Global Hardware Encryption Market
Tamaño del mercado en miles de millones de dólares
Tasa de crecimiento anual compuesta (CAGR) :
% 
 USD
231.10 Million
USD
460.48 Million
2021
2029
USD
231.10 Million
USD
460.48 Million
2021
2029
| 2022 –2029 | |
| USD 231.10 Million | |
| USD 460.48 Million | |
|
|
|
|
Mercado global de cifrado de hardware, por tipo ( circuito integrado específico de la aplicación [ASIC] y matriz de puertas programables en campo [FPGA]), algoritmo y estándar (Rivest, Shamir y Adelman [RSA], estándar de cifrado avanzado [AES] y otros), tipo de producto (disco duro externo, disco duro interno, unidad de estado sólido, cifrador de red en línea, unidad flash USB), aplicación (electrónica de consumo, TI y telecomunicaciones, atención médica, aeroespacial y defensa, transporte, otros), uso final (industrial, comercial, residencial, gobierno) - Tendencias de la industria y pronóstico hasta 2029
Análisis y tamaño del mercado
El cifrado y el descifrado han desempeñado un papel fundamental en la prevención del acceso no autorizado a datos confidenciales o privados. El cifrado de hardware se considera muy eficaz para proteger la información confidencial durante su transmisión y almacenamiento.
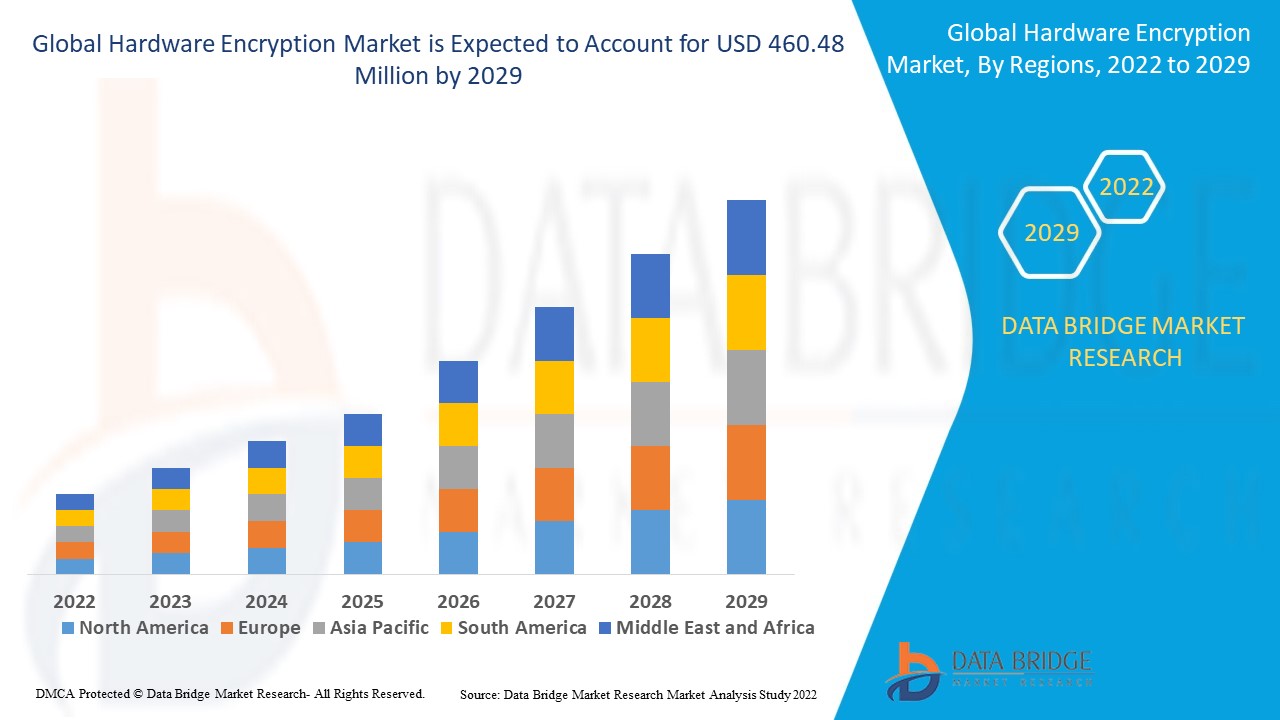
El mercado global de cifrado de hardware se valoró en 231,1 millones de dólares en 2021 y se espera que alcance los 460,48 millones de dólares para 2029, registrando una tasa de crecimiento anual compuesta (TCAC) del 9,00 % durante el período de pronóstico 2022-2029. La electrónica de consumo representa el segmento de aplicación más grande en este mercado debido al auge de sus aplicaciones. Además de información sobre el mercado, como el valor de mercado, la tasa de crecimiento, los segmentos de mercado, la cobertura geográfica, los actores del mercado y el escenario del mercado, el informe de mercado elaborado por el equipo de investigación de mercado de Data Bridge también incluye un análisis exhaustivo de expertos, análisis de importación y exportación, análisis de precios, análisis de consumo de producción y análisis PESTLE.
Definición de mercado
El cifrado de hardware se refiere al proceso de codificación de datos o información en un formato accesible únicamente para usuarios autorizados. Se requiere un algoritmo de cifrado para codificar el hardware que genera el texto cifrado. Este tipo de texto solo puede leerse después del descifrado. Un usuario autorizado debe introducir una clave o contraseña para descifrar estos datos privados.
Alcance del informe y segmentación del mercado
|
Métrica del informe |
Detalles |
|
Período de pronóstico |
2022 a 2029 |
|
Año base |
2021 |
|
Años históricos |
2020 (personalizable para 2014-2019) |
|
Unidades cuantitativas |
Ingresos en millones de USD, volúmenes en unidades, precios en USD |
|
Segmentos cubiertos |
Tipo (circuito integrado específico de la aplicación [ASIC] y matriz de puertas programables en campo [FPGA]), algoritmo y estándar (Rivest, Shamir y Adelman [RSA], estándar de cifrado avanzado [AES] y otros), tipo de producto (disco duro externo, disco duro interno, unidad de estado sólido, cifrador de red en línea, unidad flash USB), aplicación (electrónica de consumo, TI y telecomunicaciones, atención médica, aeroespacial y defensa, transporte, otros), uso final (industrial, comercial, residencial, gobierno) |
|
Países cubiertos |
EE. UU., Canadá y México en América del Norte, Alemania, Francia, Reino Unido, Países Bajos, Suiza, Bélgica, Rusia, Italia, España, Turquía, Resto de Europa en Europa, China, Japón, India, Corea del Sur, Singapur, Malasia, Australia, Tailandia, Indonesia, Filipinas, Resto de Asia-Pacífico (APAC) en Asia-Pacífico (APAC), Arabia Saudita, Emiratos Árabes Unidos, Israel, Egipto, Sudáfrica, Resto de Medio Oriente y África (MEA) como parte de Medio Oriente y África (MEA), Brasil, Argentina y Resto de América del Sur como parte de América del Sur. |
|
Actores del mercado cubiertos |
Microsoft (EE. UU.), Bloombase (EE. UU.), Symantec (EE. UU.), Intel Security (EE. UU.), EMC Corporation (EE. UU.), Amazon Web Services Inc. (EE. UU.), Check Point Software Technologies (Israel), Cisco System Inc. (EE. UU.), F-Secure (Finlandia), Fortinet Inc. (EE. UU.), IBM Corporation (EE. UU.), Oracle Corporation (EE. UU.), Palo Alto Networks Inc. (EE. UU.), WinMagic Inc. (Canadá) y Trend Micro Incorporated (Japón), entre otros. |
|
Oportunidades de mercado |
|
Dinámica del mercado del cifrado de hardware
Esta sección aborda la comprensión de los factores impulsores, las ventajas, las oportunidades, las limitaciones y los desafíos del mercado. Todo esto se analiza en detalle a continuación:
Conductores
Dinámica del mercado del cifrado de hardware
Esta sección aborda la comprensión de los factores impulsores, las ventajas, las oportunidades, las limitaciones y los desafíos del mercado. Todo esto se analiza en detalle a continuación:
Conductores
- Gestión de Riesgos
El uso de la seguridad de endpoints en las organizaciones para comprender, anticipar y gestionar integralmente sus riesgos es uno de los principales factores que impulsan el mercado del cifrado de hardware. Estas soluciones permiten tomar decisiones estratégicas con eficacia y responder con eficiencia.
- Implementación de regulaciones estrictas
El aumento en la implementación de regulaciones y mandatos estrictos por parte del gobierno en diversos sectores de usuarios finales acelera el crecimiento del mercado. Además, el cifrado de hardware se está adoptando ampliamente en las organizaciones debido a sus ventajas únicas.
- Aumento de las amenazas
El aumento de las amenazas a las organizaciones debido a la digitalización y al intercambio de grandes cantidades de datos está influyendo aún más en el mercado. El aumento de las amenazas a la ciberseguridad es otro factor que impulsa el mercado.
Además, la rápida urbanización, el cambio en el estilo de vida, el aumento de las inversiones y el mayor gasto de los consumidores impactan positivamente en el mercado de cifrado de hardware.
Oportunidades
Además, la amplia aceptación de la computación en la nube amplía las oportunidades rentables para los actores del mercado en el período de pronóstico de 2022 a 2029. Asimismo, el desarrollo y crecimiento sustancial de la IoT en diversas industrias expandirá aún más el mercado.
Restricciones/Desafíos
Por otro lado, se prevé que la necesidad de grandes inversiones de capital por parte de las partes interesadas y la deficiente capacidad de respuesta de los compradores obstaculicen el crecimiento del mercado. Asimismo, se prevé que el aumento en la adopción de SED y TPM en los procesadores actuales y el desconocimiento de la tecnología de cifrado de hardware supongan un desafío para el mercado del cifrado de hardware en el período de pronóstico 2022-2029.
Este informe sobre el mercado del cifrado de hardware proporciona detalles sobre los últimos desarrollos, regulaciones comerciales, análisis de importación y exportación, análisis de producción, optimización de la cadena de valor, cuota de mercado, impacto de los actores del mercado nacional y local, análisis de oportunidades en cuanto a nuevas fuentes de ingresos, cambios en las regulaciones del mercado, análisis estratégico del crecimiento del mercado, tamaño del mercado, crecimiento de las categorías de mercado, nichos de aplicación y dominio, aprobaciones y lanzamientos de productos, expansiones geográficas e innovaciones tecnológicas en el mercado. Para obtener más información sobre el mercado del cifrado de hardware, contacte con Data Bridge Market Research para obtener un informe analítico. Nuestro equipo le ayudará a tomar decisiones informadas para impulsar el crecimiento del mercado.
Impacto de la COVID-19 en el mercado del cifrado de hardware
La COVID-19 tuvo un impacto positivo en el mercado del cifrado de hardware debido al aumento en el número de sectores que adoptaron herramientas de seguridad durante el brote. Numerosos sectores, especialmente el de la electrónica de consumo, junto con las telecomunicaciones y las TI, implementaron seguridad de endpoints para proteger los datos de los consumidores. Se prevé que el mercado del cifrado de hardware experimente un alto crecimiento en el escenario pospandémico debido a la mayor concienciación sobre los beneficios potenciales del cifrado de hardware y al aumento de las ciberamenazas.
Desarrollos recientes
- Samsung presentó una solución integral de Elemento Seguro (SE) certificada con Nivel de Garantía de Evaluación de Criterios Comunes (CC EAL) 5+ para dispositivos móviles. Esta nueva solución ofrece una sólida seguridad gracias a un chip de seguridad (S3K250AF).
Alcance y tamaño del mercado global de cifrado de hardware
El mercado del cifrado de hardware se segmenta según tipo, tipo de producto, aplicación y uso final. El crecimiento de estos segmentos le permitirá analizar segmentos con un crecimiento reducido en las industrias y brindar a los usuarios una valiosa visión general del mercado y perspectivas que les ayudarán a tomar decisiones estratégicas para identificar las principales aplicaciones del mercado.
Tipo
- Circuito integrado de aplicación específica (ASIC) y matriz de puertas programables en campo (FPGA)
- Algoritmo y estándar (Rivest, Shamir y Adelman (RSA))
- Estándar de cifrado avanzado (AES)
- Otros
Tipo de producto
- Disco duro externo
- Disco duro interno
- Unidad de estado sólido
- Cifrador de red en línea
- Unidad flash USB
Solicitud
- Electrónica de consumo
- TI y telecomunicaciones
- Cuidado de la salud
- Aeroespacial y Defensa
- Transporte
- Otros
Uso final
- Industrial
- Comercial
- Residencial
- Gobierno
Análisis y perspectivas regionales del mercado de cifrado de hardware
Se analiza el mercado de cifrado de hardware y se proporcionan información y tendencias del tamaño del mercado por país, tipo, tipo de producto, aplicación y uso final como se mencionó anteriormente.
Los países cubiertos en el informe del mercado de cifrado de hardware son EE. UU., Canadá y México en América del Norte, Alemania, Francia, Reino Unido, Países Bajos, Suiza, Bélgica, Rusia, Italia, España, Turquía, Resto de Europa en Europa, China, Japón, India, Corea del Sur, Singapur, Malasia, Australia, Tailandia, Indonesia, Filipinas, Resto de Asia-Pacífico (APAC) en Asia-Pacífico (APAC), Arabia Saudita, Emiratos Árabes Unidos, Israel, Egipto, Sudáfrica, Resto de Medio Oriente y África (MEA) como parte de Medio Oriente y África (MEA), Brasil, Argentina y Resto de América del Sur como parte de América del Sur.
América del Norte domina el mercado de cifrado de hardware debido a que la alta necesidad de seguridad de datos es masiva en varios sectores dentro de la región.
Se espera que Asia-Pacífico (APAC) sea testigo de un crecimiento significativo durante el período de pronóstico de 2022 a 2029 debido al avance en la infraestructura de TI y telecomunicaciones en la región.
La sección de países del informe también presenta los factores que impactan en cada mercado y los cambios en la regulación nacional que impactan las tendencias actuales y futuras del mercado. Datos como el análisis de la cadena de valor aguas abajo y aguas arriba, las tendencias técnicas, el análisis de las cinco fuerzas de Porter y los estudios de caso son algunos de los indicadores utilizados para pronosticar el escenario del mercado en cada país. Asimismo, se consideran la presencia y disponibilidad de marcas globales y los desafíos que enfrentan debido a la alta o escasa competencia de marcas locales y nacionales, el impacto de los aranceles nacionales y las rutas comerciales, al proporcionar un análisis de pronóstico de los datos nacionales.
Panorama competitivo y mercado del cifrado de hardware
El panorama competitivo del mercado de cifrado de hardware ofrece detalles por competidor. Se incluye información general de la empresa, sus estados financieros, ingresos generados, potencial de mercado, inversión en investigación y desarrollo, nuevas iniciativas de mercado, presencia global, plantas de producción, capacidad de producción, fortalezas y debilidades de la empresa, lanzamiento de productos, alcance y variedad de productos, y dominio de las aplicaciones. Los datos anteriores se refieren únicamente al enfoque de las empresas en el mercado de cifrado de hardware.
Algunos de los principales actores que operan en el mercado de cifrado de hardware son
- Microsoft (EE. UU.)
- Bloombase. (EE. UU.)
- Symantec (EE. UU.)
- Intel Security (EE. UU.)
- Corporación EMC (EE. UU.)
- Amazon Web Services Inc. (EE. UU.)
- Check Point Software Technologies (Israel)
- Cisco System Inc. (EE. UU.)
- F-Secure (Finlandia)
- Fortinet Inc. (EE. UU.)
- IBM Corporation (EE. UU.)
- Oracle Corporation (EE. UU.)
- Palo Alto Networks Inc. (EE. UU.)
- WinMagic Inc. (Canadá)
- Trend Micro Incorporated (Japón)
SKU-
Obtenga acceso en línea al informe sobre la primera nube de inteligencia de mercado del mundo
- Panel de análisis de datos interactivo
- Panel de análisis de empresas para oportunidades con alto potencial de crecimiento
- Acceso de analista de investigación para personalización y consultas
- Análisis de la competencia con panel interactivo
- Últimas noticias, actualizaciones y análisis de tendencias
- Aproveche el poder del análisis de referencia para un seguimiento integral de la competencia
Tabla de contenido
1. INTRODUCTION
1.1 OBJECTIVES OF THE STUDY
1.2 MARKET DEFINITION
1.3 OVERVIEW OF GLOBAL HARDWARE ENCRYPTION MARKET
1.4 CURRENCY AND PRICING
1.5 LIMITATION
1.6 MARKETS COVERED
2. MARKET SEGMENTATION
2.1 KEY TAKEAWAYS
2.2 ARRIVING AT THE GLOBAL HARDWARE ENCRYPTION MARKET
2.3 VENDOR POSITIONING GRID
2.4 TECHNOLOGY LIFE LINE CURVE
2.5 MARKET GUIDE
2.6 MULTIVARIATE MODELLING
2.7 TOP TO BOTTOM ANALYSIS
2.8 STANDARDS OF MEASUREMENT
2.9 VENDOR SHARE ANALYSIS
2.10 DATA POINTS FROM KEY PRIMARY INTERVIEWS
2.11 DATA POINTS FROM KEY SECONDARY DATABASES
2.12 GLOBAL HARDWARE ENCRYPTION MARKET: RESEARCH SNAPSHOT
2.13 ASSUMPTIONS
3. MARKET OVERVIEW
3.1 DRIVERS
3.2 RESTRAINTS
3.3 OPPORTUNITIES
3.4 CHALLENGES
4. EXECUTIVE SUMMARY
5. PREMIUM INSIGHTS
5.1 VALUE CHAIN ANALYSIS
5.2 BRAND ANALYSIS
5.3 ECOSYSTEM MARKET MAP
5.4 TECHNOLOGICAL TRENDS
5.5 TOP WINNING STRATEGIES
5.6 PORTER’S FIVE FORCES ANALYSIS
6. GLOBAL HARDWARE ENCRYPTION MARKET, BY PRODUCT
6.1 OVERVIEW
6.2 INTERNAL HARD DISK DRIVE
6.3 EXTERNAL HARD DISK DRIVE
6.4 USB FLASH DRIVE
6.5 SOLID-STATE DRIVE
6.6 INLINE NETWORK ENCRYPTION
6.7 OTHERS
7. GLOBAL HARDWARE ENCRYPTION MARKET, BY ALGORITHM & STANDARD
7.1 OVERVIEW
7.2 SECURE HASH ALGORITHM (SHA)
7.3 DIGITAL SIGNATURE ALGORITHM (DSA)
7.4 DATA ENCRYPTION STANDARD (DES)
7.5 ADVANCED ENCRYPTION STANDARD (AES)
7.6 RIVEST-SHAMIR-ADLEMAN (RSA) ALGORITHM
7.7 ELLIPTIC CURVE CRYPTOGRAPHY (ECC)
8. GLOBAL HARDWARE ENCRYPTION MARKET, BY ARCHITECTURE
8.1 OVERVIEW
8.2 PRODUCT SPECIFIC INTEGRATED CIRCUITS (ASIC)
8.3 FIELD PROGRAMMABLE GATE ARRAYS (FPGA)
9. GLOBAL HARDWARE ENCRYPTION MARKET, BY APPLICATION
9.1 OVERVIEW
9.2 IT & TELECOM
9.2.1 BY PRODUCT
9.2.1.1. INTERNAL HARD DISK DRIVE
9.2.1.2. EXTERNAL HARD DISK DRIVE
9.2.1.3. USB FLASH DRIVE
9.2.1.4. SOLID-STATE DRIVE
9.2.1.5. INLINE NETWORK ENCRYPTION
9.2.1.6. OTHERS
9.3 CONSUMER ELECTRONICS
9.3.1 BY PRODUCT
9.3.1.1. INTERNAL HARD DISK DRIVE
9.3.1.2. EXTERNAL HARD DISK DRIVE
9.3.1.3. USB FLASH DRIVE
9.3.1.4. SOLID-STATE DRIVE
9.3.1.5. INLINE NETWORK ENCRYPTION
9.3.1.6. OTHERS
9.4 AEROSPACE & DEFENSE
9.4.1 BY PRODUCT
9.4.1.1. INTERNAL HARD DISK DRIVE
9.4.1.2. EXTERNAL HARD DISK DRIVE
9.4.1.3. USB FLASH DRIVE
9.4.1.4. SOLID-STATE DRIVE
9.4.1.5. INLINE NETWORK ENCRYPTION
9.4.1.6. OTHERS
9.5 TRANSPORTATION
9.5.1 BY PRODUCT
9.5.1.1. INTERNAL HARD DISK DRIVE
9.5.1.2. EXTERNAL HARD DISK DRIVE
9.5.1.3. USB FLASH DRIVE
9.5.1.4. SOLID-STATE DRIVE
9.5.1.5. INLINE NETWORK ENCRYPTION
9.5.1.6. OTHERS
9.6 HEALTHCARE
9.6.1 BY PRODUCT
9.6.1.1. INTERNAL HARD DISK DRIVE
9.6.1.2. EXTERNAL HARD DISK DRIVE
9.6.1.3. USB FLASH DRIVE
9.6.1.4. SOLID-STATE DRIVE
9.6.1.5. INLINE NETWORK ENCRYPTION
9.6.1.6. OTHERS
9.7 OTHERS
9.7.1 BY PRODUCT
9.7.1.1. INTERNAL HARD DISK DRIVE
9.7.1.2. EXTERNAL HARD DISK DRIVE
9.7.1.3. USB FLASH DRIVE
9.7.1.4. SOLID-STATE DRIVE
9.7.1.5. INLINE NETWORK ENCRYPTION
9.7.1.6. OTHERS
10. GLOBAL HARDWARE ENCRYPTION MARKET, BY REGION
10.1 GLOBAL HARDWARE ENCRYPTION MARKET, (ALL SEGMENTATION PROVIDED ABOVE IS REPRESENTED IN THIS CHAPTER BY COUNTRY)
10.1.1 NORTH AMERICA
10.1.1.1. U.S.
10.1.1.2. CANADA
10.1.1.3. MEXICO
10.1.2 EUROPE
10.1.2.1. GERMANY
10.1.2.2. FRANCE
10.1.2.3. U.K.
10.1.2.4. ITALY
10.1.2.5. SPAIN
10.1.2.6. RUSSIA
10.1.2.7. TURKEY
10.1.2.8. BELGIUM
10.1.2.9. NETHERLANDS
10.1.2.10. SWITZERLAND
10.1.2.11. denmark
10.1.2.12. sweden
10.1.2.13. poland
10.1.2.14. norway
10.1.2.15. finland
10.1.2.16. REST OF EUROPE
10.1.3 ASIA PACIFIC
10.1.3.1. JAPAN
10.1.3.2. CHINA
10.1.3.3. SOUTH KOREA
10.1.3.4. INDIA
10.1.3.5. AUSTRALIA
10.1.3.6. SINGAPORE
10.1.3.7. THAILAND
10.1.3.8. MALAYSIA
10.1.3.9. INDONESIA
10.1.3.10. PHILIPPINES
10.1.3.11. new zealand
10.1.3.12. taiwan
10.1.3.13. vietnam
10.1.3.14. REST OF ASIA PACIFIC
10.1.4 SOUTH AMERICA
10.1.4.1. BRAZIL
10.1.4.2. ARGENTINA
10.1.4.3. REST OF SOUTH AMERICA
10.1.5 MIDDLE EAST AND AFRICA
10.1.5.1. SOUTH AFRICA
10.1.5.2. EGYPT
10.1.5.3. bahrain
10.1.5.4. qatar
10.1.5.5. kuwait
10.1.5.6. oman
10.1.5.7. SAUDI ARABIA
10.1.5.8. U.A.E
10.1.5.9. ISRAEL
10.1.5.10. REST OF MIDDLE EAST AND AFRICA
10.2 KEY PRIMARY INSIGHTS: BY MAJOR COUNTRIES
11. GLOBAL HARDWARE ENCRYPTION MARKET, COMPANY LANDSCAPE
11.1 COMPANY SHARE ANALYSIS: NORTH AMERICA
11.2 COMPANY SHARE ANALYSIS: EUROPE
11.3 COMPANY SHARE ANALYSIS: ASIA-PACIFIC
11.4 MERGERS & ACQUISITIONS
11.5 NEW PRODUCT DEVELOPMENT & APPROVALS
11.6 EXPANSIONS
11.7 REGULATORY CHANGES
11.8 PARTNERSHIP AND OTHER STRATEGIC DEVELOPMENTS
12. GLOBAL HARDWARE ENCRYPTION MARKET, SWOT ANALYSIS
13. GLOBAL HARDWARE ENCRYPTION MARKET, COMPANY PROFILE
13.1 TOSHIBA CORPORATION
13.1.1 COMPANY SNAPSHOT
13.1.2 REVENUE ANALYSIS
13.1.3 GEOGRAPHIC PRESENCE
13.1.4 PRODUCT PORTFOLIO
13.1.5 RECENT DEVELOPMENTS
13.2 MICRON TECHNOLOGY, INC
13.2.1 COMPANY SNAPSHOT
13.2.2 REVENUE ANALYSIS
13.2.3 GEOGRAPHIC PRESENCE
13.2.4 PRODUCT PORTFOLIO
13.2.5 RECENT DEVELOPMENTS
13.3 MAXIM INTEGRATED PRODUCTS, INC
13.3.1 COMPANY SNAPSHOT
13.3.2 REVENUE ANALYSIS
13.3.3 GEOGRAPHIC PRESENCE
13.3.4 PRODUCT PORTFOLIO
13.3.5 RECENT DEVELOPMENTS
13.4 SAMSUNG
13.4.1 COMPANY SNAPSHOT
13.4.2 REVENUE ANALYSIS
13.4.3 GEOGRAPHIC PRESENCE
13.4.4 PRODUCT PORTFOLIO
13.4.5 RECENT DEVELOPMENTS
13.5 WESTERN DIGITAL CORPORATION
13.5.1 COMPANY SNAPSHOT
13.5.2 REVENUE ANALYSIS
13.5.3 GEOGRAPHIC PRESENCE
13.5.4 PRODUCT PORTFOLIO
13.5.5 RECENT DEVELOPMENTS
13.6 WINMAGIC, INC
13.6.1 COMPANY SNAPSHOT
13.6.2 REVENUE ANALYSIS
13.6.3 GEOGRAPHIC PRESENCE
13.6.4 PRODUCT PORTFOLIO
13.6.5 RECENT DEVELOPMENTS
13.7 KANGURU SOLUTIONS
13.7.1 COMPANY SNAPSHOT
13.7.2 REVENUE ANALYSIS
13.7.3 GEOGRAPHIC PRESENCE
13.7.4 PRODUCT PORTFOLIO
13.7.5 RECENT DEVELOPMENTS
13.8 BROADCOM CORPORATION
13.8.1 COMPANY SNAPSHOT
13.8.2 REVENUE ANALYSIS
13.8.3 GEOGRAPHIC PRESENCE
13.8.4 PRODUCT PORTFOLIO
13.8.5 RECENT DEVELOPMENTS
13.9 INTEL CORPORATION
13.9.1 COMPANY SNAPSHOT
13.9.2 REVENUE ANALYSIS
13.9.3 GEOGRAPHIC PRESENCE
13.9.4 PRODUCT PORTFOLIO
13.9.5 RECENT DEVELOPMENTS
13.10 IBM CORPORATION
13.10.1 COMPANY SNAPSHOT
13.10.2 REVENUE ANALYSIS
13.10.3 GEOGRAPHIC PRESENCE
13.10.4 PRODUCT PORTFOLIO
13.10.5 RECENT DEVELOPMENTS
13.11 THALES E-SECURITY
13.11.1 COMPANY SNAPSHOT
13.11.2 REVENUE ANALYSIS
13.11.3 GEOGRAPHIC PRESENCE
13.11.4 PRODUCT PORTFOLIO
13.11.5 RECENT DEVELOPMENTS
13.12 MCAFEE
13.12.1 COMPANY SNAPSHOT
13.12.2 REVENUE ANALYSIS
13.12.3 GEOGRAPHIC PRESENCE
13.12.4 PRODUCT PORTFOLIO
13.12.5 RECENT DEVELOPMENTS
13.13 NETAPP
13.13.1 COMPANY SNAPSHOT
13.13.2 REVENUE ANALYSIS
13.13.3 GEOGRAPHIC PRESENCE
13.13.4 PRODUCT PORTFOLIO
13.13.5 RECENT DEVELOPMENTS
13.14 INFINEON TECHNOLOGIES
13.14.1 COMPANY SNAPSHOT
13.14.2 REVENUE ANALYSIS
13.14.3 GEOGRAPHIC PRESENCE
13.14.4 PRODUCT PORTFOLIO
13.14.5 RECENT DEVELOPMENTS
13.15 IDEMIA
13.15.1 COMPANY SNAPSHOT
13.15.2 REVENUE ANALYSIS
13.15.3 GEOGRAPHIC PRESENCE
13.15.4 PRODUCT PORTFOLIO
13.15.5 RECENT DEVELOPMENTS
13.16 NXP SEMICONDUCTORS
13.16.1 COMPANY SNAPSHOT
13.16.2 REVENUE ANALYSIS
13.16.3 GEOGRAPHIC PRESENCE
13.16.4 PRODUCT PORTFOLIO
13.16.5 RECENT DEVELOPMENTS
13.17 FORTANIX
13.17.1 COMPANY SNAPSHOT
13.17.2 REVENUE ANALYSIS
13.17.3 GEOGRAPHIC PRESENCE
13.17.4 PRODUCT PORTFOLIO
13.17.5 RECENT DEVELOPMENTS
13.18 MICRO FOCUS
13.18.1 COMPANY SNAPSHOT
13.18.2 REVENUE ANALYSIS
13.18.3 GEOGRAPHIC PRESENCE
13.18.4 PRODUCT PORTFOLIO
13.18.5 RECENT DEVELOPMENTS
13.19 ATOS SE
13.19.1 COMPANY SNAPSHOT
13.19.2 REVENUE ANALYSIS
13.19.3 GEOGRAPHIC PRESENCE
13.19.4 PRODUCT PORTFOLIO
13.19.5 RECENT DEVELOPMENTS
13.20 ENTRUST
13.20.1 COMPANY SNAPSHOT
13.20.2 REVENUE ANALYSIS
13.20.3 GEOGRAPHIC PRESENCE
13.20.4 PRODUCT PORTFOLIO
13.20.5 RECENT DEVELOPMENTS
13.21 TREND MICRO
13.21.1 COMPANY SNAPSHOT
13.21.2 REVENUE ANALYSIS
13.21.3 GEOGRAPHIC PRESENCE
13.21.4 PRODUCT PORTFOLIO
13.21.5 RECENT DEVELOPMENTS
13.22 KIOXIA HOLDINGS CORPORATION
13.22.1 COMPANY SNAPSHOT
13.22.2 REVENUE ANALYSIS
13.22.3 GEOGRAPHIC PRESENCE
13.22.4 PRODUCT PORTFOLIO
13.22.5 RECENT DEVELOPMENTS
13.23 KINGSTON TECHNOLOGY CORP
13.23.1 COMPANY SNAPSHOT
13.23.2 REVENUE ANALYSIS
13.23.3 GEOGRAPHIC PRESENCE
13.23.4 PRODUCT PORTFOLIO
13.23.5 RECENT DEVELOPMENTS
13.24 SEAGATE TECHNOLOGY PLC
13.24.1 COMPANY SNAPSHOT
13.24.2 REVENUE ANALYSIS
13.24.3 GEOGRAPHIC PRESENCE
13.24.4 PRODUCT PORTFOLIO
13.24.5 RECENT DEVELOPMENTS
NOTE: THE COMPANIES PROFILED IS NOT EXHAUSTIVE LIST AND IS AS PER OUR PREVIOUS CLIENT REQUIREMENT. WE PROFILE MORE THAN 100 COMPANIES IN OUR STUDY AND HENCE THE LIST OF COMPANIES CAN BE MODIFIED OR REPLACED ON REQUEST
14. RELATED REPORTS
15. QUESTIONNAIRE
16. ABOUT DATA BRIDGE MARKET RESEARCH
Metodología de investigación
La recopilación de datos y el análisis del año base se realizan utilizando módulos de recopilación de datos con muestras de gran tamaño. La etapa incluye la obtención de información de mercado o datos relacionados a través de varias fuentes y estrategias. Incluye el examen y la planificación de todos los datos adquiridos del pasado con antelación. Asimismo, abarca el examen de las inconsistencias de información observadas en diferentes fuentes de información. Los datos de mercado se analizan y estiman utilizando modelos estadísticos y coherentes de mercado. Además, el análisis de la participación de mercado y el análisis de tendencias clave son los principales factores de éxito en el informe de mercado. Para obtener más información, solicite una llamada de un analista o envíe su consulta.
La metodología de investigación clave utilizada por el equipo de investigación de DBMR es la triangulación de datos, que implica la extracción de datos, el análisis del impacto de las variables de datos en el mercado y la validación primaria (experto en la industria). Los modelos de datos incluyen cuadrícula de posicionamiento de proveedores, análisis de línea de tiempo de mercado, descripción general y guía del mercado, cuadrícula de posicionamiento de la empresa, análisis de patentes, análisis de precios, análisis de participación de mercado de la empresa, estándares de medición, análisis global versus regional y de participación de proveedores. Para obtener más información sobre la metodología de investigación, envíe una consulta para hablar con nuestros expertos de la industria.
Personalización disponible
Data Bridge Market Research es líder en investigación formativa avanzada. Nos enorgullecemos de brindar servicios a nuestros clientes existentes y nuevos con datos y análisis que coinciden y se adaptan a sus objetivos. El informe se puede personalizar para incluir análisis de tendencias de precios de marcas objetivo, comprensión del mercado de países adicionales (solicite la lista de países), datos de resultados de ensayos clínicos, revisión de literatura, análisis de mercado renovado y base de productos. El análisis de mercado de competidores objetivo se puede analizar desde análisis basados en tecnología hasta estrategias de cartera de mercado. Podemos agregar tantos competidores sobre los que necesite datos en el formato y estilo de datos que esté buscando. Nuestro equipo de analistas también puede proporcionarle datos en archivos de Excel sin procesar, tablas dinámicas (libro de datos) o puede ayudarlo a crear presentaciones a partir de los conjuntos de datos disponibles en el informe.