYPE, 2020-2029 (USD MILLION)
TABLE 22 IRAQ PHYSICAL SECURITY MARKET, BY DEPLOYMENT MODEL, 2020-2029 (USD MILLION)
TABLE 23 IRAQ CYBER SECURITY MARKET, BY DEPLOYMENT MODEL, 2020-2029 (USD MILLION)
TABLE 24 IRAQ PHYSICAL SECURITY MARKET, BY ENTERPRISE SIZE, 2020-2029 (USD MILLION)
TABLE 25 IRAQ CYBER SECURITY MARKET, BY ENTERPRISE SIZE, 2020-2029 (USD MILLION)
TABLE 26 IRAQ LARGE SIZED ENTERPRISES IN PHYSICAL SECURITY MARKET, BY DEPLOYMENT MODEL, 2020-2029 (USD MILLION)
TABLE 27 IRAQ LARGE SIZED ENTERPRISES IN CYBER SECURITY MARKET, BY DEPLOYMENT MODEL, 2020-2029 (USD MILLION)
TABLE 28 IRAQ SMALL AND MEDIUM-SIZED ENTERPRISES IN PHYSICAL SECURITY MARKET, BY DEPLOYMENT MODEL, 2020-2029 (USD MILLION)
TABLE 29 IRAQ SMALL AND MEDIUM-SIZED ENTERPRISES IN CYBER SECURITY MARKET, BY DEPLOYMENT MODEL, 2020-2029 (USD MILLION)
TABLE 30 IRAQ PHYSICAL SECURITY MARKET, BY END USER, 2020-2029 (USD MILLION)
TABLE 31 IRAQ CYBER SECURITY MARKET, BY END USER, 2020-2029 (USD MILLION)
TABLE 32 IRAQ COMMERCIAL IN PHYSICAL SECURITY MARKET, BY TYPE, 2020-2029 (USD MILLION)
TABLE 33 IRAQ COMMERCIAL IN CYBER SECURITY MARKET, BY TYPE, 2020-2029 (USD MILLION)
TABLE 34 IRAQ INDUSTRIAL IN PHYSICAL SECURITY MARKET, BY TYPE 2020-2029 (USD MILLION)
TABLE 35 IRAQ INDUSTRIAL IN CYBER SECURITY MARKET, BY TYPE 2020-2029 (USD MILLION)
TABLE 36 IRAQ RESIDENTIAL IN PHYSICAL SECURITY MARKET, BY TYPE 2020-2029 (USD MILLION)
TABLE 37 IRAQ RESIDENTIAL IN CYBER SECURITY MARKET, BY TYPE 2020-2029 (USD MILLION)
그림 목록
FIGURE 1 IRAQ PHYSICAL AND CYBER SECURITY MARKET: SEGMENTATION
FIGURE 2 IRAQ PHYSICAL AND CYBER SECURITY MARKET: DATA TRIANGULATION
FIGURE 3 IRAQ PHYSICAL AND CYBER SECURITY MARKET: DROC ANALYSIS
FIGURE 4 IRAQ PHYSICAL SECURITY MARKET: REGIONAL VS COUNTRY ANALYSIS
FIGURE 5 IRAQ CYBER SECURITY MARKET: REGIONAL VS COUNTRY ANALYSIS
FIGURE 6 IRAQ PHYSICAL AND CYBER SECURITY MARKET: COMPANY RESEARCH ANALYSIS
FIGURE 7 IRAQ PHYSICAL AND CYBER SECURITY MARKET: INTERVIEW DEMOGRAPHICS
FIGURE 8 IRAQ PHYSICAL SECURITY MARKET: DBMR MARKET POSITION GRID
FIGURE 9 IRAQ CYBER SECURITY MARKET: DBMR MARKET POSITION GRID
FIGURE 10 IRAQ CYBER SECURITY MARKET: VENDOR SHARE ANALYSIS
FIGURE 11 IRAQ PHYSICAL SECURITY MARKET: VENDOR SHARE ANALYSIS
FIGURE 12 IRAQ PHYSICAL SECURITY MARKET: MARKET END USER COVERAGE GRID
FIGURE 13 IRAQ CYBER SECURITY MARKET: MARKET END USER COVERAGE GRID
FIGURE 14 IRAQ CYBER SECURITY MARKET: SEGMENTATION
FIGURE 15 IRAQ PHYSICAL SECURITY MARKET: SEGMENTATION
FIGURE 16 AN INCREASE IN CLOUD SERVICES CYBER AND PHYSICAL SECURITY SOLUTIONS IS EXPECTED TO DRIVE IRAQ PHYSICAL SECURITY MARKET IN THE FORECAST PERIOD OF 2022 TO 2029
FIGURE 17 EMERGENCE OF SMART INTERCONNECTED BUILDING/HOME IS EXPECTED TO DRIVE IRAQ CYBER SECURITY MARKET IN THE FORECAST PERIOD OF 2022 TO 2029
FIGURE 18 SERVICES SEGMENT IS EXPECTED TO ACCOUNT FOR THE LARGEST SHARE OF IRAQ CYBER SECURITY MARKET IN THE FORECASTED PERIOD OF 2022 & 2029
FIGURE 19 HARDWARE SEGMENT IS EXPECTED TO ACCOUNT FOR THE LARGEST SHARE OF IRAQ PHYSICAL SECURITY MARKET IN THE FORECASTED PERIOD OF 2022 & 2029
FIGURE 20 VALUE CHAIN FOR PHYSICAL AND CYBER SECURITY MARKET
FIGURE 21 PORTERS FIVE FORCES ANALYSIS FOR PHYSICAL AND CYBER SECURITY MARKET
FIGURE 22 PESTLE ANALYSIS FOR PHYSICAL AND CYBER SECURITY MARKET
FIGURE 23 DRIVERS, RESTRAINTS, OPPORTUNITIES, AND CHALLENGES OF IRAQ PHYSICAL AND CYBER SECURITY MARKET
FIGURE 24 KEY STATS OF REMOTE WORK
FIGURE 25 GROWING PREVALENCE OF BIOMETRIC SOLUTIONS AMONG CONSUMER
FIGURE 26 TECHNOLOGY AMALGAMATION IN SMART HOME/ BUILDINGS
FIGURE 27 IMPACT OF CYBER SECURITY THREAT
FIGURE 28 PHISHING ATTACKS REPORTED IN RESPECTIVE COUNTRIES IN Q2, 2021
FIGURE 29 IRAQ CYBER SECURITY MARKET, BY OFFERING, 2021
FIGURE 30 IRAQ PHYSICAL SECURITY MARKET, BY COMPONENT, 2021
FIGURE 31 IRAQ PHYSICAL SECURITY MARKET, BY AUTHENTICATION, 2021
FIGURE 32 IRAQ CYBER SECURITY MARKET: BY APPLICATION, 2021
FIGURE 33 IRAQ CYBER SECURITY MARKET: BY SECURITY TYPE, 2021
FIGURE 34 IRAQ PHYSICAL SECURITY MARKET, BY DEPLOYMENT MODEL, 2021
FIGURE 35 IRAQ CYBER SECURITY MARKET, BY DEPLOYMENT MODEL, 2021
FIGURE 36 IRAQ PHYSICAL SECURITY MARKET, BY ENTERPRISE SIZE, 2021
FIGURE 37 IRAQ CYBER SECURITY MARKET, BY ENTERPRISE SIZE, 2021
FIGURE 38 IRAQ PHYSICAL SECURITY MARKET: BY END USER, 2021
FIGURE 39 IRAQ CYBER SECURITY MARKET: BY END USER, 2021
FIGURE 40 IRAQ CYBER SECURITY MARKET: COMPANY SHARE 2021 (%)
FIGURE 41 IRAQ PHYSICAL SECURITY MARKET: COMPANY SHARE 2021 (%)
연구 방법론
데이터 수집 및 기준 연도 분석은 대규모 샘플 크기의 데이터 수집 모듈을 사용하여 수행됩니다. 이 단계에는 다양한 소스와 전략을 통해 시장 정보 또는 관련 데이터를 얻는 것이 포함됩니다. 여기에는 과거에 수집한 모든 데이터를 미리 검토하고 계획하는 것이 포함됩니다. 또한 다양한 정보 소스에서 발견되는 정보 불일치를 검토하는 것도 포함됩니다. 시장 데이터는 시장 통계 및 일관된 모델을 사용하여 분석하고 추정합니다. 또한 시장 점유율 분석 및 주요 추세 분석은 시장 보고서의 주요 성공 요인입니다. 자세한 내용은 분석가에게 전화를 요청하거나 문의 사항을 드롭하세요.
DBMR 연구팀에서 사용하는 주요 연구 방법론은 데이터 마이닝, 시장에 대한 데이터 변수의 영향 분석 및 주요(산업 전문가) 검증을 포함하는 데이터 삼각 측량입니다. 데이터 모델에는 공급업체 포지셔닝 그리드, 시장 타임라인 분석, 시장 개요 및 가이드, 회사 포지셔닝 그리드, 특허 분석, 가격 분석, 회사 시장 점유율 분석, 측정 기준, 글로벌 대 지역 및 공급업체 점유율 분석이 포함됩니다. 연구 방법론에 대해 자세히 알아보려면 문의를 통해 업계 전문가에게 문의하세요.
사용자 정의 가능
Data Bridge Market Research는 고급 형성 연구 분야의 선두 주자입니다. 저희는 기존 및 신규 고객에게 목표에 맞는 데이터와 분석을 제공하는 데 자부심을 느낍니다. 보고서는 추가 국가에 대한 시장 이해(국가 목록 요청), 임상 시험 결과 데이터, 문헌 검토, 재생 시장 및 제품 기반 분석을 포함하도록 사용자 정의할 수 있습니다. 기술 기반 분석에서 시장 포트폴리오 전략에 이르기까지 타겟 경쟁업체의 시장 분석을 분석할 수 있습니다. 귀하가 원하는 형식과 데이터 스타일로 필요한 만큼 많은 경쟁자를 추가할 수 있습니다. 저희 분석가 팀은 또한 원시 엑셀 파일 피벗 테이블(팩트북)로 데이터를 제공하거나 보고서에서 사용 가능한 데이터 세트에서 프레젠테이션을 만드는 데 도움을 줄 수 있습니다.