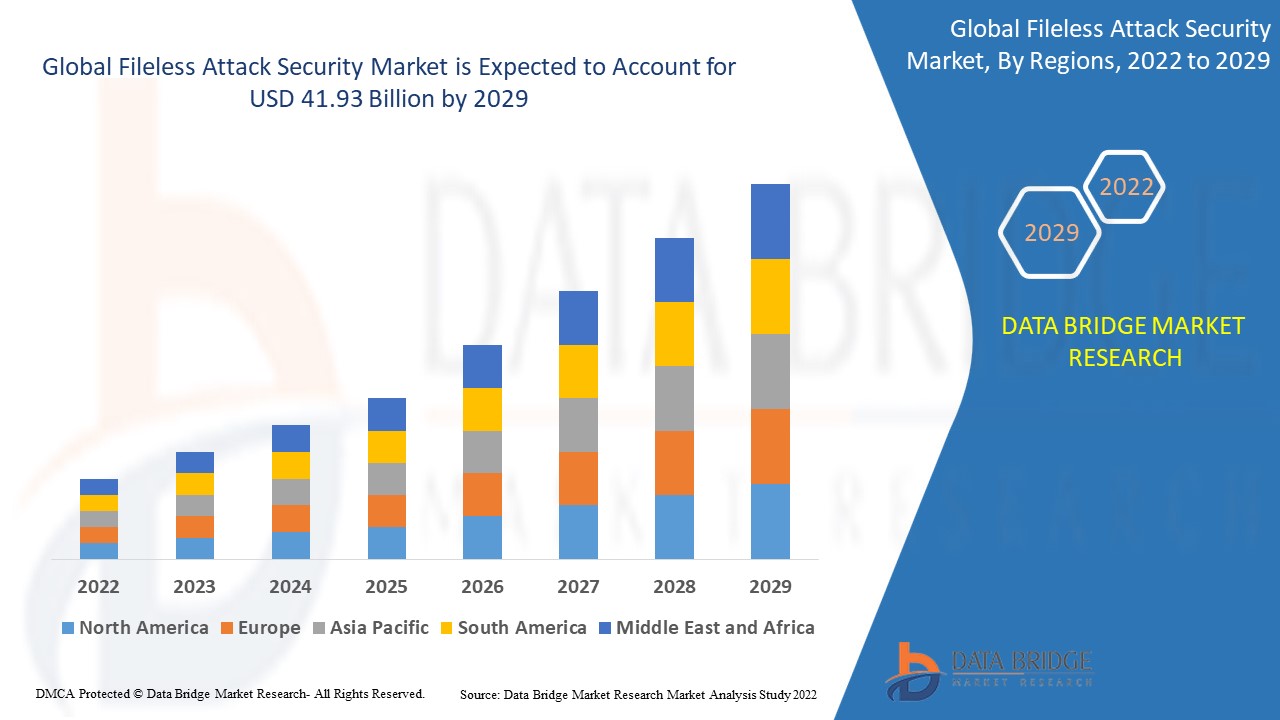
Global Fileless Attack Security Market
Market Size in USD Billion
CAGR :
% 
 USD
16.46 Billion
USD
41.93 Billion
2021
2029
USD
16.46 Billion
USD
41.93 Billion
2021
2029
| 2022 –2029 | |
| USD 16.46 Billion | |
| USD 41.93 Billion | |
|
|
|
|
Fileless Attack Security Market Analysis and Size
Increasing cyber-attacks and hacker threats, digital transformation, compliance, privacy and data protection, and so on. Furthermore, a growing number of security attacks now include fileless attacks, a trend that is expected to intensify in 2022.
Data Bridge Market Research analyses that the fileless attack security market was valued at USD 16.46 billion in 2021 and is expected to reach the value of USD 41.93 billion by 2029, at a CAGR of 12.40% during the forecast period. In addition to the market insights such as market value, growth rate, market segments, geographical coverage, market players, and market scenario, the market report curated by the Data Bridge Market Research team includes in-depth expert analysis, import/export analysis, pricing analysis, production consumption analysis, and pestle analysis.
Fileless Attack Security Market Scope and Segmentation
|
Report Metric |
Details |
|
Forecast Period |
2022 to 2029 |
|
Base Year |
2021 |
|
Historic Years |
2020 (Customizable to 2014 - 2019) |
|
Quantitative Units |
Revenue in USD billion, Volumes in Units, Pricing in USD |
|
Segments Covered |
Type (Macros, Scripts, In Memory, Others), Attack Technique (Memory-Only Threats, Fileless Persistence Methods, Dual-Use Tools, Non-Portable Executable (PE) File Attacks), Security Technology (Endpoint Security, Endpoint Detection and Response (EDR), Email Security, Network Security, Others), Application (PowerShell, Windows Management Instrumentation (WMI), Others), End User (Aerospace, Defense, Government, Banking, Financial Institutions, Information Technology (IT), Telecom, Healthcare, Retail, E-Commerce, Education, Others) |
|
Countries Covered |
U.S., Canada and Mexico in North America, Germany, France, U.K., Netherlands, Switzerland, Belgium, Russia, Italy, Spain, Turkey, Rest of Europe in Europe, China, Japan, India, South Korea, Singapore, Malaysia, Australia, Thailand, Indonesia, Philippines, Rest of Asia-Pacific (APAC) in the Asia-Pacific (APAC), Saudi Arabia, U.A.E, South Africa, Egypt, Israel, Rest of Middle East and Africa (MEA) as a part of Middle East and Africa (MEA), Brazil, Argentina and Rest of South America as part of South America |
|
Market Players Covered |
Digi-key Electronics (U.S.), Brewer Science, Inc. (U.S.), DuPont (U.S.), Murata Manufacturing Co., Ltd (Japan), MTS Systems Corporation (U.S.) Interlink Electronics, Inc. (U.S.), Emerson Electric Co (U.S.), Thin Film Electronics ASA (Norway), ISORG (France), Peratech Holdco Ltd (U.K.), Honeywell International Inc (U.S.), TE connectivity (Switzerland), SpotSee (U.S.), KWJ Engineering Inc., (U.S.), Fujifilm Holding Corporation (Japan), Interlink Electronics, Inc. (U.S.) and Tekscan, Inc. (U.S.) |
|
Market Opportunities |
|
Market Definition
Unlike traditional malware, fileless malware attacks do not necessitate programmers introducing programming on a target machine. In reality, programmers take over devices built into Windows and use them to carry out attacks. Fileless malware attacks Windows devices, specifically PowerShell and Windows Management Instrumentation (WMI), and uses them for malicious purposes such as exchanging data with other machines.
Global Fileless Attack Security Market Dynamics
Drivers
- Rising prevalence of cyber-attacks
Recently, there has been an upsurge in the use of targeted attacks to get into targets' network infrastructure while remaining anonymous. Attackers frequently target endpoints, networks, on-premises devices, cloud-based applications, data, and other IT infrastructure. Gaining access to the targeted businesses or organisations and stealing sensitive data is the main objective of targeted attacks. These focused attacks on an enterprise's most vital activities have detrimental effects on business, intellectual property, finances, and the loss of sensitive consumer information..
- Growing requirement of cloud deployment
By deploying them on-premises, organizations may gain more control over all big data security solutions, including next-generation firewalls and intrusion prevention systems. Enterprises profit from the speed, scalability, and increased IT security that cloud deployment models for big data security solutions offer. Cloud-based big data security solutions are in greater demand among SMEs and large companies as more applications are supplied through the cloud. Furthermore, improved security measures and increased cybersecurity awareness will accelerate overall market growth during the forecast period. Again, the increasing volume of business data generated from multiple sources is expected to drive the fileless attack security market's growth rate.
Opportunity
The increased adoption of artificial intelligence (AI) and machine language (ML) based applications will provide various growth opportunities to the market. As they strive to secure information using algorithms, AI and ML can learn about how certain risks are classified. These technologies can quickly examine the system's strange behaviour and determine whether or not those anomalies qualify as potential dangers by employing such methods.
Restraints
Lack of skilled and trained personnel and privacy concerns are acting as market restraints for fileless attack security during the forecasted period.
This fileless attack security market report provides details of new recent developments, trade regulations, import-export analysis, production analysis, value chain optimization, market share, impact of domestic and localized market players, analyses opportunities in terms of emerging revenue pockets, changes in market regulations, strategic market growth analysis, market size, category market growths, application niches and dominance, product approvals, product launches, geographic expansions, technological innovations in the market. To gain more info on the fileless attack security market contact Data Bridge Market Research for an Analyst Brief, our team will help you take an informed market decision to achieve market growth.
COVID-19 Impact on Fileless Attack Security Market
The COVID-19 outbreak had a significant impact on the fileless attack security market. During the COVID-19 pandemic, numerous governments and regulatory bodies have mandated that public and private enterprises adopt new methods for working remotely and maintaining social distance. Since then, many companies' new Business Continuity Plans (BCPs) have been based on digital business methods. Due to the widespread use of BYOD devices, the WFH trend, and internet penetration in every part of the world, people are increasingly inclined to adopt digital technologies such as cloud solutions, fuelling the demand for fileless attack security measures to fend off cyberattacks. Endpoint and network security are in high demand to maintain strong security practises and policies in the face of the COVID-19 pandemic.
Recent Developments
In 2021, To unify and improve threat detection for Fileless Attack Security, McAfee Corp. has released MVISION Extended Detection and Response (XDR), which includes network telemetry and the cloud. This will provide easier, automated response, quicker, more proactive investigation cycles, and continuing modernization of security operations centres today (SOC).
Global Fileless Attack Security Market Scope
The fileless attack security market is segmented on the basis of type, attack technique, security technology, application and end user. The growth amongst these segments will help you analyse meagre growth segments in the industries and provide the users with a valuable market overview and market insights to help them make strategic decisions for identifying core market applications.
Type
- Macros
- Scripts
- In Memory
- Others
End user
- Aerospace
- Defence
- Government
- Banking
- Financial Institutions
- Information Technology (IT)
- Telecom
- Healthcare
- Retail
- E-Commerce
- Education
- Others
Attack technique
- Memory-Only Threats
- Fileless Persistence Methods
- Dual-Use Tools
- Non-Portable Executable (PE) File Attacks
Security technology
- Endpoint Security
- Endpoint Detection and Response (EDR)
- Email Security
- Network Security
- Others
Application
- PowerShell
- Windows Management Instrumentation (WMI)
- Others
Fileless Attack Security Market Regional Analysis/Insights
The fileless attack security market is analysed and market size insights and trends are provided by country, type, attack technique, security technology, application and end user as referenced above.
The countries covered in the fileless attack security market report are U.S., Canada and Mexico in North America, Germany, France, U.K., Netherlands, Switzerland, Belgium, Russia, Italy, Spain, Turkey, Rest of Europe in Europe, China, Japan, India, South Korea, Singapore, Malaysia, Australia, Thailand, Indonesia, Philippines, Rest of Asia-Pacific (APAC) in the Asia-Pacific (APAC), Saudi Arabia, U.A.E, South Africa, Egypt, Israel, Rest of Middle East and Africa (MEA) as a part of Middle East and Africa (MEA), Brazil, Argentina and Rest of South America as part of South America.
The country section of the report also provides individual market impacting factors and changes in market regulation that impact the current and future trends of the market. Data points like down-stream and upstream value chain analysis, technical trends and porter's five forces analysis, case studies are some of the pointers used to forecast the market scenario for individual countries. Also, the presence and availability of Global brands and their challenges faced due to large or scarce competition from local and domestic brands, impact of domestic tariffs and trade routes are considered while providing forecast analysis of the country data.
Competitive Landscape and Fileless Attack Security Market Share Analysis
The fileless attack security market competitive landscape provides details by competitor. Details included are company overview, company financials, revenue generated, market potential, investment in research and development, new market initiatives, Global presence, production sites and facilities, production capacities, company strengths and weaknesses, product launch, product width and breadth, application dominance. The above data points provided are only related to the companies' focus related to fileless attack security market.
Some of the major players operating in the fileless attack security market are:
- Digi-key Electronics (U.S.)
- Brewer Science, Inc. (U.S.)
- DuPont (U.S.)
- Murata Manufacturing Co., Ltd (Japan)
- MTS Systems Corporation (U.S.)
- Interlink Electronics, Inc. (U.S.)
- Emerson Electric Co (U.S.)
- Thin Film Electronics ASA (Norway)
- ISORG (France)
- Peratech Holdco Ltd (U.K.)
- Honeywell International Inc (U.S.)
- TE connectivity (Switzerland)
- SpotSee (U.S.)
- KWJ Engineering Inc., (U.S.)
- Fujifilm Holding Corporation (Japan)
- Interlink Electronics, Inc. (U.S.)
- Tekscan, Inc. (U.S.)
SKU-
Get online access to the report on the World's First Market Intelligence Cloud
- Interactive Data Analysis Dashboard
- Company Analysis Dashboard for high growth potential opportunities
- Research Analyst Access for customization & queries
- Competitor Analysis with Interactive dashboard
- Latest News, Updates & Trend analysis
- Harness the Power of Benchmark Analysis for Comprehensive Competitor Tracking
Table of Content
1 INTRODUCTION
1.1 OBJECTIVES OF THE STUDY
1.2 MARKET DEFINITION
1.3 OVERVIEW OF GLOBAL FILELESS ATTACK SECURITY MARKET
1.4 CURRENCY AND PRICING
1.5 LIMITATION
1.6 MARKETS COVERED
2 MARKET SEGMENTATION
2.1 KEY TAKEAWAYS
2.2 ARRIVING AT THE GLOBAL FILELESS ATTACK SECURITY MARKET
2.3 VENDOR POSITIONING GRID
2.4 TECHNOLOGY LIFE LINE CURVE
2.5 MARKET GUIDE
2.6 MULTIVARIATE MODELLING
2.7 TOP TO BOTTOM ANALYSIS
2.8 STANDARDS OF MEASUREMENT
2.9 VENDOR SHARE ANALYSIS
2.1 DATA POINTS FROM KEY PRIMARY INTERVIEWS
2.11 DATA POINTS FROM KEY SECONDARY DATABASES
2.12 GLOBAL FILELESS ATTACK SECURITY MARKET: RESEARCH SNAPSHOT
2.13 ASSUMPTIONS
3 MARKET OVERVIEW
3.1 DRIVERS
3.2 RESTRAINTS
3.3 OPPORTUNITIES
3.4 CHALLENGES
4 EXECUTIVE SUMMARY
5 PREMIUM INSIGHTS
5.1 VALUE CHAIN ANALYSIS
5.2 BRAND ANALYSIS
5.3 ECOSYSTEM MARKET MAP
5.4 TECHNOLOGICAL TRENDS
5.5 TOP WINNING STRATEGIES
5.6 PORTER’S FIVE FORCES ANALYSIS
6 GLOBAL FILELESS ATTACK SECURITY MARKET, BY TYPE
6.1 OVERVIEW
6.2 MACROS
6.3 IN MEMORY
6.4 SCRIPTS
6.5 OTHERS
7 GLOBAL FILELESS ATTACK SECURITY MARKET, BY SECURITY TECHNOLOGIES
7.1 OVERVIEW
7.2 ENDPOINT SECURITY
7.2.1 MULTILAYERED SECURITY ENGINES
7.2.2 SYSTEM HARDENING
7.2.3 DECEPTION
7.3 ENDPOINT DETECTION & RESPONSE (EDR)
7.4 EMAIL SECURITY
7.5 NETWORK SECURITY
7.6 OTHERS
8 GLOBAL FILELESS ATTACK SECURITY MARKET, BY ATTACK TECHNOLOGY
8.1 OVERVIEW
8.2 MEMORY-ONLY THREATS
8.3 DUAL-USE TOOLS
8.4 FILELESS PERSISTENCE METHODS
8.5 NON-PORTABLE EXECUTABLE (PE) FILE ATTACKS
8.6 OTHERS
9 GLOBAL FILELESS ATTACK SECURITY MARKET, BY APPLICATION
9.1 OVERVIEW
9.2 AEROSPACE & DEFENSE
9.2.1 BY TYPE
9.2.1.1. MACROS
9.2.1.2. IN MEMORY
9.2.1.3. SCRIPTS
9.2.1.4. OTHERS
9.3 BFSI
9.3.1 BY TYPE
9.3.1.1. MACROS
9.3.1.2. IN MEMORY
9.3.1.3. SCRIPTS
9.3.1.4. OTHERS
9.4 GOVERNMENT
9.4.1 BY TYPE
9.4.1.1. MACROS
9.4.1.2. IN MEMORY
9.4.1.3. SCRIPTS
9.4.1.4. OTHERS
9.5 IT & TELECOM
9.5.1 BY TYPE
9.5.1.1. MACROS
9.5.1.2. IN MEMORY
9.5.1.3. SCRIPTS
9.5.1.4. OTHERS
9.6 HEALTHCARE
9.6.1 BY TYPE
9.6.1.1. MACROS
9.6.1.2. IN MEMORY
9.6.1.3. SCRIPTS
9.6.1.4. OTHERS
9.7 RETAIL
9.7.1 BY TYPE
9.7.1.1. MACROS
9.7.1.2. IN MEMORY
9.7.1.3. SCRIPTS
9.7.1.4. OTHERS
9.8 E-COMMERCE
9.8.1 BY TYPE
9.8.1.1. MACROS
9.8.1.2. IN MEMORY
9.8.1.3. SCRIPTS
9.8.1.4. OTHERS
9.9 EDUCATION
9.9.1 BY TYPE
9.9.1.1. MACROS
9.9.1.2. IN MEMORY
9.9.1.3. SCRIPTS
9.9.1.4. OTHERS
9.1 OTHERS
9.10.1 BY TYPE
9.10.1.1. MACROS
9.10.1.2. IN MEMORY
9.10.1.3. SCRIPTS
9.10.1.4. OTHERS
10 GLOBAL FILELESS ATTACK SECURITY MARKET, BY REGION
Global FILELESS ATTACK SECURITY Market, (ALL SEGMENTATION PROVIDED ABOVE IS REPRESENTED IN THIS CHAPTER BY COUNTRY)
10.1 NORTH AMERICA
10.1.1 U.S.
10.1.2 CANADA
10.1.3 MEXICO
10.2 EUROPE
10.2.1 GERMANY
10.2.2 FRANCE
10.2.3 U.K.
10.2.4 ITALY
10.2.5 SPAIN
10.2.6 RUSSIA
10.2.7 TURKEY
10.2.8 BELGIUM
10.2.9 NETHERLANDS
10.2.10 SWITZERLAND
10.2.11 DENMARK
10.2.12 SWEDEN
10.2.13 POLAND
10.2.14 NORWAY
10.2.15 FINLAND
10.2.16 REST OF EUROPE
10.3 ASIA PACIFIC
10.3.1 JAPAN
10.3.2 CHINA
10.3.3 SOUTH KOREA
10.3.4 INDIA
10.3.5 AUSTRALIA
10.3.6 SINGAPORE
10.3.7 THAILAND
10.3.8 MALAYSIA
10.3.9 INDONESIA
10.3.10 PHILIPPINES
10.3.11 NEW ZEALAND
10.3.12 TAIWAN
10.3.13 VIETNAM
10.3.14 REST OF ASIA PACIFIC
10.4 SOUTH AMERICA
10.4.1 BRAZIL
10.4.2 ARGENTINA
10.4.3 REST OF SOUTH AMERICA
10.5 MIDDLE EAST AND AFRICA
10.5.1 SOUTH AFRICA
10.5.2 EGYPT
10.5.3 BAHRAIN
10.5.4 QATAR
10.5.5 KUWAIT
10.5.6 OMAN
10.5.7 SAUDI ARABIA
10.5.8 U.A.E
10.5.9 ISRAEL
10.5.10 REST OF MIDDLE EAST AND AFRICA
10.6 KEY PRIMARY INSIGHTS: BY MAJOR COUNTRIES
11 GLOBAL FILELESS ATTACK SECURITY MARKET, COMPANY LANDSCAPE
11.1 COMPANY SHARE ANALYSIS: NORTH AMERICA
11.2 COMPANY SHARE ANALYSIS: EUROPE
11.3 COMPANY SHARE ANALYSIS: ASIA-PACIFIC
11.4 MERGERS & ACQUISITIONS
11.5 NEW PRODUCT DEVELOPMENT & APPROVALS
11.6 EXPANSIONS
11.7 REGULATORY CHANGES
11.8 PARTNERSHIP AND OTHER STRATEGIC DEVELOPMENTS
12 GLOBAL FILELESS ATTACK SECURITY MARKET, SWOT ANALYSIS
13 GLOBAL FILELESS ATTACK SECURITY MARKET, COMPANY PROFILE
13.1 AMAZON WEB SERVICES
13.1.1 COMPANY SNAPSHOT
13.1.2 REVENUE ANALYSIS
13.1.3 GEOGRAPHIC PRESENCE
13.1.4 PRODUCT PORTFOLIO
13.1.5 RECENT DEVELOPMENTS
13.2 TATA CONSULTANCY SERVICES
13.2.1 COMPANY SNAPSHOT
13.2.2 REVENUE ANALYSIS
13.2.3 GEOGRAPHIC PRESENCE
13.2.4 PRODUCT PORTFOLIO
13.2.5 RECENT DEVELOPMENTS
13.3 MICROSOFT
13.3.1 COMPANY SNAPSHOT
13.3.2 REVENUE ANALYSIS
13.3.3 GEOGRAPHIC PRESENCE
13.3.4 PRODUCT PORTFOLIO
13.3.5 RECENT DEVELOPMENTS
13.4 MICRO FOCUS
13.4.1 COMPANY SNAPSHOT
13.4.2 REVENUE ANALYSIS
13.4.3 GEOGRAPHIC PRESENCE
13.4.4 PRODUCT PORTFOLIO
13.4.5 RECENT DEVELOPMENTS
13.5 F-SECURE
13.5.1 COMPANY SNAPSHOT
13.5.2 REVENUE ANALYSIS
13.5.3 GEOGRAPHIC PRESENCE
13.5.4 PRODUCT PORTFOLIO
13.5.5 RECENT DEVELOPMENTS
13.6 MCAFEE
13.6.1 COMPANY SNAPSHOT
13.6.2 REVENUE ANALYSIS
13.6.3 GEOGRAPHIC PRESENCE
13.6.4 PRODUCT PORTFOLIO
13.6.5 RECENT DEVELOPMENTS
13.7 FORTINET, INC
13.7.1 COMPANY SNAPSHOT
13.7.2 REVENUE ANALYSIS
13.7.3 GEOGRAPHIC PRESENCE
13.7.4 PRODUCT PORTFOLIO
13.7.5 RECENT DEVELOPMENTS
13.8 FORCEPOINT
13.8.1 COMPANY SNAPSHOT
13.8.2 REVENUE ANALYSIS
13.8.3 GEOGRAPHIC PRESENCE
13.8.4 PRODUCT PORTFOLIO
13.8.5 RECENT DEVELOPMENTS
13.9 RAPID7
13.9.1 COMPANY SNAPSHOT
13.9.2 REVENUE ANALYSIS
13.9.3 GEOGRAPHIC PRESENCE
13.9.4 PRODUCT PORTFOLIO
13.9.5 RECENT DEVELOPMENTS
13.1 FIREYE, INC
13.10.1 COMPANY SNAPSHOT
13.10.2 REVENUE ANALYSIS
13.10.3 GEOGRAPHIC PRESENCE
13.10.4 PRODUCT PORTFOLIO
13.10.5 RECENT DEVELOPMENTS
13.11 CHECKPOINT SOFTWARE TECHNOLOGIES, LTD
13.11.1 COMPANY SNAPSHOT
13.11.2 REVENUE ANALYSIS
13.11.3 GEOGRAPHIC PRESENCE
13.11.4 PRODUCT PORTFOLIO
13.11.5 RECENT DEVELOPMENTS
13.12 IMPERVA
13.12.1 COMPANY SNAPSHOT
13.12.2 REVENUE ANALYSIS
13.12.3 GEOGRAPHIC PRESENCE
13.12.4 PRODUCT PORTFOLIO
13.12.5 RECENT DEVELOPMENTS
13.13 KASPERSKY LAB
13.13.1 COMPANY SNAPSHOT
13.13.2 REVENUE ANALYSIS
13.13.3 GEOGRAPHIC PRESENCE
13.13.4 PRODUCT PORTFOLIO
13.13.5 RECENT DEVELOPMENTS
13.14 BREWER SCIENCE, INC
13.14.1 COMPANY SNAPSHOT
13.14.2 REVENUE ANALYSIS
13.14.3 GEOGRAPHIC PRESENCE
13.14.4 PRODUCT PORTFOLIO
13.14.5 RECENT DEVELOPMENTS
13.15 INTERLINK ELECTRONICS, INC
13.15.1 COMPANY SNAPSHOT
13.15.2 REVENUE ANALYSIS
13.15.3 GEOGRAPHIC PRESENCE
13.15.4 PRODUCT PORTFOLIO
13.15.5 RECENT DEVELOPMENTS
13.16 MURATA MANUFACTURING CO, LTD
13.16.1 COMPANY SNAPSHOT
13.16.2 REVENUE ANALYSIS
13.16.3 GEOGRAPHIC PRESENCE
13.16.4 PRODUCT PORTFOLIO
13.16.5 RECENT DEVELOPMENTS
13.17 HONEYWELL
13.17.1 COMPANY SNAPSHOT
13.17.2 REVENUE ANALYSIS
13.17.3 GEOGRAPHIC PRESENCE
13.17.4 PRODUCT PORTFOLIO
13.17.5 RECENT DEVELOPMENTS
13.18 TE CONNECTIVITY
13.18.1 COMPANY SNAPSHOT
13.18.2 REVENUE ANALYSIS
13.18.3 GEOGRAPHIC PRESENCE
13.18.4 PRODUCT PORTFOLIO
13.18.5 RECENT DEVELOPMENTS
13.19 THIN FILM ELECTRONICS
13.19.1 COMPANY SNAPSHOT
13.19.2 REVENUE ANALYSIS
13.19.3 GEOGRAPHIC PRESENCE
13.19.4 PRODUCT PORTFOLIO
13.19.5 RECENT DEVELOPMENTS
13.2 MTS SYSTEMS CORPORATION
13.20.1 COMPANY SNAPSHOT
13.20.2 REVENUE ANALYSIS
13.20.3 GEOGRAPHIC PRESENCE
13.20.4 PRODUCT PORTFOLIO
13.20.5 RECENT DEVELOPMENTS
13.21 DIGI-KEY ELECTRONICS
13.21.1 COMPANY SNAPSHOT
13.21.2 REVENUE ANALYSIS
13.21.3 GEOGRAPHIC PRESENCE
13.21.4 PRODUCT PORTFOLIO
13.21.5 RECENT DEVELOPMENTS
13.22 DUPONT
13.22.1 COMPANY SNAPSHOT
13.22.2 REVENUE ANALYSIS
13.22.3 GEOGRAPHIC PRESENCE
13.22.4 PRODUCT PORTFOLIO
13.22.5 RECENT DEVELOPMENTS
13.23 ISORG
13.23.1 COMPANY SNAPSHOT
13.23.2 REVENUE ANALYSIS
13.23.3 GEOGRAPHIC PRESENCE
13.23.4 PRODUCT PORTFOLIO
13.23.5 RECENT DEVELOPMENTS
13.24 QUALYS, INC
13.24.1 COMPANY SNAPSHOT
13.24.2 REVENUE ANALYSIS
13.24.3 GEOGRAPHIC PRESENCE
13.24.4 PRODUCT PORTFOLIO
13.24.5 RECENT DEVELOPMENTS
NOTE: THE COMPANIES PROFILED IS NOT EXHAUSTIVE LIST AND IS AS PER OUR PREVIOUS CLIENT REQUIREMENT. WE PROFILE MORE THAN 100 COMPANIES IN OUR STUDY AND HENCE THE LIST OF COMPANIES CAN BE MODIFIED OR REPLACED ON REQUEST
14 RELATED REPORTS
15 QUESTIONNAIRE
16 ABOUT DATA BRIDGE MARKET RESEARCH
Research Methodology
Data collection and base year analysis are done using data collection modules with large sample sizes. The stage includes obtaining market information or related data through various sources and strategies. It includes examining and planning all the data acquired from the past in advance. It likewise envelops the examination of information inconsistencies seen across different information sources. The market data is analysed and estimated using market statistical and coherent models. Also, market share analysis and key trend analysis are the major success factors in the market report. To know more, please request an analyst call or drop down your inquiry.
The key research methodology used by DBMR research team is data triangulation which involves data mining, analysis of the impact of data variables on the market and primary (industry expert) validation. Data models include Vendor Positioning Grid, Market Time Line Analysis, Market Overview and Guide, Company Positioning Grid, Patent Analysis, Pricing Analysis, Company Market Share Analysis, Standards of Measurement, Global versus Regional and Vendor Share Analysis. To know more about the research methodology, drop in an inquiry to speak to our industry experts.
Customization Available
Data Bridge Market Research is a leader in advanced formative research. We take pride in servicing our existing and new customers with data and analysis that match and suits their goal. The report can be customized to include price trend analysis of target brands understanding the market for additional countries (ask for the list of countries), clinical trial results data, literature review, refurbished market and product base analysis. Market analysis of target competitors can be analyzed from technology-based analysis to market portfolio strategies. We can add as many competitors that you require data about in the format and data style you are looking for. Our team of analysts can also provide you data in crude raw excel files pivot tables (Fact book) or can assist you in creating presentations from the data sets available in the report.