Mercado de ciberseguridad de Turquía, por oferta (servicios y soluciones/software), aplicación (gestión de identidad y acceso, oferta de servicios de seguridad y privacidad de datos, gobernanza, riesgo y cumplimiento, oferta de servicios de gestión unificada de vulnerabilidades y otros), tipo de seguridad (seguridad de infraestructura, seguridad de red , seguridad de aplicaciones, seguridad en la nube, seguridad de endpoints y otros), modelo de implementación (nube y local), tamaño de la empresa (grandes empresas y pequeñas y medianas empresas), usuario final (industrial, comercial, gubernamental y residencial): tendencias de la industria y pronóstico hasta 2029.
Análisis y perspectivas del mercado de ciberseguridad de Turquía
La ciberseguridad protege los sistemas conectados a Internet, como hardware, software y datos, de las ciberamenazas y las infracciones. El aumento de los servicios en la nube y las soluciones de ciberseguridad está impulsando el mercado. Sin embargo, el aumento de las amenazas de ciberseguridad y el ransomware en las soluciones de ciberseguridad pueden frenar el crecimiento.
La demanda de ciberseguridad está creciendo y seguirá creciendo en el futuro. Data Bridge Market Research analiza que el mercado de ciberseguridad de Turquía crecerá a una tasa compuesta anual del 7,3 % entre 2022 y 2029.
|
Métrica del informe |
Detalles |
|
Período de pronóstico |
2022 a 2029 |
|
Año base |
2021 |
|
Años históricos |
2020 (Personalizable para 2019 - 2014) |
|
Unidades cuantitativas |
Valores en Millones |
|
Segmentos cubiertos |
Por oferta (servicios y soluciones/software), aplicación (gestión de identidad y acceso, oferta de servicios de seguridad y privacidad de datos, gestión de riesgos y cumplimiento normativo, oferta de servicios de gestión unificada de vulnerabilidades y otros), tipo de seguridad (seguridad de infraestructura, seguridad de red, seguridad de aplicaciones, seguridad en la nube, seguridad de endpoints y otros), modelo de implementación (nube y local), tamaño de la empresa (grandes empresas y pequeñas y medianas empresas), usuario final (industrial, comercial, gubernamental y residencial) |
|
Países cubiertos |
Pavo |
|
Actores del mercado cubiertos |
BAE Systems, Microsoft, McAfee, LLC, Thales, Rapid7, Trend Micro Incorporated, Accenture, Cisco Systems, Inc., IBM Corporation, Oracle, Splunk Inc., Check Point Software Technologies Ltd., Palo Alto Networks, Fortinet, Inc., Juniper Networks, Inc., Micro Focus y Johnson Controls, entre otros. |
Definición de mercado
La ciberseguridad protege los sistemas conectados a Internet, como hardware, software y datos, contra amenazas y violaciones cibernéticas. Tanto las personas como las empresas utilizan esta práctica para protegerse contra el acceso no autorizado a los centros de datos y otros sistemas inteligentes.
Dinámica del mercado de ciberseguridad en Turquía
En esta sección se aborda la comprensión de los factores impulsores, las ventajas, las oportunidades, las limitaciones y los desafíos del mercado. Todo esto se analiza en detalle a continuación:
Conductores
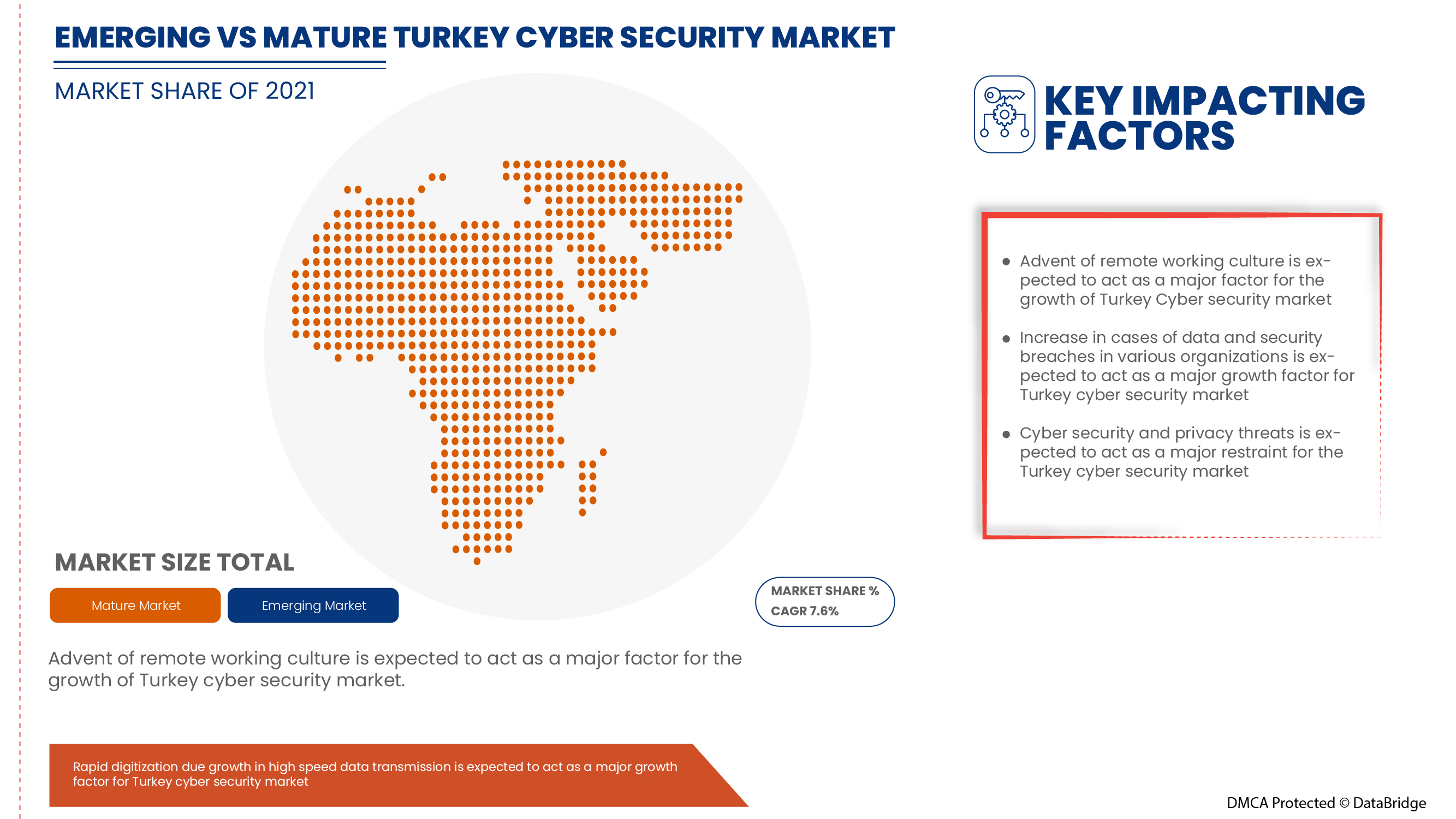
- El advenimiento de la cultura del trabajo remoto
El trabajo remoto está aumentando debido a la reciente pandemia, en la que los empleados se vieron obligados a trabajar de forma remota en sus respectivas ubicaciones. Hace unas décadas, la capacidad de trabajar fuera de una oficina corporativa no se consideraba viable porque se suponía que sería menos eficiente. El trabajo remoto recién ahora se está volviendo común debido a los avances tecnológicos, como la fuerte conectividad a Internet, que podría servir de base a soluciones y otros.
- Aumento de las soluciones de seguridad física y cibernética en servicios en la nube
La tecnología en la nube es una tecnología en línea vital que se utiliza en todo el mundo. La tecnología en la nube permite a los usuarios acceder a almacenamiento, archivos, software y servidores mediante dispositivos conectados a Internet. También significa tener la capacidad de almacenar y acceder a datos y programas a través de Internet. A diferencia de los métodos tradicionales de hardware y software, las tecnologías en la nube pueden ayudar a las empresas a mantenerse a la vanguardia de la tecnología sin gastar mucho en métodos tradicionales.

Oportunidad
-
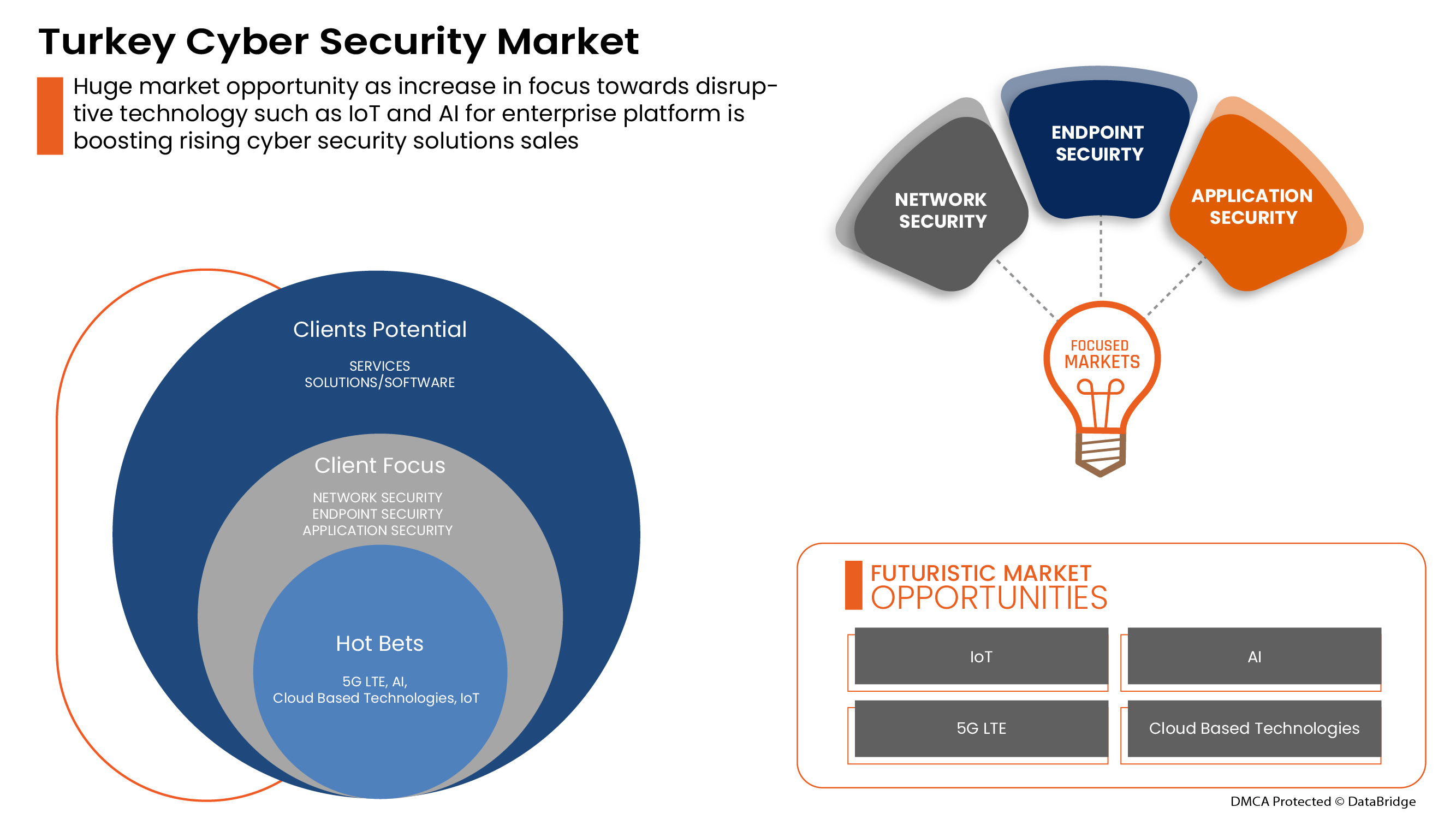
Aumentan las alianzas estratégicas y las adquisiciones entre organizaciones para el sistema de seguridad física y cibernética
La coordinación e inversión en proyectos es esencial para lograr mejoras sostenidas en el mercado de la seguridad física y cibernética. Debido a esto, el gobierno y otras organizaciones privadas están esforzándose a través de asociaciones y adquisiciones, acelerando así el crecimiento de las industrias. Esto ayuda a generar conciencia y ganancias para la organización, creando así un espacio para una nueva invención en la industria. Además, a través de asociaciones, la empresa puede invertir más en tecnologías avanzadas para proporcionar servicios y soluciones de seguridad física y cibernética más seguros y confiables.
Restricción/Desafío
- Aumento de las amenazas de ciberseguridad y ransomware en soluciones de seguridad física y cibernética
Debido al COVID-19, los problemas de ciberdelincuencia y ciberseguridad aumentaron un 600% en 2020. Las fallas en la seguridad de la red son una debilidad que los piratas informáticos aprovechan para realizar acciones no autorizadas dentro de un sistema. Según Purple Sec LLC, en 2018, las variantes de malware para dispositivos móviles aumentaron un 54%, de las cuales el 98% del malware para dispositivos móviles se dirige a dispositivos Android. Se estima que el 25% de las empresas han sido víctimas de cryptojacking. Varias empresas también incluyen la industria de la seguridad.
Impacto de la COVID-19 en el mercado de ciberseguridad de Turquía
El COVID-19 ha afectado positivamente al mercado de ciberseguridad de Turquía. Debido al COVID-19, los problemas de ciberdelincuencia y ciberseguridad aumentaron un 600% en 2020. Las fallas en la seguridad de la red son una debilidad que los piratas informáticos explotan para realizar acciones no autorizadas dentro de un sistema. Según Purple Sec LLC, en 2018, las variantes de malware móvil para dispositivos móviles aumentaron un 54%, de las cuales el 98% del malware móvil se dirige a dispositivos Android. Se estima que el 25% de las empresas han sido víctimas de cryptojacking. Varias empresas también incluyen la industria de la seguridad.
Desarrollo reciente
- En agosto de 2022, Fortinet, Inc. anunció una asociación con Comcast Business para ofrecer a las empresas un nuevo conjunto de soluciones de borde de servicio de acceso seguro (SASE) y borde de servicio de seguridad (SSE) para ayudar a las empresas a proteger sus fuerzas de trabajo distribuidas.
- En mayo de 2022, Cisco Systems, Inc. lanzó una herramienta avanzada de evaluación de la ciberseguridad. El objetivo principal detrás del lanzamiento de las soluciones era permitir que las pequeñas y medianas empresas (PYMES) comprendan mejor su postura de seguridad general.
Alcance del mercado de ciberseguridad en Turquía
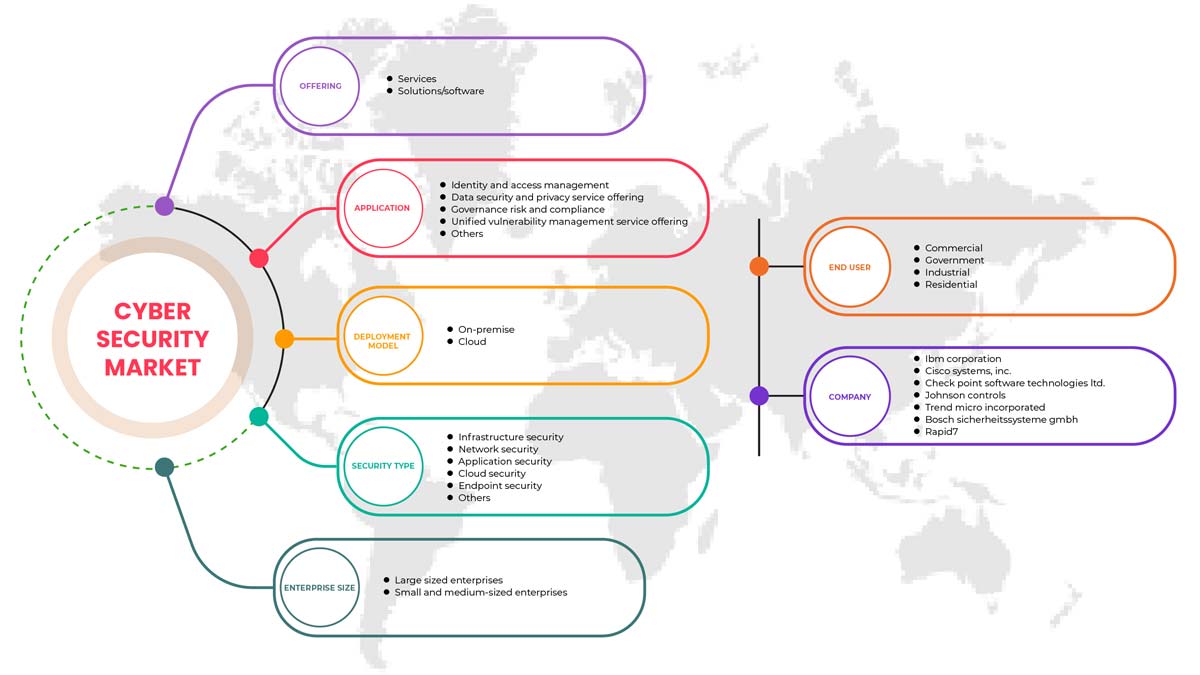
El mercado de la seguridad cibernética está segmentado en función de la oferta, la aplicación, el tipo de seguridad, el modelo de implementación, el tamaño de la empresa y el usuario final. El crecimiento entre estos segmentos le ayudará a analizar los segmentos de crecimiento reducido de las industrias y brindará a los usuarios una valiosa descripción general del mercado y conocimientos del mercado para ayudarlos a tomar decisiones estratégicas para identificar las principales aplicaciones del mercado.
Ofrenda
- Servicios
- Soluciones/software
Sobre la base de la oferta, el mercado de ciberseguridad de Egipto está segmentado en servicios y soluciones/software.
Solicitud
- Gestión de identidad y acceso
- Oferta de servicios de seguridad y privacidad de datos
- Riesgo de gobernanza y cumplimiento
- Oferta de servicios de gestión de vulnerabilidades unificada
- Otros
Sobre la base de la aplicación, el mercado de seguridad cibernética de Egipto está segmentado en gestión de identidad y acceso, oferta de servicios de seguridad y privacidad de datos, gobernanza, riesgo y cumplimiento, oferta de servicios de gestión unificada de vulnerabilidades y otros.
Tipo de seguridad
- Seguridad de la infraestructura
- Seguridad de la red
- Seguridad de la aplicación
- Seguridad en la nube
- Seguridad de puntos finales
- Otros
Sobre la base del tipo de seguridad, el mercado de ciberseguridad de Egipto está segmentado en seguridad de infraestructura, seguridad de red, seguridad de aplicaciones, seguridad en la nube, seguridad de puntos finales y otros.
Modelo de implementación
- Nube
- En las instalaciones
Sobre la base del modelo de implementación, el mercado de ciberseguridad de Egipto está segmentado en nube y local.
Tamaño de la empresa
- Empresas de gran tamaño
- Pequeñas y medianas empresas
Sobre la base del tamaño de la empresa, el mercado de ciberseguridad de Egipto está segmentado en empresas de gran tamaño y pequeñas y medianas empresas.
Usuario final
- Industrial
- Comercial
- Gobierno
- Residencial
Sobre la base del modelo de implementación, el mercado de ciberseguridad de Egipto está segmentado en industrial, comercial, gubernamental y residencial.
Análisis y perspectivas regionales del mercado de ciberseguridad de Turquía
Se analiza el mercado de ciberseguridad de Turquía y se proporcionan información y tendencias sobre el tamaño del mercado por oferta, aplicación, tipo de seguridad, modelo de implementación, tamaño de la empresa y usuario final.
La sección de países del informe también proporciona factores de impacto de mercado individuales y cambios en las regulaciones en el mercado a nivel nacional que afectan las tendencias actuales y futuras del mercado. Los puntos de datos como nuevas ventas, ventas de reemplazo, demografía del país, epidemiología de enfermedades y aranceles de importación y exportación son algunos de los indicadores importantes utilizados para pronosticar el escenario del mercado para países individuales. Además, se consideran la presencia y disponibilidad de marcas globales y los desafíos que enfrentan debido a la competencia sustancial o escasa del impacto de las marcas locales y nacionales en los canales de venta al proporcionar un análisis de pronóstico de los datos del país.
Análisis del panorama competitivo y de la cuota de mercado de la ciberseguridad en Turquía
El panorama competitivo del mercado de ciberseguridad de Turquía ofrece detalles por competidor. Los componentes incluidos son la descripción general de la empresa, las finanzas de la empresa, los ingresos generados, el potencial de mercado, la inversión en investigación y desarrollo, las nuevas iniciativas de mercado, la presencia global, los sitios e instalaciones de producción, las capacidades de producción, las fortalezas y debilidades de la empresa, el lanzamiento de productos, la amplitud y la variedad de productos, y el dominio de las aplicaciones. Los puntos de datos anteriores solo están relacionados con el enfoque de las empresas en el mercado de ciberseguridad de Turquía.
Algunos de los principales actores clave en el mercado de ciberseguridad de Turquía son BAE Systems, Microsoft, McAfee, LLC, Thales, Rapid7, Trend Micro Incorporated, Accenture, Cisco Systems, Inc., IBM Corporation, Oracle, Splunk Inc., Check Point Software Technologies Ltd., Palo Alto Networks, Fortinet, Inc., Juniper Networks, Inc., Micro Focus y Johnson Controls, entre otros.
SKU-
Obtenga acceso en línea al informe sobre la primera nube de inteligencia de mercado del mundo
- Panel de análisis de datos interactivo
- Panel de análisis de empresas para oportunidades con alto potencial de crecimiento
- Acceso de analista de investigación para personalización y consultas
- Análisis de la competencia con panel interactivo
- Últimas noticias, actualizaciones y análisis de tendencias
- Aproveche el poder del análisis de referencia para un seguimiento integral de la competencia
Tabla de contenido
1 INTRODUCTION
1.1 OBJECTIVES OF THE STUDY
1.2 MARKET DEFINITION
1.3 OVERVIEW OF TURKEY PHYSICAL AND CYBER SECURITY MARKET
1.4 CURRENCY AND PRICING
1.5 LIMITATIONS
1.6 MARKETS COVERED
2 MARKET SEGMENTATION
2.1 MARKETS COVERED
2.2 GEOGRAPHICAL SCOPE
2.3 YEARS CONSIDERED FOR THE STUDY
2.4 DBMR TRIPOD DATA VALIDATION MODEL
2.5 PRIMARY INTERVIEWS WITH KEY OPINION LEADERS
2.6 DBMR MARKET POSITION GRID
2.7 VENDOR SHARE ANALYSIS
2.8 MARKET END USER COVERAGE GRID
2.9 MULTIVARIATE MODELING
2.1 COMPONENT TIMELINE CURVE
2.11 OFFERING TIMELINE CURVE
2.12 SECONDARY SOURCES
2.13 ASSUMPTIONS
3 EXECUTIVE SUMMARY
4 PREMIUM INSIGHTS
4.1 INVESTMENT POLICY
4.1 CASE STUDY
4.1.1 SECURE SOFTWARE DEVELOPMENT INFRASTRUCTURE
4.1.2 SOC-AS-A-PLATFORM (SOCAAP)
4.1.3 RANSOMWARE & FORENSICS ANALYSIS
4.1.4 WISCONSIN'S DEER DISTRICT SECURITY PLAN
4.1.5 LICENSE PLATE READERS IN SCHOOLS
4.1.6 K-12 SCHOOLS
4.2 VALUE CHAIN ANALYSIS
4.3 PORTERS FIVE FORCES
4.4 PESTLE ANALYSIS
4.5 TECHNOLOGICAL LANDSCAPE
4.5.1 AI AND MACHINE LEARNING
4.5.2 IOT
4.5.3 BLOCKCHAIN
4.6 REGULATORY STANDARDS
4.6.1 CYBER SECURITY
4.6.2 PHYSICAL SECURITY
4.7 LOCAL PLAYERS LIST
5 MARKET OVERVIEW
5.1 DRIVERS
5.1.1 ADVENT OF REMOTE WORKING CULTURE
5.1.2 INCREASE IN CLOUD SERVICES CYBER AND PHYSICAL SECURITY SOLUTIONS
5.1.3 GROWING IMPORTANCE OF PHYSICAL BIOMETRIC SOLUTIONS ACROSS ALL SECTORS
5.1.4 EMERGENCE OF SMART INTERCONNECTED BUILDING/HOME
5.2 RESTRAINTS
5.2.1 RISE IN CYBER SECURITY THREAT AND RANSOMWARE IN PHYSICAL AND CYBER SECURITY SOLUTIONS
5.3 OPPORTUNITIES
5.3.1 RISING STRATEGIC PARTNERSHIP AND ACQUISITION AMONG ORGANIZATIONS FOR PHYSICAL AND CYBER SECURITY SYSTEM
5.3.2 EMERGENCE OF VARIOUS DISRUPTIVE TECHNOLOGY SUCH AS IOT AND AI FOR VARIOUS INDUSTRIES
5.3.3 INCREASE IN CASES OF DATA AND SECURITY BREACHES IN VARIOUS ORGANIZATIONS
5.4 CHALLENGES
5.4.1 LACK OF PROFESSIONAL EXPERTISE FOR CYBER SECURITY SYSTEMS
5.4.2 COMPLEXITY ASSOCIATED WITH THE INTEGRATION OF VARIOUS PHYSICAL SECURITY SYSTEMS
6 TURKEY CYBER SECURITY MARKET, BY OFFERING
6.1 OVERVIEW
6.2 SERVICES
6.3 SOLUTIONS/SOFTWARE
7 TURKEY PHYSICAL SECURITY MARKET, BY COMPONENT
7.1 OVERVIEW
7.2 HARDWARE
7.2.1 VIDEO SURVEILLANCE SYSTEM
7.2.1.1 CAMERAS
7.2.1.2 RECORDERS
7.2.2 PHYSICAL ACCESS CONTROL SYSTEM
7.2.2.1 BIOMETRICS
7.2.2.2 LOCKS
7.2.2.2.1 ELECTRONIC LOCKS
7.3 SERVICES
7.3.1 MANAGED SERVICES
7.3.2 PROFESSIONAL SERVICES
7.4 SOFTWARE
8 TURKEY PHYSICAL SECURITY MARKET, BY AUTHENTICATION
8.1 OVERVIEW
8.2 SINGLE- FACTOR AUTHENTICATION
8.3 TWO- FACTOR AUTHENTICATION
8.4 THREE- FACTOR AUTHENTICATION
9 TURKEY CYBER SECURITY MARKET, BY APPLICATION
9.1 OVERVIEW
9.2 IDENTITY AND ACCESS MANAGEMENT
9.3 DATA SECURITY AND PRIVACY SERVICE OFFERING
9.4 GOVERNANCE RISK AND COMPLIANCE
9.5 UNIFIED VULNERABILITY MANAGEMENT SERVICE OFFERING
9.6 OTHERS
10 TURKEY CYBER SECURITY MARKET, BY SECURITY TYPE
10.1 OVERVIEW
10.2 INFRASTRUCTURE SECURITY
10.3 NETWORK SECURITY
10.4 APPLICATION SECURITY
10.5 CLOUD SECURITY
10.6 ENDPOINT SECURITY
10.7 OTHERS
11 TURKEY PHYSICAL AND CYBER SECURITY MARKET, BY DEPLOYMENT MODEL
11.1 OVERVIEW
11.2 ON-PREMISE
11.3 CLOUD
12 TURKEY PHYSICAL AND CYBER SECURITY MARKET, BY ENTERPRISE SIZE
12.1 OVERVIEW
12.2 LARGE SIZED ENTERPRISES
12.3 SMALL AND MEDIUM-SIZED ENTERPRISES
13 TURKEY PHYSICAL AND CYBER SECURITY MARKET, BY END USER
13.1 OVERVIEW
13.2 COMMERCIAL
13.3 GOVERNMENT
13.4 INDUSTRIAL
13.5 RESIDENTIAL
14 TURKEY CYBER SECURITY MARKET, COMPANY LANDSCAPE
14.1 COMPANY SHARE ANALYSIS: TURKEY
15 TURKEY PHYSICAL SECURITY MARKET, COMPANY LANDSCAPE
15.1 COMPANY SHARE ANALYSIS: TURKEY
16 SWOT ANALYSIS
16.1 DBMR ANALYSIS
16.1.1 STRENGTH
16.1.2 WEAKNESS
16.1.3 THREATS
16.1.4 OPPORTUNITY
17 COMPANY PROFILE
17.1 THALES GROUP
17.1.1 COMPANY SNAPSHOT
17.1.2 REVENUE ANALYSIS
17.1.3 PRODUCTS PORTFOLIO
17.1.4 RECENT DEVELOPMENTS
17.2 HANGZHOU HIKVISION DIGITAL TECHNOLOGY CO., LTD
17.2.1 COMPANY SNAPSHOT
17.2.2 REVENUE ANALYSIS
17.2.3 PRODUCT PORTFOLIO
17.2.4 RECENT DEVELOPMENTS
17.3 ACCENTURE
17.3.1 COMPANY SNAPSHOT
17.3.2 REVENUE ANALYSIS
17.3.3 SERVICE PORTFOLIO
17.3.4 RECENT DEVELOPMENTS
17.4 IDEMIA
17.4.1 COMPANY SNAPSHOT
17.4.2 PRODUCT PORTFOLIO
17.4.3 RECENT DEVELOPMENTS
17.5 BAE SYSTEMS
17.5.1 COMPANY SNAPSHOT
17.5.2 REVENUE ANALYSIS
17.5.3 SERVICE PORTFOLIO
17.5.4 RECENT DEVELOPMENT
17.6 FORTINET, INC.
17.6.1 COMPANY SNAPSHOT
17.6.2 REVENUE ANALYSIS
17.6.3 SERVICE PORTFOLIO
17.6.4 RECENT DEVELOPMENTS
17.7 PALO ALTO NETWORKS
17.7.1 COMPANY SNAPSHOT
17.7.2 REVENUE ANALYSIS
17.7.3 PRODUCT PORTFOLIO
17.7.4 RECENT DEVELOPMENT
17.8 AWARE, INC.
17.8.1 COMPANY SNAPSHOT
17.8.2 REVENUE ANALYSIS
17.8.3 PRODUCT PORTFOLIO
17.8.4 RECENT DEVELOPMENTS
17.9 AXIS COMMUNICATIONS AB
17.9.1 COMPANY SNAPSHOT
17.9.2 REVENUE ANALYSIS
17.9.3 PRODUCT PORTFOLIO
17.9.4 RECENT DEVELOPMENT
17.1 BOSCH SICHERHEITSSYSTEME GMBH
17.10.1 COMPANY SNAPSHOT
17.10.2 REVENUE ANALYSIS
17.10.3 PRODUCTS PORTFOLIO
17.10.4 RECENT DEVELOPMENT
17.11 CHECK POINT SOFTWARE TECHNOLOGIES LTD.
17.11.1 COMPANY SNAPSHOT
17.11.2 REVENUE ANALYSIS
17.11.3 PRODUCTS PORTFOLIO
17.11.4 RECENT DEVELOPMENTS
17.12 CISCO SYSTEMS, INC.
17.12.1 COMPANY SNAPSHOT
17.12.2 REVENUE ANALYSIS
17.12.3 PRODUCTS PORTFOLIO
17.12.4 RECENT DEVELOPMENTS
17.13 HEXAGON AB
17.13.1 COMPANY SNAPSHOT
17.13.2 REVENUE ANALYSIS
17.13.3 OFFERING PORTFOLIO
17.13.4 RECENT DEVELOPMENT
17.14 HID GLOBAL CORPORATION
17.14.1 COMPANY SNAPSHOT
17.14.2 PRODUCT PORTFOLIO
17.14.3 RECENT DEVELOPMENT
17.15 IBM CORPORATION
17.15.1 COMPANY SNAPSHOT
17.15.2 REVENUE ANALYSIS
17.15.3 PRODUCTS PORTFOLIO
17.15.4 RECENT DEVELOPMENTS
17.16 JOHNSON CONTROL
17.16.1 COMPANY SNAPSHOT
17.16.2 REVENUE ANALYSIS
17.16.3 PRODUCTS PORTFOLIO
17.16.4 RECENT DEVELOPMENTS
17.17 JUNIPER NETWORKS, INC.
17.17.1 COMPANY SNAPSHOT
17.17.2 REVENUE ANALYSIS
17.17.3 PRODUCTS PORTFOLIO
17.17.4 RECENT DEVELOPMENTS
17.18 MCAFEE, LLC
17.18.1 COMPANY SNAPSHOT
17.18.2 REVENUE ANALYSIS
17.18.3 PRODUCTS PORTFOLIO
17.18.4 RECENT DEVELOPMENTS
17.19 MICRO FOCUS
17.19.1 COMPANY SNAPSHOT
17.19.2 REVENUE ANALYSIS
17.19.3 PRODUCT PORTFOLIO
17.19.4 RECENT DEVELOPMENT
17.2 MICROSOFT
17.20.1 COMPANY SNAPSHOT
17.20.2 REVENUE ANALYSIS
17.20.3 PRODUCT PORTFOLIO
17.20.4 RECENT DEVELOPMENTS
17.21 ORACLE
17.21.1 COMPANY SNAPSHOT
17.21.2 REVENUE ANALYSIS
17.21.3 SERVICE CATEGORY
17.21.4 RECENT DEVELOPMENT
17.22 PELCO CORPORATIONS
17.22.1 COMPANY SNAPSHOT
17.22.2 REVENUE ANALYSIS
17.22.3 PRODUCTS PORTFOLIO
17.22.4 RECENT DEVELOPMENTS
17.23 RAPID7
17.23.1 COMPANY SNAPSHOT
17.23.2 REVENUE ANALYSIS
17.23.3 PRODUCT PORTFOLIO
17.23.4 RECENT DEVELOPMENTS
17.24 SPLUNK INC.
17.24.1 COMPANY SNAPSHOT
17.24.2 REVENUE ANALYSIS
17.24.3 PRODUCTS PORTFOLIO
17.24.4 RECENT DEVELOPMENT
17.25 TREND MICRO INCORPORATED
17.25.1 COMPANY SNAPSHOT
17.25.2 REVENUE ANALYSIS
17.25.3 PRODUCTS PORTFOLIO
17.25.4 RECENT DEVELOPMENTS
18 QUESTIONNAIRE
19 RELATED REPORTS
Lista de Tablas
TABLE 1 LIST OF LOCAL CYBER SECURITY PLAYERS
TABLE 2 LIST OF LOCAL PHYSICAL SECURITY PLAYERS
TABLE 3 TURKEY CYBER SECURITY MARKET, BY OFFERING, 2020-2029 (USD MILLION)
TABLE 4 TURKEY SERVICES IN CYBER SECURITY MARKET, BY TYPE, 2020-2029 (USD MILLION)
TABLE 5 TURKEY SOLUTIONS/SOFTWARE IN CYBER SECURITY MARKET, BY TYPE, 2020-2029 (USD MILLION)
TABLE 6 TURKEY PHYSICAL SECURITY MARKET, BY COMPONENT, 2020-2029 (USD MILLION)
TABLE 7 TURKEY HARWARE IN PHYSICAL SECURITY MARKET, BY TYPE, 2020-2029 (USD MILLION)
TABLE 8 TURKEY VIDEO SURVEILLANCE SYSTEM IN HARDWRAE PHYSICAL SECURITY MARKET, BY TYPE, 2020-2029 (USD MILLION)
TABLE 9 TURKEY CAMERAS IN VIDEO SURVEILLANCE SYSTEM PHYSICAL SECURITY MARKET, BY TYPE, 2020-2029 (USD MILLION)
TABLE 10 TURKEY RECORDERS IN VIDEO SURVEILLANCE SYSTEM PHYSICAL SECURITY MARKET, BY TYPE, 2020-2029 (USD MILLION)
TABLE 11 TURKEY PHYSICAL ACCESS CONTROL SYSTEM IN PHYSICAL SECURITY MARKET, BY TYPE, 2020-2029 (USD MILLION)
TABLE 12 TURKEY BIOMETRICS IN PHYSICAL ACCESS CONTROL SYSTEM PHYSICAL SECURITY MARKET, BY TYPE, 2020-2029 (USD MILLION)
TABLE 13 TURKEY LOCKS IN PHYSICAL ACCESS CONTROL SYSTEM PHYSICAL SECURITY MARKET, BY TYPE, 2020-2029 (USD MILLION)
TABLE 14 TURKEY ELECTRONIC LOCKS IN LOCKS PHYSICAL SECURITY MARKET, BY TYPE, 2020-2029 (USD MILLION)
TABLE 15 TURKEY SERVICES IN PHYSICAL SECURITY MARKET, BY TYPE, 2020-2029 (USD MILLION)
TABLE 16 TURKEY MANAGED SERVICES IN SERVICES PHYSICAL SECURITY MARKET, BY TYPE, 2020-2029 (USD MILLION)
TABLE 17 TURKEY PROFESSIONAL SERVICES IN SERVICES PHYSICAL SECURITY MARKET, BY TYPE, 2020-2029 (USD MILLION)
TABLE 18 TURKEY SOFTWARE IN PHYSICAL SECURITY MARKET, BY TYPE, 2020-2029 (USD MILLION)
TABLE 19 TURKEY PHYSICAL SECURITY MARKET, BY AUTHENTICATION, 2020-2029 (USD MILLION)
TABLE 20 TURKEY CYBER SECURITY MARKET, BY APPLICATION, 2020-2029 (USD MILLION)
TABLE 21 TURKEY CYBER SECURITY MARKET, BY SECURITY TYPE, 2020-2029 (USD MILLION)
TABLE 22 TURKEY PHYSICAL SECURITY MARKET, BY DEPLOYMENT MODEL, 2020-2029 (USD MILLION)
TABLE 23 TURKEY CYBER SECURITY MARKET, BY DEPLOYMENT MODEL, 2020-2029 (USD MILLION)
TABLE 24 TURKEY PHYSICAL SECURITY MARKET, BY ENTERPRISE SIZE, 2020-2029 (USD MILLION)
TABLE 25 TURKEY CYBER SECURITY MARKET, BY ENTERPRISE SIZE, 2020-2029 (USD MILLION)
TABLE 26 TURKEY LARGE SIZED ENTERPRISES IN PHYSICAL SECURITY MARKET, BY DEPLOYMENT MODEL, 2020-2029 (USD MILLION)
TABLE 27 TURKEY LARGE SIZED ENTERPRISES IN CYBER SECURITY MARKET, BY DEPLOYMENT MODEL, 2020-2029 (USD MILLION)
TABLE 28 TURKEY SMALL AND MEDIUM-SIZED ENTERPRISES IN PHYSICAL SECURITY MARKET, BY DEPLOYMENT MODEL, 2020-2029 (USD MILLION)
TABLE 29 TURKEY SMALL AND MEDIUM-SIZED ENTERPRISES IN CYBER SECURITY MARKET, BY DEPLOYMENT MODEL, 2020-2029 (USD MILLION)
TABLE 30 TURKEY PHYSICAL SECURITY MARKET, BY END USER, 2020-2029 (USD MILLION)
TABLE 31 TURKEY CYBER SECURITY MARKET, BY END USER, 2020-2029 (USD MILLION)
TABLE 32 TURKEY COMMERCIAL IN PHYSICAL SECURITY MARKET, BY TYPE, 2020-2029 (USD MILLION)
TABLE 33 TURKEY COMMERCIAL IN CYBER SECURITY MARKET, BY TYPE, 2020-2029 (USD MILLION)
TABLE 34 TURKEY INDUSTRIAL IN PHYSICAL SECURITY MARKET, BY TYPE 2020-2029 (USD MILLION)
TABLE 35 TURKEY INDUSTRIAL IN CYBER SECURITY MARKET, BY TYPE 2020-2029 (USD MILLION)
TABLE 36 TURKEY RESIDENTIAL IN PHYSICAL SECURITY MARKET, BY TYPE 2020-2029 (USD MILLION)
TABLE 37 TURKEY RESIDENTIAL IN CYBER SECURITY MARKET, BY TYPE 2020-2029 (USD MILLION)
Lista de figuras
FIGURE 1 TURKEY PHYSICAL AND CYBER SECURITY MARKET: SEGMENTATION
FIGURE 2 TURKEY PHYSICAL AND CYBER SECURITY MARKET: DATA TRIANGULATION
FIGURE 3 TURKEY PHYSICAL AND CYBER SECURITY MARKET: DROC ANALYSIS
FIGURE 4 TURKEY PHYSICAL SECURITY MARKET: REGIONAL VS COUNTRY ANALYSIS
FIGURE 5 TURKEY CYBER SECURITY MARKET: REGIONAL VS COUNTRY ANALYSIS
FIGURE 6 TURKEY PHYSICAL AND CYBER SECURITY MARKET: COMPANY RESEARCH ANALYSIS
FIGURE 7 TURKEY PHYSICAL AND CYBER SECURITY MARKET: INTERVIEW DEMOGRAPHICS
FIGURE 8 TURKEY PHYSICAL SECURITY MARKET: DBMR MARKET POSITION GRID
FIGURE 9 TURKEY CYBER SECURITY MARKET: DBMR MARKET POSITION GRID
FIGURE 10 TURKEY CYBER SECURITY MARKET: VENDOR SHARE ANALYSIS
FIGURE 11 TURKEY PHYSICAL SECURITY MARKET: VENDOR SHARE ANALYSIS
FIGURE 12 TURKEY PHYSICAL SECURITY MARKET: MARKET END USER COVERAGE GRID
FIGURE 13 TURKEY CYBER SECURITY MARKET: MARKET END USER COVERAGE GRID
FIGURE 14 TURKEY CYBER SECURITY MARKET: SEGMENTATION
FIGURE 15 TURKEY PHYSICAL SECURITY MARKET: SEGMENTATION
FIGURE 16 AN INCREASE IN CLOUD SERVICES CYBER AND PHYSICAL SECURITY SOLUTIONS IS EXPECTED TO DRIVE TURKEY PHYSICAL SECURITY MARKET IN THE FORECAST PERIOD OF 2022 TO 2029
FIGURE 17 EMERGENCE OF SMART INTERCONNECTED BUILDING/HOME IS EXPECTED TO DRIVE TRUKEY CYBER SECURITY MARKET IN THE FORECAST PERIOD OF 2022 TO 2029
FIGURE 18 SERVICES SEGMENT IS EXPECTED TO ACCOUNT FOR THE LARGEST SHARE OF TURKEY CYBER SECURITY MARKET IN THE FORECASTED PERIOD OF 2022 & 2029
FIGURE 19 HARDWARE SEGMENT IS EXPECTED TO ACCOUNT FOR THE LARGEST SHARE OF TURKEY PHYSICAL SECURITY MARKET IN THE FORECASTED PERIOD OF 2022 & 2029
FIGURE 20 VALUE CHAIN FOR PHYSICAL AND CYBER SECURITY MARKET
FIGURE 21 PORTERS FIVE FORCES ANALYSIS FOR PHYSICAL AND CYBER SECURITY MARKET
FIGURE 22 PESTLE ANALYSIS FOR PHYSICAL AND CYBER SECURITY MARKET
FIGURE 23 DRIVERS, RESTRAINTS, OPPORTUNITIES, AND CHALLENGES OF TURKEY PHYSICAL AND CYBER SECURITY MARKET
FIGURE 24 KEY STATS OF REMOTE WORK
FIGURE 25 GROWING PREVALENCE OF BIOMETRIC SOLUTIONS AMONG CONSUMER
FIGURE 26 TECHNOLOGY AMALGAMATION IN SMART HOME/ BUILDINGS
FIGURE 27 IMPACT OF CYBER SECURITY THREAT
FIGURE 28 PHISHING ATTACKS REPORTED IN RESPECTIVE COUNTRIES IN Q2, 2021
FIGURE 29 TURKEY CYBER SECURITY MARKET, BY OFFERING, 2021
FIGURE 30 TURKEY PHYSICAL SECURITY MARKET, BY COMPONENT, 2021
FIGURE 31 TURKEY PHYSICAL SECURITY MARKET, BY AUTHENTICATION, 2021
FIGURE 32 TURKEY CYBER SECURITY MARKET: BY APPLICATION, 2021
FIGURE 33 TURKEY CYBER SECURITY MARKET: BY SECURITY TYPE, 2021
FIGURE 34 TURKEY PHYSICAL SECURITY MARKET, BY DEPLOYMENT MODEL, 2021
FIGURE 35 TURKEY CYBER SECURITY MARKET, BY DEPLOYMENT MODEL, 2021
FIGURE 36 TURKEY PHYSICAL SECURITY MARKET, BY ENTERPRISE SIZE, 2021
FIGURE 37 TURKEY CYBER SECURITY MARKET, BY ENTERPRISE SIZE, 2021
FIGURE 38 TURKEY PHYSICAL SECURITY MARKET: BY END USER, 2021
FIGURE 39 TURKEY CYBER SECURITY MARKET: BY END USER, 2021
FIGURE 40 TURKEY CYBER SECURITY MARKET: COMPANY SHARE 2021 (%)
FIGURE 41 TURKEY PHYSICAL SECURITY MARKET: COMPANY SHARE 2021 (%)
Metodología de investigación
La recopilación de datos y el análisis del año base se realizan utilizando módulos de recopilación de datos con muestras de gran tamaño. La etapa incluye la obtención de información de mercado o datos relacionados a través de varias fuentes y estrategias. Incluye el examen y la planificación de todos los datos adquiridos del pasado con antelación. Asimismo, abarca el examen de las inconsistencias de información observadas en diferentes fuentes de información. Los datos de mercado se analizan y estiman utilizando modelos estadísticos y coherentes de mercado. Además, el análisis de la participación de mercado y el análisis de tendencias clave son los principales factores de éxito en el informe de mercado. Para obtener más información, solicite una llamada de un analista o envíe su consulta.
La metodología de investigación clave utilizada por el equipo de investigación de DBMR es la triangulación de datos, que implica la extracción de datos, el análisis del impacto de las variables de datos en el mercado y la validación primaria (experto en la industria). Los modelos de datos incluyen cuadrícula de posicionamiento de proveedores, análisis de línea de tiempo de mercado, descripción general y guía del mercado, cuadrícula de posicionamiento de la empresa, análisis de patentes, análisis de precios, análisis de participación de mercado de la empresa, estándares de medición, análisis global versus regional y de participación de proveedores. Para obtener más información sobre la metodología de investigación, envíe una consulta para hablar con nuestros expertos de la industria.
Personalización disponible
Data Bridge Market Research es líder en investigación formativa avanzada. Nos enorgullecemos de brindar servicios a nuestros clientes existentes y nuevos con datos y análisis que coinciden y se adaptan a sus objetivos. El informe se puede personalizar para incluir análisis de tendencias de precios de marcas objetivo, comprensión del mercado de países adicionales (solicite la lista de países), datos de resultados de ensayos clínicos, revisión de literatura, análisis de mercado renovado y base de productos. El análisis de mercado de competidores objetivo se puede analizar desde análisis basados en tecnología hasta estrategias de cartera de mercado. Podemos agregar tantos competidores sobre los que necesite datos en el formato y estilo de datos que esté buscando. Nuestro equipo de analistas también puede proporcionarle datos en archivos de Excel sin procesar, tablas dinámicas (libro de datos) o puede ayudarlo a crear presentaciones a partir de los conjuntos de datos disponibles en el informe.