Mercado global de seguridad Zero Trust, por tipo de autenticación (autenticación de un solo factor, autenticación multifactor), tipo de solución ( seguridad de datos , seguridad de endpoints, seguridad de API, análisis de seguridad, gestión de políticas de seguridad), implementación (local, nube), tamaño de la organización (pyme, gran empresa), vertical ( banca, servicios financieros y seguros , TI y telecomunicaciones, gobierno y defensa, energía y servicios públicos, atención médica, comercio minorista y comercio electrónico, otros), país (EE. UU., Canadá, México, Brasil, Argentina, resto de Sudamérica, Alemania, Francia, Italia, Reino Unido, Bélgica, España, Rusia, Turquía, Países Bajos, Suiza, resto de Europa, Japón, China, India, Corea del Sur, Australia, Singapur, Malasia, Tailandia, Indonesia, Filipinas, resto de Asia-Pacífico, Emiratos Árabes Unidos, Arabia Saudita, Egipto, Sudáfrica, Israel, resto de Oriente Medio y África) - Tendencias de la industria y pronóstico hasta 2029.
Análisis de mercado y perspectivas del mercado de seguridad Zero Trust
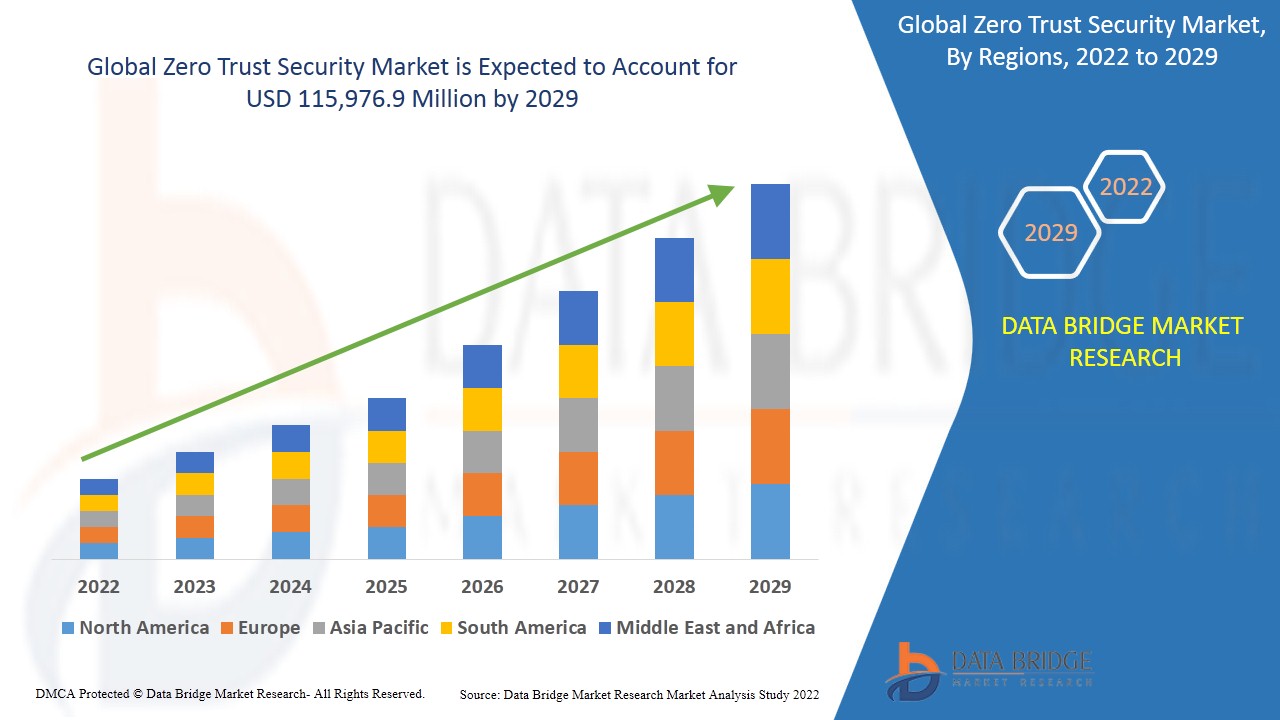
Se espera que el mercado de seguridad de confianza cero gane crecimiento de mercado en el período de pronóstico de 2022 a 2029. Data Bridge Market Research analiza que el mercado aumentará hasta USD 115,976.9 millones para 2029 y está creciendo a una CAGR del 15.20% en el período de pronóstico mencionado anteriormente.
Zero Trust hace referencia a un modelo de seguridad que se basa en el principio de controles de acceso estrictos y en no confiar en nadie por defecto, ni siquiera en aquellos que ya se encuentran dentro del perímetro de la red. El modelo está configurado de tal manera que cada persona y dispositivo que intente acceder a los recursos de una red privada debe pasar una estricta verificación de identidad, independientemente de si se encuentran dentro o fuera del perímetro de la red. Es un enfoque integral de la seguridad de la red que incorpora una variedad de tecnologías.
Se espera que factores como la mayor adopción de soluciones de seguridad de confianza cero, la creciente digitalización y el creciente número de vulnerabilidades cibernéticas debido a la adopción de servicios basados en la nube surjan como factores significativos que aceleren el crecimiento del mercado de seguridad de confianza cero. Además de esto, factores como la creciente conciencia e inversión en soluciones de seguridad de confianza cero, el aumento de las regulaciones gubernamentales como las próximas regulaciones CCPA, la creciente penetración de las tecnologías de IoT y las empresas que eligen proveedores externos, el creciente número de riesgos cibernéticos, la creciente frecuencia de ciberataques basados en objetivos y el aumento de las regulaciones para la protección de datos y la seguridad de la información agravarán aún más el crecimiento del mercado de seguridad de confianza cero en el período de pronóstico mencionado anteriormente. Sin embargo, las crecientes restricciones presupuestarias entre las empresas emergentes pequeñas y emergentes en las economías en desarrollo resultan como una restricción del crecimiento para el mercado.
También se prevé que la mayor demanda de una mejor visibilidad debido al aumento del tráfico de IoT entre las empresas, la creciente necesidad de soluciones de seguridad de confianza cero basadas en la nube entre las pymes y los crecientes avances tecnológicos y la modernización de las técnicas utilizadas generen oportunidades lucrativas para el mercado de seguridad de confianza cero en el período de pronóstico de 2022 a 2029. Las crecientes limitaciones de diseño e implementación para implementar soluciones de seguridad de confianza cero plantearán un desafío para el mercado de seguridad de confianza cero.
Este informe sobre el mercado de seguridad de confianza cero proporciona detalles de los nuevos desarrollos recientes, regulaciones comerciales, análisis de importación y exportación, análisis de producción, optimización de la cadena de valor, participación de mercado, impacto de los actores del mercado nacional y localizado, analiza las oportunidades en términos de bolsillos de ingresos emergentes, cambios en las regulaciones del mercado, análisis estratégico del crecimiento del mercado, tamaño del mercado, crecimientos del mercado de categorías, nichos de aplicación y dominio, aprobaciones de productos, lanzamientos de productos, expansiones geográficas, innovaciones tecnológicas en el mercado. Para obtener más información sobre el mercado de seguridad de confianza cero, comuníquese con Data Bridge Market Research para obtener un informe de analista ; nuestro equipo lo ayudará a tomar una decisión de mercado informada para lograr el crecimiento del mercado.
Alcance y tamaño del mercado de seguridad Zero Trust global
El mercado de seguridad de confianza cero está segmentado en función del tipo de autenticación, el tipo de solución, la implementación, el tamaño de la organización y la vertical. El crecimiento entre los diferentes segmentos le ayuda a obtener el conocimiento relacionado con los diferentes factores de crecimiento que se espera que prevalezcan en todo el mercado y a formular diferentes estrategias para ayudar a identificar las áreas de aplicación principales y la diferencia en su mercado objetivo.
- Según el tipo de autenticación, el mercado de seguridad de confianza cero se segmenta en autenticación de un solo factor y autenticación de múltiples factores.
- Según el tipo de solución, el mercado de seguridad de confianza cero se segmenta en seguridad de datos, seguridad de puntos finales, seguridad de API, análisis de seguridad y gestión de políticas de seguridad.
- Sobre la base de la implementación, el mercado de seguridad de confianza cero se segmenta en local y en la nube.
- En función del tamaño de la organización, el mercado de seguridad de confianza cero se segmenta en pymes y grandes empresas.
El mercado de seguridad de confianza cero también está segmentado en función de la vertical en banca, servicios financieros y seguros, TI y telecomunicaciones, gobierno y defensa, energía y servicios públicos, atención médica, comercio minorista y comercio electrónico, entre otros.
Análisis a nivel de país del mercado de seguridad de confianza cero
El mercado de seguridad de confianza cero está segmentado según el tipo de autenticación, el tipo de solución, la implementación, el tamaño de la organización y la vertical.
Los países cubiertos en el informe del mercado de seguridad de confianza cero son EE. UU., Canadá, México, Brasil, Argentina, resto de Sudamérica, Alemania, Francia, Italia, Reino Unido, Bélgica, España, Rusia, Turquía, Países Bajos, Suiza, resto de Europa, Japón, China, India, Corea del Sur, Australia, Singapur, Malasia, Tailandia, Indonesia, Filipinas, resto de Asia-Pacífico, Emiratos Árabes Unidos, Arabia Saudita, Egipto, Sudáfrica, Israel, resto de Medio Oriente y África.
Norteamérica domina el mercado de seguridad de confianza cero durante el período de pronóstico debido a la alta adopción de la transformación digital con grandes volúmenes de datos críticos generados, la creciente necesidad de soluciones de seguridad de confianza cero, el aumento de la digitalización, la mayor conciencia e inversión en soluciones de seguridad de confianza cero y el aumento de las regulaciones gubernamentales, como las próximas regulaciones CCPA en esta región en el período de pronóstico de 2022 a 2029. Por otro lado, se espera que Asia-Pacífico muestre un crecimiento lucrativo debido a la gran cantidad de riesgos cibernéticos debido a la adopción de servicios basados en la nube en esta región.
La sección de países del informe de mercado de seguridad de confianza cero también proporciona factores de impacto de mercado individuales y cambios en la regulación en el mercado a nivel nacional que afectan las tendencias actuales y futuras del mercado. Los puntos de datos como volúmenes de consumo, sitios y volúmenes de producción, análisis de importación y exportación, análisis de tendencias de precios, costo de las materias primas, análisis de la cadena de valor ascendente y descendente son algunos de los principales indicadores utilizados para pronosticar el escenario del mercado para países individuales. Además, se consideran la presencia y disponibilidad de marcas globales y sus desafíos enfrentados debido a la competencia grande o escasa de las marcas locales y nacionales, el impacto de los aranceles nacionales y las rutas comerciales al proporcionar un análisis de pronóstico de los datos del país.
Análisis del panorama competitivo y de la cuota de mercado de la seguridad Zero Trust
El panorama competitivo del mercado de seguridad de confianza cero proporciona detalles por competidor. Los detalles incluidos son una descripción general de la empresa, las finanzas de la empresa, los ingresos generados, el potencial de mercado, la inversión en investigación y desarrollo, las nuevas iniciativas de mercado, la presencia global, los sitios e instalaciones de producción, las capacidades de producción, las fortalezas y debilidades de la empresa, el lanzamiento de productos, la amplitud y variedad de productos, y el dominio de las aplicaciones. Los puntos de datos anteriores proporcionados solo están relacionados con el enfoque de las empresas en relación con el mercado de seguridad de confianza cero.
Algunos de los principales actores que operan en el informe del mercado de seguridad de confianza cero son Cisco, IBM, Akamai Technologies, Check Point Software Technologies Ltd, Pulse Secure, LLC, Palo Alto Networks, Cyxtera Technologies, Inc., Broadcom, Okta, Cloudflare, Inc, Forcepoint, Centrify Corporation., FireEye, Cyxtera Technologies, Inc., Illumio, Sophos Ltd y Microsoft, entre otros.
Acontecimientos recientes
- En septiembre de 2020, Check Point adquirió la tecnología basada en la nube de Odo Security para proporcionar acceso remoto seguro. Check Point combinó esta tecnología con su arquitectura Infinity para brindar la solución más sencilla y segura para las empresas que buscan acceso remoto seguro a cualquier aplicación.
SKU-
Obtenga acceso en línea al informe sobre la primera nube de inteligencia de mercado del mundo
- Panel de análisis de datos interactivo
- Panel de análisis de empresas para oportunidades con alto potencial de crecimiento
- Acceso de analista de investigación para personalización y consultas
- Análisis de la competencia con panel interactivo
- Últimas noticias, actualizaciones y análisis de tendencias
- Aproveche el poder del análisis de referencia para un seguimiento integral de la competencia
Metodología de investigación
La recopilación de datos y el análisis del año base se realizan utilizando módulos de recopilación de datos con muestras de gran tamaño. La etapa incluye la obtención de información de mercado o datos relacionados a través de varias fuentes y estrategias. Incluye el examen y la planificación de todos los datos adquiridos del pasado con antelación. Asimismo, abarca el examen de las inconsistencias de información observadas en diferentes fuentes de información. Los datos de mercado se analizan y estiman utilizando modelos estadísticos y coherentes de mercado. Además, el análisis de la participación de mercado y el análisis de tendencias clave son los principales factores de éxito en el informe de mercado. Para obtener más información, solicite una llamada de un analista o envíe su consulta.
La metodología de investigación clave utilizada por el equipo de investigación de DBMR es la triangulación de datos, que implica la extracción de datos, el análisis del impacto de las variables de datos en el mercado y la validación primaria (experto en la industria). Los modelos de datos incluyen cuadrícula de posicionamiento de proveedores, análisis de línea de tiempo de mercado, descripción general y guía del mercado, cuadrícula de posicionamiento de la empresa, análisis de patentes, análisis de precios, análisis de participación de mercado de la empresa, estándares de medición, análisis global versus regional y de participación de proveedores. Para obtener más información sobre la metodología de investigación, envíe una consulta para hablar con nuestros expertos de la industria.
Personalización disponible
Data Bridge Market Research es líder en investigación formativa avanzada. Nos enorgullecemos de brindar servicios a nuestros clientes existentes y nuevos con datos y análisis que coinciden y se adaptan a sus objetivos. El informe se puede personalizar para incluir análisis de tendencias de precios de marcas objetivo, comprensión del mercado de países adicionales (solicite la lista de países), datos de resultados de ensayos clínicos, revisión de literatura, análisis de mercado renovado y base de productos. El análisis de mercado de competidores objetivo se puede analizar desde análisis basados en tecnología hasta estrategias de cartera de mercado. Podemos agregar tantos competidores sobre los que necesite datos en el formato y estilo de datos que esté buscando. Nuestro equipo de analistas también puede proporcionarle datos en archivos de Excel sin procesar, tablas dinámicas (libro de datos) o puede ayudarlo a crear presentaciones a partir de los conjuntos de datos disponibles en el informe.