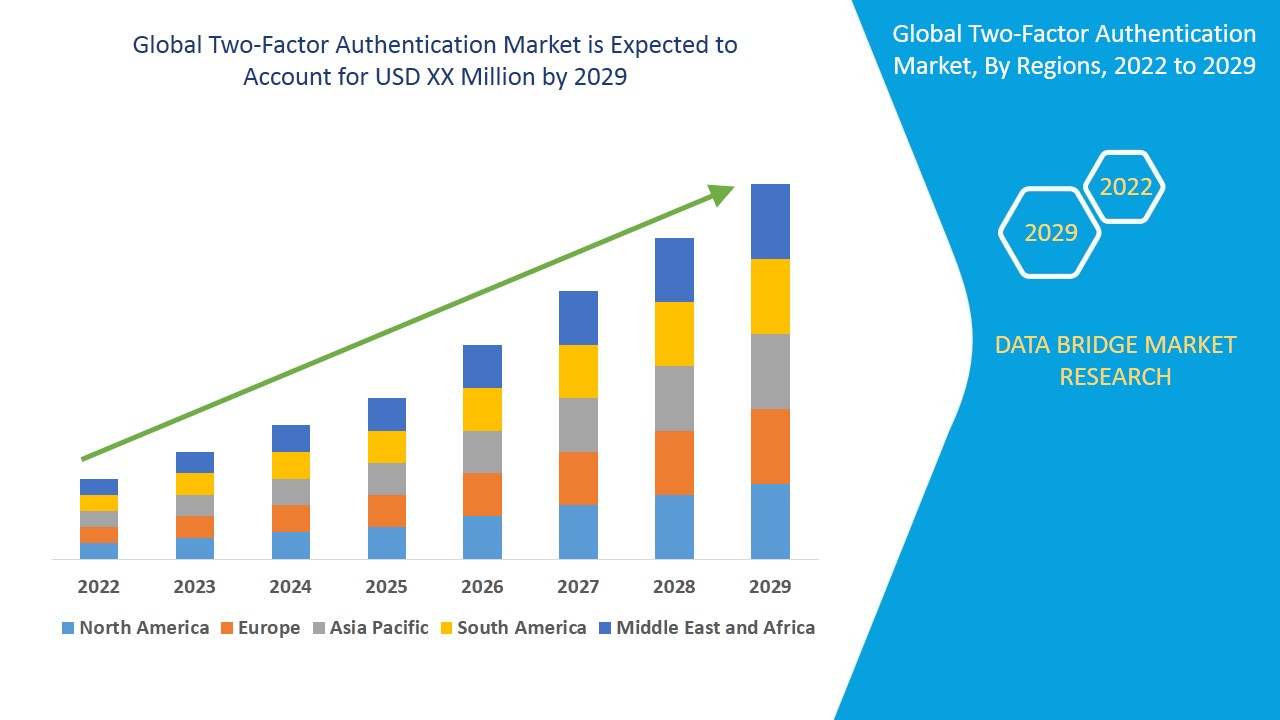
Market Analysis and Insights of Two-Factor Authentication Market
Two-factor authentication market is expected to gain market growth in the forecast period of 2022 to 2029. Data Bridge Market Research analyses the two-factor authentication market to exhibit a CAGR of 18.45% for the forecast period of 2022 to 2029.
Authentication refers to an analytical technique which basically ensures the security of credentials and resources associated with them with the help of one time password, hardware tokens, biometrics and others. The procedure of two-factor authentication generally includes a security token in text message or an email, voice and a password that will secure the credentials.
The factors such as the adoption of two-factor authentication and rising security breach threats will emerge as the major factors driving market growth. In addition to this, the increasing number of online transactions, provision of high security by hardware tokens ands, provision of high security by hardware tokens, and the emergence of 4G/5G devices will further aggravate the market value for the forecast period of 2022 to 2029. Additionally, the factors such as the high demand for two-factor authentication due to the various beneficial features such as the voice recognition, iris recognition, fingerprint and passwords in various health care, defense and governments segments are estimated to cushion the growth of the market. On the other hand, the high costs associated with hardware and software act as a restraint for the market. Moreover, the initial investment and lack of telecom infrastructure are also estimated to obstruct overall growth of the market.
In addition to this, rising penetration in residential applications and technological innovations with improved capabilities are estimated to create new opportunities for growing the market within the forecast period. On the flip side, the lack of telecom infrastructure result as a challenge for the market.
This two-factor authentication market report provides details of new recent developments, trade regulations, import export analysis, production analysis, value chain optimization, market share, impact of domestic and localized market players, analyses opportunities in terms of emerging revenue pockets, changes in market regulations, strategic market growth analysis, market size, category market growths, application niches and dominance, product approvals, product launches, geographical expansions, technological innovations in the market. To gain more info on two-factor authentication market contact Data Bridge Market Research for an Analyst Brief, our team will help you take an informed market decision to achieve market growth.
Global Two-Factor Authentication Market Scope and Market Size
The two-factor authentication market is segmented on the basis of type, model, technology and end-user. The growth amongst the different segments helps you in attaining the knowledge related to the different growth factors expected to be prevalent throughout the market and formulate different strategies to help identify core application areas and the difference in your target market.
- The two-factor authentication market on the basis of type has been segmented as one time password (OTP) and public key infrastructure (PKI).
- On the basis of model, the two-factor authentication market has been segmented into smart card with PIN, one time password with PIN, biometric technology with PIN, smart card with biometric technology and others.
- On the basis of technology, the two-factor authentication market has been segmented into OTP authenticators, PKI authenticators, physical and logical access control, out-of-band authenticators and mobile PKI office suite.
- Two-factor authentication has also been segmented on the basis of end-user into banking and finance, government, military and defense, commercial security, travel and immigration, healthcare, consumer electronics and aerospace.
Two-Factor Authentication Market Country Level Analysis
The two-factor authentication market is analyzed and market size, volume information is provided by type, model, technology and end-user as referenced above.
The countries covered in the two-factor authentication market report are U.S., Canada and Mexico in North America, Germany, France, U.K., Netherlands, Switzerland, Belgium, Russia, Italy, Spain, Turkey, Rest of Europe in Europe, China, Japan, India, South Korea, Singapore, Malaysia, Australia, Thailand, Indonesia, Philippines, Rest of Asia-Pacific (APAC) in the Asia-Pacific (APAC), Saudi Arabia, U.A.E, Israel, Egypt, South Africa, Rest of Middle East and Africa (MEA) as a part of Middle East and Africa (MEA), Brazil, Argentina and Rest of South America as part of South America.
North America region dominates the two-factor authentication market due to the prevalence of many service providers, adoption of security measures and initiatives adopted by government regarding safety and security of credentials in the region within the forecasted period. The Asia-Pacific region is projected to undergo substantial during the forecast period due to the increasing adoption of bring your own technology and growth of IT technology.
The country section of the two-factor authentication market report also provides individual market impacting factors and changes in regulation in the market domestically that impacts the current and future trends of the market. Data points such as consumption volumes, production sites and volumes, import export analysis, price trend analysis, cost of raw materials, down-stream and upstream value chain analysis are some of the major pointers used to forecast the market scenario for individual countries. Also, presence and availability of global brands and their challenges faced due to large or scarce competition from local and domestic brands, impact of domestic tariffs and trade routes are considered while providing forecast analysis of the country data.
Competitive Landscape and Two-Factor Authentication Market Share Analysis
The two-factor authentication market competitive landscape provides details by competitor. Details included are company overview, company financials, revenue generated, market potential, investment in research and development, new market initiatives, global presence, production sites and facilities, production capacities, company strengths and weaknesses, product launch, product width and breadth, application dominance. The above data points provided are only related to the companies’ focus related to two-factor authentication market.
Some of the major players operating in the two-factor authentication market report are Thales Group, Fujitsu, Suprema., OneSpan, NEC Corporation, Broadcom, RSA., IBM, HID Global Corporation, Google LLC, Dell Inc., Amazon Web Services, Inc., Entrust Corporation, HID Global Corporation, ASSA ABLOY, RSA Security LLC, SUPREMA., Crossmatch, Censornet, IDEMIA, ZKTECO CO., LTD., Watchdata Co., Ltd., SecurEnvoy Ltd., Entrust Corporation, 3M, IDEMIA, Yubico, SecurStar, SecurEnvoy Ltd, and SecureAuth Corporation, among others.
SKU-
Get online access to the report on the World's First Market Intelligence Cloud
- Interactive Data Analysis Dashboard
- Company Analysis Dashboard for high growth potential opportunities
- Research Analyst Access for customization & queries
- Competitor Analysis with Interactive dashboard
- Latest News, Updates & Trend analysis
- Harness the Power of Benchmark Analysis for Comprehensive Competitor Tracking
Table of Content
1 INTRODUCTION
1.1 OBJECTIVES OF THE STUDY
1.2 MARKET DEFINITION
1.3 OVERVIEW OF GLOBAL TWO-FACTOR AUTHENTICATION MARKET
1.4 CURRENCY AND PRICING
1.5 LIMITATION
1.6 MARKETS COVERED
2 MARKET SEGMENTATION
2.1 KEY TAKEAWAYS
2.2 ARRIVING AT THE GLOBAL TWO-FACTOR AUTHENTICATION MARKETSIZE
2.2.1 VENDOR POSITIONING GRID
2.2.2 TECHNOLOGY LIFE LINE CURVE
2.2.3 MULTIVARIATE MODELLING
2.2.4 TOP TO BOTTOM ANALYSIS
2.2.5 STANDARDS OF MEASUREMENT
2.2.6 VENDOR SHARE ANALYSIS
2.2.7 DATA POINTS FROM KEY PRIMARY INTERVIEWS
2.2.8 DATA POINTS FROM KEY SECONDARY DATABASES
2.3 GLOBAL TWO-FACTOR AUTHENTICATION MARKET: RESEARCH SNAPSHOT
2.4 ASSUMPTIONS
3 MARKET OVERVIEW
3.1 DRIVERS
3.2 RESTRAINTS
3.3 OPPORTUNITIES
3.4 CHALLENGES
4 EXECUTIVE SUMMARY
5 PREMIUM INSIGHTS
5.1.1 VALUE CHAIN ANALYSIS
5.1.2 REGULATORY LANDSCAPE
5.1.3 REGULATORY COMPLIANCES
5.1.3.1. CRIMINAL JUSTICE INFORMATION SYSTEM (CJIS) SECURITY POLICY
5.1.3.2. PAYMENT CARD INDUSTRY (PCI) DATA SECURITY STANDARD
5.1.3.3. FFIEC AUTHENTICATION IN AN INTERNET BANKING ENVIRONMENT GUIDANCE
5.1.3.4. FAIR AND ACCURATE CREDIT TRANSACTION ACT (FACTA)
5.1.3.5. IDENTITY THEFT RED FLAGS
5.1.3.6. HEALTH INSURANCE PORTABILITY AND ACCOUNTABILITY ACT (HIPPA)
5.1.3.7. SARBANES–OXLEY ACT (SOX)
5.1.3.8. GRAMM–LEACH–BLILEY ACT
5.1.4 NEW INDUSTRY TRENDS
5.1.4.1. OUT-OF-BAND AUTHENTICATION
5.1.4.2. BUILT-IN FINGERPRINT READERS
5.1.4.3. BAKED-IN AUTHENTICATION
6 INDUSTRY INSIGHTS
7 GLOBAL TWO-FACTOR AUTHENTICATION MARKET, BY TYPE
7.1 OVERVIEW
7.2 ONE TIME PASSWORD
7.3 PUBLIC KEY INFRASTRUCTURE
8 GLOBAL TWO-FACTOR AUTHENTICATION MARKET, BY MODEL
8.1 OVERVIEW
8.2 SMART CARD WITH PIN
8.3 ONE TIME PASSWORD WITH PIN
8.4 BIOMETRIC TECHNOLOGY WITH PIN
8.5 SMART CARD WITH BIOMETRIC TECHNOLOGY
8.6 OTHERS
9 GLOBAL TWO-FACTOR AUTHENTICATION MARKET, BY TECHNOLOGY
9.1 OVERVIEW
9.2 OTP AUTHENTICATORS
9.3 PKI AUTHENTICATORS
9.4 PHYSICAL AND LOGICAL ACCESS CONTROL
9.5 OUT-OF-BAND AUTHENTICATORS
9.6 MOBILE PKI OFFICE SUITE
10 GLOBAL TWO-FACTOR AUTHENTICATION MARKET, BY METHODS
10.1 OVERVIEW
10.2 KNOWLEDGE FACTORS
10.3 POSSESSION FACTORS
10.4 INHERENCE FACTORS
11 GLOBAL TWO-FACTOR AUTHENTICATION MARKET, BY SERVICES
11.1 OVERVIEW
11.2 COMPLAINCE MANAGEMENT
11.3 SUBSCRIPTION KEYS MANAGEMENT
11.4 MANAGED PUBLICS KEY INFRASTRUCTURE (PKI)
11.5 REPORTING
11.6 OTHERS
12 GLOBAL TWO-FACTOR AUTHENTICATION MARKET, BY TOKENIZATION TYPE
12.1 OVERVIEW
12.2 TOKEN-BASED AUTHENTICATION
12.3 TOKENLESS AUTHENTICATION
13 GLOBAL TWO-FACTOR AUTHENTICATION MARKET, BY END USER
13.1 OVERVIEW
13.2 BANKING AND FINANCE
13.2.1 SMART CARD WITH PIN
13.2.2 ONE TIME PASSWORD WITH PIN
13.2.3 BIOMETRIC TECHNOLOGY WITH PIN
13.2.4 SMART CARD WITH BIOMETRIC TECHNOLOGY
13.2.5 OTHERS
13.3 IT AND TELECOMMUNICATION
13.3.1 SMART CARD WITH PIN
13.3.2 ONE TIME PASSWORD WITH PIN
13.3.3 BIOMETRIC TECHNOLOGY WITH PIN
13.3.4 SMART CARD WITH BIOMETRIC TECHNOLOGY
13.3.5 OTHERS
13.4 E COMMERCE
13.4.1 SMART CARD WITH PIN
13.4.2 ONE TIME PASSWORD WITH PIN
13.4.3 BIOMETRIC TECHNOLOGY WITH PIN
13.4.4 SMART CARD WITH BIOMETRIC TECHNOLOGY
13.4.5 OTHERS
13.5 MEDIA AND ENTERTAINMENT
13.5.1 SMART CARD WITH PIN
13.5.2 ONE TIME PASSWORD WITH PIN
13.5.3 BIOMETRIC TECHNOLOGY WITH PIN
13.5.4 SMART CARD WITH BIOMETRIC TECHNOLOGY
13.5.5 OTHERS
13.6 HOSPITALITY
13.6.1 SMART CARD WITH PIN
13.6.2 ONE TIME PASSWORD WITH PIN
13.6.3 BIOMETRIC TECHNOLOGY WITH PIN
13.6.4 SMART CARD WITH BIOMETRIC TECHNOLOGY
13.6.5 OTHERS
13.7 GAMING
13.7.1 SMART CARD WITH PIN
13.7.2 ONE TIME PASSWORD WITH PIN
13.7.3 BIOMETRIC TECHNOLOGY WITH PIN
13.7.4 SMART CARD WITH BIOMETRIC TECHNOLOGY
13.7.5 OTHERS
13.8 EDUCATION
13.8.1 SMART CARD WITH PIN
13.8.2 ONE TIME PASSWORD WITH PIN
13.8.3 BIOMETRIC TECHNOLOGY WITH PIN
13.8.4 SMART CARD WITH BIOMETRIC TECHNOLOGY
13.8.5 OTHERS
13.9 MANUFACTURING
13.9.1 SMART CARD WITH PIN
13.9.2 ONE TIME PASSWORD WITH PIN
13.9.3 BIOMETRIC TECHNOLOGY WITH PIN
13.9.4 SMART CARD WITH BIOMETRIC TECHNOLOGY
13.9.5 OTHERS
13.1 GOVERNMENT AND DEFENCE
13.10.1 SMART CARD WITH PIN
13.10.2 ONE TIME PASSWORD WITH PIN
13.10.3 BIOMETRIC TECHNOLOGY WITH PIN
13.10.4 SMART CARD WITH BIOMETRIC TECHNOLOGY
13.10.5 OTHERS
13.11 MILITARY & DEFENSE
13.11.1 SMART CARD WITH PIN
13.11.2 ONE TIME PASSWORD WITH PIN
13.11.3 BIOMETRIC TECHNOLOGY WITH PIN
13.11.4 SMART CARD WITH BIOMETRIC TECHNOLOGY
13.11.5 OTHERS
13.12 COMMERCIAL SECURITY
13.12.1 SMART CARD WITH PIN
13.12.2 ONE TIME PASSWORD WITH PIN
13.12.3 BIOMETRIC TECHNOLOGY WITH PIN
13.12.4 SMART CARD WITH BIOMETRIC TECHNOLOGY
13.12.5 OTHERS
13.13 TRAVEL & IMMIGRATION
13.13.1 SMART CARD WITH PIN
13.13.2 ONE TIME PASSWORD WITH PIN
13.13.3 BIOMETRIC TECHNOLOGY WITH PIN
13.13.4 SMART CARD WITH BIOMETRIC TECHNOLOGY
13.13.5 OTHERS
13.14 HEALTHCARE
13.14.1 SMART CARD WITH PIN
13.14.2 ONE TIME PASSWORD WITH PIN
13.14.3 BIOMETRIC TECHNOLOGY WITH PIN
13.14.4 SMART CARD WITH BIOMETRIC TECHNOLOGY
13.14.5 OTHERS
13.15 CONSUMER ELECTRONICS
13.15.1 SMART CARD WITH PIN
13.15.2 ONE TIME PASSWORD WITH PIN
13.15.3 BIOMETRIC TECHNOLOGY WITH PIN
13.15.4 SMART CARD WITH BIOMETRIC TECHNOLOGY
13.15.5 OTHERS
13.16 AEROSPACE
13.16.1 SMART CARD WITH PIN
13.16.2 ONE TIME PASSWORD WITH PIN
13.16.3 BIOMETRIC TECHNOLOGY WITH PIN
13.16.4 SMART CARD WITH BIOMETRIC TECHNOLOGY
13.16.5 OTHERS
13.17 OTHERS
14 GLOBAL TWO-FACTOR AUTHENTICATION MARKET, BY REGION
GLOBAL TWO-FACTOR AUTHENTICATION MARKET, (ALL SEGMENTATION PROVIDED ABOVE IS REPRESENTED IN THIS CHAPTER BY COUNTRY)
14.1 NORTH AMERICA
14.1.1 U.S.
14.1.2 CANADA
14.1.3 MEXICO
14.2 EUROPE
14.2.1 GERMANY
14.2.2 FRANCE
14.2.3 U.K.
14.2.4 ITALY
14.2.5 SPAIN
14.2.6 RUSSIA
14.2.7 TURKEY
14.2.8 BELGIUM
14.2.9 NETHERLANDS
14.2.10 SWITZERLAND
14.2.11 REST OF EUROPE
14.3 ASIA-PACIFIC
14.3.1 JAPAN
14.3.2 CHINA
14.3.3 SOUTH KOREA
14.3.4 INDIA
14.3.5 AUSTRALIA
14.3.6 SINGAPORE
14.3.7 THAILAND
14.3.8 MALAYSIA
14.3.9 INDONESIA
14.3.10 PHILIPPINES
14.3.11 REST OF ASIA-PACIFIC
14.4 LATIN AMERICA
14.4.1 BRAZIL
14.4.2 ARGENTINA
14.4.3 COLOMBIA
14.4.4 CHILE
14.4.5 PERU
14.4.6 ECUADOR
14.4.7 GUATEMALA
14.4.8 PANAMA
14.4.9 PARAGUAY
14.4.10 BOLIVIA
14.4.11 REST OF SOUTH AMERICA
14.5 MIDDLE EAST AND AFRICA
14.5.1 SOUTH AFRICA
14.5.2 UAE
14.5.3 EGYPT
14.5.4 ISRAEL
14.5.5 SAUDI ARABIA
14.5.6 REST OF MIDDLE EAST AND AFRICA
14.6 KEY PRIMARY INSIGHTS: BY MAJOR COUNTRIES
15 GLOBAL TWO-FACTOR AUTHENTICATION MARKET, COMPANY LANDSCAPE
15.1 COMPANY SHARE ANALYSIS: GLOBAL
15.2 COMPANY SHARE ANALYSIS: NORTH AMERICA
15.3 COMPANY SHARE ANALYSIS: EUROPE
15.4 COMPANY SHARE ANALYSIS: ASIA-PACIFIC
15.5 MERGERS & ACQUISITIONS
15.6 NEW PRODUCT DEVELOPMENT & APPROVALS
15.7 EXPANSIONS
15.8 REGULATORY CHANGES
15.9 PARTNERSHIP AND OTHER STRATEGIC DEVELOPMENTS
16 GLOBAL TWO-FACTOR AUTHENTICATION MARKET, COMPANY PROFILE
16.1 GEMALTO NV
16.1.1 COMPANY OVERVIEW
16.1.2 COMPANY SNAPSHOT
16.1.3 REVENUE ANALYSIS
16.1.4 PRODUCT PORTFOLIO
16.1.5 RECENT DEVELOPMENTS
16.2 FUJITSU LTD
16.2.1 COMPANY OVERVIEW
16.2.2 COMPANY SNAPSHOT
16.2.3 REVENUE ANALYSIS
16.2.4 PRODUCT PORTFOLIO
16.2.5 RECENT DEVELOPMENTS
16.3 SUPREMA INC.
16.3.1 COMPANY OVERVIEW
16.3.2 COMPANY SNAPSHOT
16.3.3 REVENUE ANALYSIS
16.3.4 PRODUCT PORTFOLIO
16.3.5 RECENT DEVELOPMENTS
16.4 ONESPAN INC.
16.4.1 COMPANY OVERVIEW
16.4.2 COMPANY SNAPSHOT
16.4.3 REVENUE ANALYSIS
16.4.4 PRODUCT PORTFOLIO
16.4.5 RECENT DEVELOPMENTS
16.5 NEC CORPORATION
16.5.1 COMPANY OVERVIEW
16.5.2 COMPANY SNAPSHOT
16.5.3 REVENUE ANALYSIS
16.5.4 PRODUCT PORTFOLIO
16.5.5 RECENT DEVELOPMENTS
16.6 SYMANTEC CORPORATION
16.6.1 COMPANY OVERVIEW
16.6.2 COMPANY SNAPSHOT
16.6.3 REVENUE ANALYSIS
16.6.4 PRODUCT PORTFOLIO
16.6.5 RECENT DEVELOPMENTS
16.7 RSA SECURITY LLC
16.7.1 COMPANY OVERVIEW
16.7.2 COMPANY SNAPSHOT
16.7.3 REVENUE ANALYSIS
16.7.4 PRODUCT PORTFOLIO
16.7.5 RECENT DEVELOPMENTS
16.8 IDEMIA
16.8.1 COMPANY OVERVIEW
16.8.2 COMPANY SNAPSHOT
16.8.3 REVENUE ANALYSIS
16.8.4 PRODUCT PORTFOLIO
16.8.5 RECENT DEVELOPMENTS
16.9 `
16.1 HID GLOBAL CORPORATION
16.10.1 COMPANY OVERVIEW
16.10.2 COMPANY SNAPSHOT
16.10.3 REVENUE ANALYSIS
16.10.4 PRODUCT PORTFOLIO
16.10.5 RECENT DEVELOPMENTS
16.11 CA INC.
16.11.1 COMPANY OVERVIEW
16.11.2 COMPANY SNAPSHOT
16.11.3 REVENUE ANALYSIS
16.11.4 PRODUCT PORTFOLIO
16.11.5 RECENT DEVELOPMENTS
16.12 GOOGLE LLC
16.12.1 COMPANY OVERVIEW
16.12.2 COMPANY SNAPSHOT
16.12.3 REVENUE ANALYSIS
16.12.4 PRODUCT PORTFOLIO
16.12.5 RECENT DEVELOPMENTS
16.13 SAFRAN
16.13.1 COMPANY OVERVIEW
16.13.2 COMPANY SNAPSHOT
16.13.3 REVENUE ANALYSIS
16.13.4 PRODUCT PORTFOLIO
16.13.5 RECENT DEVELOPMENTS
16.14 NEC CORPORATION
16.14.1 COMPANY OVERVIEW
16.14.2 COMPANY SNAPSHOT
16.14.3 REVENUE ANALYSIS
16.14.4 PRODUCT PORTFOLIO
16.14.5 RECENT DEVELOPMENTS
16.15 RSA SECURITY LLC
16.15.1 COMPANY OVERVIEW
16.15.2 COMPANY SNAPSHOT
16.15.3 REVENUE ANALYSIS
16.15.4 PRODUCT PORTFOLIO
16.15.5 RECENT DEVELOPMENTS
16.16 HID GLOBAL CORPORATION
16.16.1 COMPANY OVERVIEW
16.16.2 COMPANY SNAPSHOT
16.16.3 REVENUE ANALYSIS
16.16.4 PRODUCT PORTFOLIO
16.16.5 RECENT DEVELOPMENTS
16.17 ASSA ABLOY AB
16.17.1 COMPANY OVERVIEW
16.17.2 COMPANY SNAPSHOT
16.17.3 REVENUE ANALYSIS
16.17.4 PRODUCT PORTFOLIO
16.17.5 RECENT DEVELOPMENTS
16.18 3M
16.18.1 COMPANY OVERVIEW
16.18.2 COMPANY SNAPSHOT
16.18.3 REVENUE ANALYSIS
16.18.4 PRODUCT PORTFOLIO
16.18.5 RECENT DEVELOPMENTS
16.19 CA TECHNOLOGIES
16.19.1 COMPANY OVERVIEW
16.19.2 COMPANY SNAPSHOT
16.19.3 REVENUE ANALYSIS
16.19.4 PRODUCT PORTFOLIO
16.19.5 RECENT DEVELOPMENTS
16.2 FUJITSU
16.20.1 COMPANY OVERVIEW
16.20.2 COMPANY SNAPSHOT
16.20.3 REVENUE ANALYSIS
16.20.4 PRODUCT PORTFOLIO
16.20.5 RECENT DEVELOPMENTS
16.21 VASCO DATA SECURITY INTERNATIONAL, INC.
16.21.1 COMPANY OVERVIEW
16.21.2 COMPANY SNAPSHOT
16.21.3 REVENUE ANALYSIS
16.21.4 PRODUCT PORTFOLIO
16.21.5 RECENT DEVELOPMENTS
16.22 SUPREMA INC.
16.22.1 COMPANY OVERVIEW
16.22.2 COMPANY SNAPSHOT
16.22.3 REVENUE ANALYSIS
16.22.4 PRODUCT PORTFOLIO
16.22.5 RECENT DEVELOPMENTS
16.23 CROSSMATCH
16.23.1 COMPANY OVERVIEW
16.23.2 COMPANY SNAPSHOT
16.23.3 REVENUE ANALYSIS
16.23.4 PRODUCT PORTFOLIO
16.23.5 RECENT DEVELOPMENTS
16.24 APERSONA, INC.
16.24.1 COMPANY OVERVIEW
16.24.2 COMPANY SNAPSHOT
16.24.3 REVENUE ANALYSIS
16.24.4 PRODUCT PORTFOLIO
16.24.5 RECENT DEVELOPMENTS
16.25 BIOMIO
16.25.1 COMPANY OVERVIEW
16.25.2 COMPANY SNAPSHOT
16.25.3 REVENUE ANALYSIS
16.25.4 PRODUCT PORTFOLIO
16.25.5 RECENT DEVELOPMENTS
16.26 IOVATION INC.
16.26.1 COMPANY OVERVIEW
16.26.2 COMPANY SNAPSHOT
16.26.3 REVENUE ANALYSIS
16.26.4 PRODUCT PORTFOLIO
16.26.5 RECENT DEVELOPMENTS
16.27 ZK SOFTWARE
16.27.1 COMPANY OVERVIEW
16.27.2 COMPANY SNAPSHOT
16.27.3 REVENUE ANALYSIS
16.27.4 PRODUCT PORTFOLIO
16.27.5 RECENT DEVELOPMENTS
*NOTE: THE COMPANIES PROFILED IS NOT EXHAUSTIVE LIST AND IS AS PER OUR PREVIOUS CLIENT REQUIREMENT. WE PROFILE MORE THAN 100 COMPANIES IN OUR STUDY AND HENCE THE LIST OF COMPANIES CAN BE MODIFIED OR REPLACED ON REQUEST
17 RELATED REPORTS
18 QUESTIONNAIRE
19 ABOUT DATA BRIDGE MARKET RESEARCH
Global Two Factor Authentication Market, Supply Chain Analysis and Ecosystem Framework
To support market growth and help clients navigate the impact of geopolitical shifts, DBMR has integrated in-depth supply chain analysis into its Global Two Factor Authentication Market research reports. This addition empowers clients to respond effectively to global changes affecting their industries. The supply chain analysis section includes detailed insights such as Global Two Factor Authentication Market consumption and production by country, price trend analysis, the impact of tariffs and geopolitical developments, and import and export trends by country and HSN code. It also highlights major suppliers with data on production capacity and company profiles, as well as key importers and exporters. In addition to research, DBMR offers specialized supply chain consulting services backed by over a decade of experience, providing solutions like supplier discovery, supplier risk assessment, price trend analysis, impact evaluation of inflation and trade route changes, and comprehensive market trend analysis.
Research Methodology
Data collection and base year analysis are done using data collection modules with large sample sizes. The stage includes obtaining market information or related data through various sources and strategies. It includes examining and planning all the data acquired from the past in advance. It likewise envelops the examination of information inconsistencies seen across different information sources. The market data is analysed and estimated using market statistical and coherent models. Also, market share analysis and key trend analysis are the major success factors in the market report. To know more, please request an analyst call or drop down your inquiry.
The key research methodology used by DBMR research team is data triangulation which involves data mining, analysis of the impact of data variables on the market and primary (industry expert) validation. Data models include Vendor Positioning Grid, Market Time Line Analysis, Market Overview and Guide, Company Positioning Grid, Patent Analysis, Pricing Analysis, Company Market Share Analysis, Standards of Measurement, Global versus Regional and Vendor Share Analysis. To know more about the research methodology, drop in an inquiry to speak to our industry experts.
Customization Available
Data Bridge Market Research is a leader in advanced formative research. We take pride in servicing our existing and new customers with data and analysis that match and suits their goal. The report can be customized to include price trend analysis of target brands understanding the market for additional countries (ask for the list of countries), clinical trial results data, literature review, refurbished market and product base analysis. Market analysis of target competitors can be analyzed from technology-based analysis to market portfolio strategies. We can add as many competitors that you require data about in the format and data style you are looking for. Our team of analysts can also provide you data in crude raw excel files pivot tables (Fact book) or can assist you in creating presentations from the data sets available in the report.