GCC Physical Security Market Analysis and Size
Physical security measures protect buildings and the equipment within. In other words, they barricade trespassers from entering and permit authorized ones to do so. While network and cybersecurity are crucial, guarding against physical security lapses and threats is the only way to ensure the safety of the technology, the data, and any staff or faculty with access to the facility. It offers defense against terrorism, fire, robbery, vandalism, and natural calamities.
Data Bridge Market Research analyses that the physical security market is expected to reach USD 9,259.27 million by 2029, at a CAGR of 9.3% during the forecast period. The physical security market report also comprehensively covers pricing, patent, and technological advancements.
|
Report Metric |
Details |
|
Forecast Period |
2022 to 2029 |
|
Base Year |
2021 |
|
Historic Years |
2020 (Customizable to 2019-2014) |
|
Quantitative Units |
Revenue in USD Million, Pricing in USD |
|
Segments Covered |
By Component (Hardware, Services and Software), Authentication (Single-Factor Authentication, Two-Factor Authentication and Three-Factor Authentication), Deployment Model (On-Premise and Cloud), Enterprise Size (Large Sized Enterprises and Small and Medium-Sized Enterprises), End User (Commercial, Government, Industrial and Residential) |
|
Countries Covered |
Saudi Arabia, U.A.E., Qatar, Oman, Kuwait, and Bahrain |
|
Market Players Covered |
Thales, HID Global Corporation, Bosch Sicherheitssysteme GmbH, Hangzhou Hikvision Digital Technology Co., Ltd., Pelco (A Motorolla Solutions Company), Cisco Systems, Inc., Axis Communications AB, Johnson Controls, Aware, Inc., IDEMIA |
Market Definition
Physical security is a security service that aims to protect personnel, hardware, software, networks, and data from physical actions and events that could cause severe loss to an organization, enterprise, agency, or institution. These security services include protection from fire, flood, natural disasters, burglary, theft, vandalism, and terrorism. Security personnel, CCTV cameras, locks, safety barriers, access control protocols, and other similar tools are all included in its various layers, which incorporate interdependent systems.
GCC Physical Security Market Dynamics
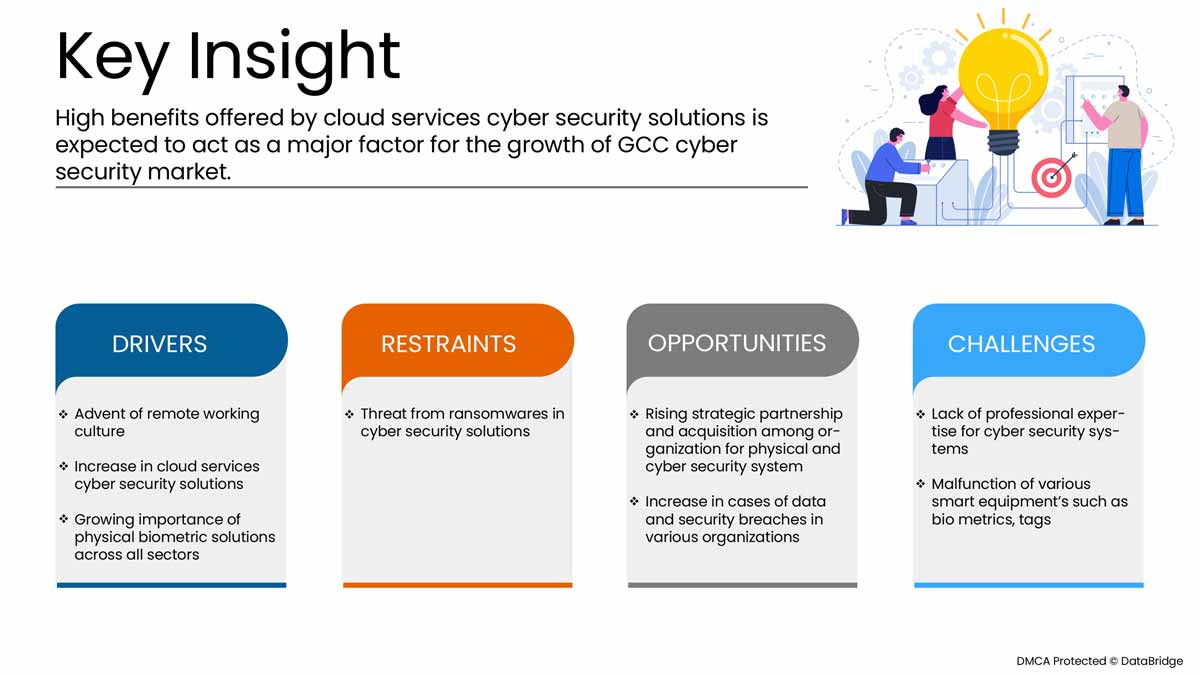
This section deals with understanding the market drivers, advantages, opportunities, restraints, and challenges. All of this is discussed in detail below:
Drivers
- Emergence of smart interconnected building/home
Recently, the popularity of smart homes/buildings has grown among consumers. A smart home/building is a residence that uses internet-connected devices to enable remote monitoring, access control solutions, and management of appliances & systems, such as smart lighting, smart locks, smart biometrics, and others.
Moreover, smart home devices are efficient and energy-saving, reducing energy bill payments. Smart home devices, due to their innovative features, in-built motion detectors, internet connectivity, and control through smartphones, laptops, and other devices, make the consumer feel safe, comfortable, and secure.
- Rapid growth in the importance of physical biometric solutions across all sectors
Biometric-based physical security devices are increasing across all regions of the globe. The fingerprint, physical access control system, video surveillance system, and facial recognition system are integrated with electronic devices such as laptops, mobiles, and other smart handheld devices. The smart approach also uses these access control door locks, security systems, home automation, IoT, automotive, game consoles, and mobile devices.
With an access control door lock, a person can quickly identify and access the house or organization by enhancing security features. The companies are performing many research activities to incorporate the advanced physical biometric system into the devices for security.
Opportunity
- Rise in strategic partnership and acquisition among organizations for physical and cyber security system
Coordinating and investing in projects is essential for achieving sustained improvements in the physical security market. Due to this, the government and other private organizations are striving through partnerships and acquisitions, thereby accelerating the growth of the industries. This helps to build awareness and profit for the organization, thereby creating scope for a new invention in the industry. Also, the company can invest more in advanced technologies to provide more secure and reliable physical security market services and solutions through partnerships.
Expanding the business could connect more people to the company's products and services. They will be able to convert more clients and boost their sales by expanding the customer base. This helps make awareness, increases the organization's profit, and creates scope for sustainable growth. Furthermore, this allows the company to get recognized in the premium market.
Restraints/Challenges
- Rise in cyber security threat and ransomware in physical and cyber security solutions
Due to COVID-19, cybercrime and cybersecurity issues increased by 600% in 2020. Flaws in network security are a weakness that hackers exploit to perform unauthorized actions within a system. According to Purple Sec L.L.C., in 2018, mobile malware variants for mobile have increased by 54% 2018, out of which 98% of mobile malware target Android devices. 25% of businesses are estimated to have been victims of crypto-jacking. Various companies also include the security industry.
- Complexity associated with the integration of various physical security systems
Integrating security systems involves combining logical and physical security applications, such as biometric identity programs and access control, into a single, all-encompassing plan. For instance, if the access control and intrusion alarm systems are linked, the access control system can be programmed to lock down a facility based on the type of alarm sounds when the system determines an intruder. However, one has to buy all the components from the same vendor. If the vendor provides only minimal support, customers could become saddled with a system that does not meet their needs. Also, redesigning and redeploying web- and mobile-based applications can become exhaustive and time-consuming.
Post COVID-19 Impact on GCC Physical Security Market
COVID-19 negatively impacted the physical security market due to lockdown regulations and the shutdown of manufacturing facilities.
The COVID-19 pandemic has impacted the physical security market to an extent positive manner. The surge in demand for video surveillance systems in various industries worldwide has helped the market grow during the pandemic. Also, the growth has been high since the market opened after COVID-19 owing to the increasing adoption of access control protocols in the commercial and industrial environment.
Solution providers are making various strategic decisions to bounce back post-COVID-19. The players are conducting multiple research and development activities to improve the technology involved in physical security. With this, the companies will bring advanced technologies to the market. In addition, government initiatives to use automation technology have led to the market's growth.
Recent Developments
- In October 2021, Honeywell and IDEMIA partnered to develop intelligent building offerings. Under the partnership, products had been set for building access which integrated Honeywell security and building management systems with IDEMIA's biometric-based access control systems. This helped the company diversify its product portfolio and gain a new market in the building access control market
- In August 2020, Motorola Solutions acquired Pelco Corporations for USD 110 million. This acquisition aimed to take the video management solution offered by Pelco international. Further, Motorola Solutions made Pelco Corporation one of the principal subsidiaries in the physical security market. Through this, both companies further enhanced their market presence by offering innovative solutions for the consumer
GCC Physical Security Market Scope
GCC physical security market is segmented on component, authentication, deployment model, enterprise size, and end user. The growth amongst these segments will help you analyse meagre growth segments in the industries and provide the users with a valuable market overview and market insights to help them make strategic decisions for identifying core market applications.
Component
- Hardware
- Services
- Software
On the basis of component, the GCC physical security market is segmented into hardware, services, and software.
Authentication
- Single-factor authentication
- Two-factor authentication
- Three-factor authentication
On the basis of authentication, the GCC physical security market has been segmented into single-factor authentication, two-factor authentication, and three-factor authentication.
Deployment Model
- On-premise
- Cloud
On the basis of deployment model, the GCC physical security market has been segmented into on-premise and cloud.
Enterprise Size
- Large sized enterprises
- Small and medium-sized enterprises
On the basis of enterprise size, the GCC physical security market has been segmented into large sized enterprises and small and medium-sized enterprises.
End User
- Commercial
- Government
- Industrial
- Residential
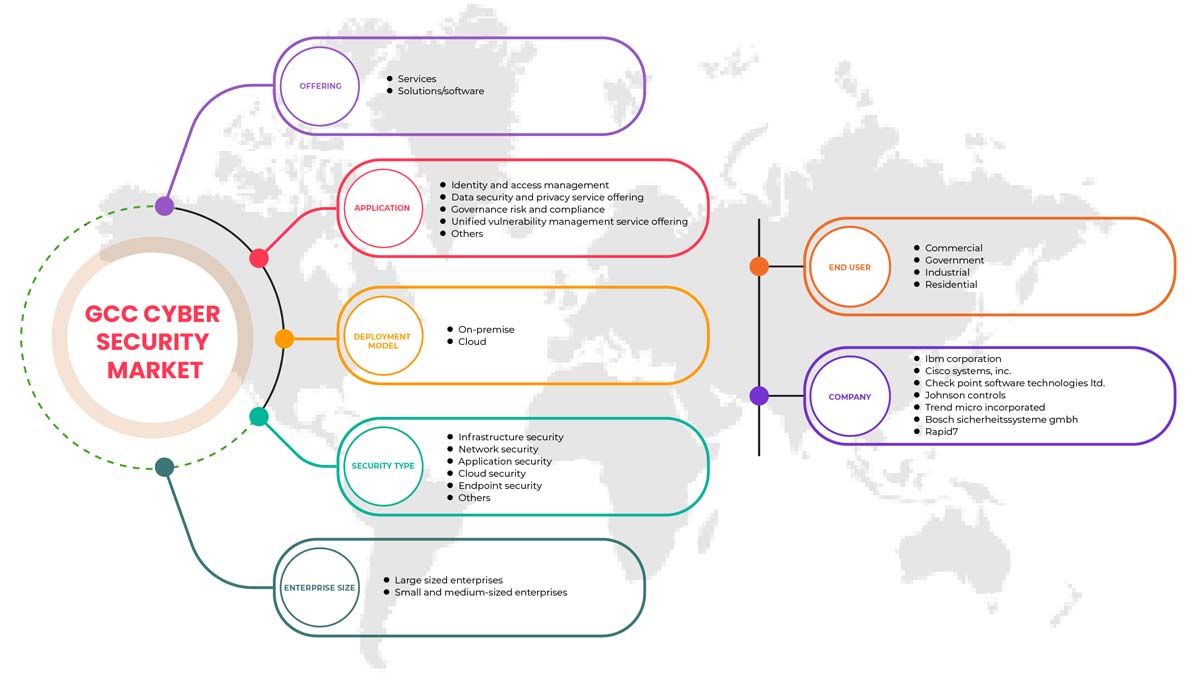
On the basis of end user, the GCC physical security market is segmented into commercial, government, industrial, and residential.
GCC Physical Security Market Regional Analysis/Insights
GCC physical security market is analyzed, and market size insights and trends are provided by the country, component, authentication, deployment type, enterprise size, and end user, as referenced above.
The physical security market report covers Saudi Arabia, U.A.E., Qatar, Oman, Kuwait, and Bahrain. Saudi Arabia dominates the GCC physical security market owing to rising investments in video surveillance and access control systems for government and public sector security.
The country section of the report also provides individual market impacting factors and changes in market regulation that influence the current and future trends of the market. Data points like downstream and upstream value chain analysis, technical trends, porter's five forces analysis, and case studies are some of the pointers used to forecast the market scenario for individual countries. Also, the presence and availability of GCC brands and their challenges faced due to large or scarce competition from local and domestic brands, the impact of domestic tariffs, and trade routes are considered while providing a forecast analysis of the country data.
Competitive Landscape and GCC Physical Security Market Share Analysis
GCC physical security market competitive landscape provides details by a competitor. Components included are company overview, company financials, revenue generated, market potential, investment in research and development, new market initiatives, GCC presence, production sites and facilities, production capacities, company strengths and weaknesses, product launch, product width, and breadth, application dominance. The above data points are only related to the companies focus on the physical security market.
Some of the major players operating in the GCC physical security market are Thales, HID Global Corporation, Bosch Sicherheitssysteme GmbH, Hangzhou Hikvision Digital Technology Co., Ltd., Pelco (A Motorolla Solutions Company), Cisco Systems, Inc., Axis Communications AB, Johnson Controls, Aware, Inc., IDEMIA among others.
SKU-
Get online access to the report on the World's First Market Intelligence Cloud
- Interactive Data Analysis Dashboard
- Company Analysis Dashboard for high growth potential opportunities
- Research Analyst Access for customization & queries
- Competitor Analysis with Interactive dashboard
- Latest News, Updates & Trend analysis
- Harness the Power of Benchmark Analysis for Comprehensive Competitor Tracking
Table of Content
1 INTRODUCTION
1.1 OBJECTIVES OF THE STUDY
1.2 MARKET DEFINITION
1.3 OVERVIEW OF GCC PHYSICAL AND CYBER SECURITY MARKET
1.4 CURRENCY AND PRICING
1.5 LIMITATIONS
1.6 MARKETS COVERED
2 MARKET SEGMENTATION
2.1 MARKETS COVERED
2.2 GEOGRAPHICAL SCOPE
2.3 YEARS CONSIDERED FOR THE STUDY
2.4 DBMR TRIPOD DATA VALIDATION MODEL
2.5 PRIMARY INTERVIEWS WITH KEY OPINION LEADERS
2.6 DBMR MARKET POSITION GRID
2.7 VENDOR SHARE ANALYSIS
2.8 MARKET END USER COVERAGE GRID
2.9 MULTIVARIATE MODELING
2.1 COMPONENT TIMELINE CURVE
2.11 OFFERING TIMELINE CURVE
2.12 SECONDARY SOURCES
2.13 ASSUMPTIONS
3 EXECUTIVE SUMMARY
4 PREMIUM INSIGHTS
4.1 INVESTMENT POLICY
4.1 CASE STUDY
4.1.1 SECURE SOFTWARE DEVELOPMENT INFRASTRUCTURE
4.1.2 SOC-AS-A-PLATFORM (SOCAAP)
4.1.3 RANSOMWARE & FORENSICS ANALYSIS
4.1.4 WISCONSIN'S DEER DISTRICT SECURITY PLAN
4.1.5 LICENSE PLATE READERS IN SCHOOLS
4.1.6 K-12 SCHOOLS
4.2 VALUE CHAIN ANALYSIS
4.3 PORTERS FIVE FORCES
4.4 PESTLE ANALYSIS
4.5 TECHNOLOGICAL LANDSCAPE
4.5.1 AI AND MACHINE LEARNING
4.5.2 IOT
4.5.3 BLOCKCHAIN
4.6 REGULATORY STANDARDS
4.6.1 CYBER SECURITY
4.6.2 PHYSICAL SECURITY
4.7 LOCAL PLAYERS LIST
5 MARKET OVERVIEW
5.1 DRIVERS
5.1.1 ADVENT OF REMOTE WORKING CULTURE
5.1.2 INCREASE IN CLOUD SERVICES CYBER AND PHYSICAL SECURITY SOLUTIONS
5.1.3 GROWING IMPORTANCE OF PHYSICAL BIOMETRIC SOLUTIONS ACROSS ALL SECTORS
5.1.4 EMERGENCE OF SMART INTERCONNECTED BUILDING/HOME
5.2 RESTRAINTS
5.2.1 RISE IN CYBER SECURITY THREAT AND RANSOMWARE IN PHYSICAL AND CYBER SECURITY SOLUTIONS
5.3 OPPORTUNITIES
5.3.1 RISING STRATEGIC PARTNERSHIP AND ACQUISITION AMONG ORGANIZATIONS FOR PHYSICAL AND CYBER SECURITY SYSTEM
5.3.2 EMERGENCE OF VARIOUS DISRUPTIVE TECHNOLOGY SUCH AS IOT AND AI FOR VARIOUS INDUSTRIES
5.3.3 INCREASE IN CASES OF DATA AND SECURITY BREACHES IN VARIOUS ORGANIZATIONS
5.4 CHALLENGES
5.4.1 LACK OF PROFESSIONAL EXPERTISE FOR CYBER SECURITY SYSTEMS
5.4.2 COMPLEXITY ASSOCIATED WITH THE INTEGRATION OF VARIOUS PHYSICAL SECURITY SYSTEMS
6 GCC CYBER SECURITY MARKET, BY OFFERING
6.1 OVERVIEW
6.2 SERVICES
6.3 SOLUTIONS/SOFTWARE
7 GCC PHYSICAL SECURITY MARKET, BY COMPONENT
7.1 OVERVIEW
7.2 HARDWARE
7.2.1 VIDEO SURVEILLANCE SYSTEM
7.2.1.1 CAMERAS
7.2.1.2 RECORDERS
7.2.2 PHYSICAL ACCESS CONTROL SYSTEM
7.2.2.1 BIOMETRICS
7.2.2.2 LOCKS
7.2.2.2.1 ELECTRONIC LOCKS
7.3 SERVICES
7.3.1 MANAGED SERVICES
7.3.2 PROFESSIONAL SERVICES
7.4 SOFTWARE
8 GCC PHYSICAL SECURITY MARKET, BY AUTHENTICATION
8.1 OVERVIEW
8.2 SINGLE- FACTOR AUTHENTICATION
8.3 TWO- FACTOR AUTHENTICATION
8.4 THREE- FACTOR AUTHENTICATION
9 GCC CYBER SECURITY MARKET, BY APPLICATION
9.1 OVERVIEW
9.2 IDENTITY AND ACCESS MANAGEMENT
9.3 DATA SECURITY AND PRIVACY SERVICE OFFERING
9.4 GOVERNANCE RISK AND COMPLIANCE
9.5 UNIFIED VULNERABILITY MANAGEMENT SERVICE OFFERING
9.6 OTHERS
10 GCC CYBER SECURITY MARKET, BY SECURITY TYPE
10.1 OVERVIEW
10.2 INFRASTRUCTURE SECURITY
10.3 NETWORK SECURITY
10.4 APPLICATION SECURITY
10.5 CLOUD SECURITY
10.6 ENDPOINT SECURITY
10.7 OTHERS
11 GCC PHYSICAL AND CYBER SECURITY MARKET, BY DEPLOYMENT MODEL
11.1 OVERVIEW
11.2 ON-PREMISE
11.3 CLOUD
12 GCC PHYSICAL AND CYBER SECURITY MARKET, BY ENTERPRISE SIZE
12.1 OVERVIEW
12.2 LARGE SIZED ENTERPRISES
12.3 SMALL AND MEDIUM-SIZED ENTERPRISES
13 GCC PHYSICAL AND CYBER SECURITY MARKET, BY END USER
13.1 OVERVIEW
13.2 COMMERCIAL
13.3 GOVERNMENT
13.4 INDUSTRIAL
13.5 RESIDENTIAL
14 GCC CYBER SECURITY MARKET, COMPANY LANDSCAPE
14.1 COMPANY SHARE ANALYSIS: GCC
15 GCC PHYSICAL SECURITY MARKET, COMPANY LANDSCAPE
15.1 COMPANY SHARE ANALYSIS: GCC
16 SWOT ANALYSIS
16.1 DBMR ANALYSIS
16.1.1 STRENGTH
16.1.2 WEAKNESS
16.1.3 THREATS
16.1.4 OPPORTUNITY
17 COMPANY PROFILE
17.1 THALES GROUP
17.1.1 COMPANY SNAPSHOT
17.1.2 REVENUE ANALYSIS
17.1.3 PRODUCTS PORTFOLIO
17.1.4 RECENT DEVELOPMENTS
17.2 HANGZHOU HIKVISION DIGITAL TECHNOLOGY CO., LTD
17.2.1 COMPANY SNAPSHOT
17.2.2 REVENUE ANALYSIS
17.2.3 PRODUCT PORTFOLIO
17.2.4 RECENT DEVELOPMENTS
17.3 ACCENTURE
17.3.1 COMPANY SNAPSHOT
17.3.2 REVENUE ANALYSIS
17.3.3 SERVICE PORTFOLIO
17.3.4 RECENT DEVELOPMENTS
17.4 IDEMIA
17.4.1 COMPANY SNAPSHOT
17.4.2 PRODUCT PORTFOLIO
17.4.3 RECENT DEVELOPMENTS
17.5 BAE SYSTEMS
17.5.1 COMPANY SNAPSHOT
17.5.2 REVENUE ANALYSIS
17.5.3 SERVICE PORTFOLIO
17.5.4 RECENT DEVELOPMENT
17.6 FORTINET, INC.
17.6.1 COMPANY SNAPSHOT
17.6.2 REVENUE ANALYSIS
17.6.3 SERVICE PORTFOLIO
17.6.4 RECENT DEVELOPMENTS
17.7 PALO ALTO NETWORKS
17.7.1 COMPANY SNAPSHOT
17.7.2 REVENUE ANALYSIS
17.7.3 PRODUCT PORTFOLIO
17.7.4 RECENT DEVELOPMENT
17.8 AWARE, INC.
17.8.1 COMPANY SNAPSHOT
17.8.2 REVENUE ANALYSIS
17.8.3 PRODUCT PORTFOLIO
17.8.4 RECENT DEVELOPMENTS
17.9 AXIS COMMUNICATIONS AB
17.9.1 COMPANY SNAPSHOT
17.9.2 REVENUE ANALYSIS
17.9.3 PRODUCT PORTFOLIO
17.9.4 RECENT DEVELOPMENT
17.1 BOSCH SICHERHEITSSYSTEME GMBH
17.10.1 COMPANY SNAPSHOT
17.10.2 REVENUE ANALYSIS
17.10.3 PRODUCTS PORTFOLIO
17.10.4 RECENT DEVELOPMENT
17.11 CHECK POINT SOFTWARE TECHNOLOGIES LTD.
17.11.1 COMPANY SNAPSHOT
17.11.2 REVENUE ANALYSIS
17.11.3 PRODUCTS PORTFOLIO
17.11.4 RECENT DEVELOPMENTS
17.12 CISCO SYSTEMS, INC.
17.12.1 COMPANY SNAPSHOT
17.12.2 REVENUE ANALYSIS
17.12.3 PRODUCTS PORTFOLIO
17.12.4 RECENT DEVELOPMENTS
17.13 HEXAGON AB
17.13.1 COMPANY SNAPSHOT
17.13.2 REVENUE ANALYSIS
17.13.3 OFFERING PORTFOLIO
17.13.4 RECENT DEVELOPMENT
17.14 HID GLOBAL CORPORATION
17.14.1 COMPANY SNAPSHOT
17.14.2 PRODUCT PORTFOLIO
17.14.3 RECENT DEVELOPMENT
17.15 IBM CORPORATION
17.15.1 COMPANY SNAPSHOT
17.15.2 REVENUE ANALYSIS
17.15.3 PRODUCTS PORTFOLIO
17.15.4 RECENT DEVELOPMENTS
17.16 JOHNSON CONTROL
17.16.1 COMPANY SNAPSHOT
17.16.2 REVENUE ANALYSIS
17.16.3 PRODUCTS PORTFOLIO
17.16.4 RECENT DEVELOPMENTS
17.17 JUNIPER NETWORKS, INC.
17.17.1 COMPANY SNAPSHOT
17.17.2 REVENUE ANALYSIS
17.17.3 PRODUCTS PORTFOLIO
17.17.4 RECENT DEVELOPMENTS
17.18 MCAFEE, LLC
17.18.1 COMPANY SNAPSHOT
17.18.2 REVENUE ANALYSIS
17.18.3 PRODUCTS PORTFOLIO
17.18.4 RECENT DEVELOPMENTS
17.19 MICRO FOCUS
17.19.1 COMPANY SNAPSHOT
17.19.2 REVENUE ANALYSIS
17.19.3 PRODUCT PORTFOLIO
17.19.4 RECENT DEVELOPMENT
17.2 MICROSOFT
17.20.1 COMPANY SNAPSHOT
17.20.2 REVENUE ANALYSIS
17.20.3 PRODUCT PORTFOLIO
17.20.4 RECENT DEVELOPMENTS
17.21 ORACLE
17.21.1 COMPANY SNAPSHOT
17.21.2 REVENUE ANALYSIS
17.21.3 SERVICE CATEGORY
17.21.4 RECENT DEVELOPMENT
17.22 PELCO CORPORATIONS
17.22.1 COMPANY SNAPSHOT
17.22.2 REVENUE ANALYSIS
17.22.3 PRODUCTS PORTFOLIO
17.22.4 RECENT DEVELOPMENTS
17.23 RAPID7
17.23.1 COMPANY SNAPSHOT
17.23.2 REVENUE ANALYSIS
17.23.3 PRODUCT PORTFOLIO
17.23.4 RECENT DEVELOPMENTS
17.24 SPLUNK INC.
17.24.1 COMPANY SNAPSHOT
17.24.2 REVENUE ANALYSIS
17.24.3 PRODUCTS PORTFOLIO
17.24.4 RECENT DEVELOPMENT
17.25 TREND MICRO INCORPORATED
17.25.1 COMPANY SNAPSHOT
17.25.2 REVENUE ANALYSIS
17.25.3 PRODUCTS PORTFOLIO
17.25.4 RECENT DEVELOPMENTS
18 QUESTIONNAIRE
19 RELATED REPORTS
List of Table
TABLE 1 LIST OF LOCAL CYBER SECURITY PLAYERS
TABLE 2 LIST OF LOCAL PHYSICAL SECURITY PLAYERS
TABLE 3 GCC CYBER SECURITY MARKET, BY OFFERING, 2020-2029 (USD MILLION)
TABLE 4 GCC SERVICES IN CYBER SECURITY MARKET, BY TYPE, 2020-2029 (USD MILLION)
TABLE 5 GCC SOLUTIONS/SOFTWARE IN CYBER SECURITY MARKET, BY TYPE, 2020-2029 (USD MILLION)
TABLE 6 GCC PHYSICAL SECURITY MARKET, BY COMPONENT, 2020-2029 (USD MILLION)
TABLE 7 GCC HARWARE IN PHYSICAL SECURITY MARKET, BY TYPE, 2020-2029 (USD MILLION)
TABLE 8 GCC VIDEO SURVEILLANCE SYSTEM IN HARDWRAE PHYSICAL SECURITY MARKET, BY TYPE, 2020-2029 (USD MILLION)
TABLE 9 GCC CAMERAS IN VIDEO SURVEILLANCE SYSTEM PHYSICAL SECURITY MARKET, BY TYPE, 2020-2029 (USD MILLION)
TABLE 10 GCC RECORDERS IN VIDEO SURVEILLANCE SYSTEM PHYSICAL SECURITY MARKET, BY TYPE, 2020-2029 (USD MILLION)
TABLE 11 GCC PHYSICAL ACCESS CONTROL SYSTEM IN PHYSICAL SECURITY MARKET, BY TYPE, 2020-2029 (USD MILLION)
TABLE 12 GCC BIOMETRICS IN PHYSICAL ACCESS CONTROL SYSTEM PHYSICAL SECURITY MARKET, BY TYPE, 2020-2029 (USD MILLION)
TABLE 13 GCC LOCKS IN PHYSICAL ACCESS CONTROL SYSTEM PHYSICAL SECURITY MARKET, BY TYPE, 2020-2029 (USD MILLION)
TABLE 14 GCC ELECTRONIC LOCKS IN LOCKS PHYSICAL SECURITY MARKET, BY TYPE, 2020-2029 (USD MILLION)
TABLE 15 GCC SERVICES IN PHYSICAL SECURITY MARKET, BY TYPE, 2020-2029 (USD MILLION)
TABLE 16 GCC MANAGED SERVICES IN SERVICES PHYSICAL SECURITY MARKET, BY TYPE, 2020-2029 (USD MILLION)
TABLE 17 GCC PROFESSIONAL SERVICES IN SERVICES PHYSICAL SECURITY MARKET, BY TYPE, 2020-2029 (USD MILLION)
TABLE 18 GCC SOFTWARE IN PHYSICAL SECURITY MARKET, BY TYPE, 2020-2029 (USD MILLION)
TABLE 19 GCC PHYSICAL SECURITY MARKET, BY AUTHENTICATION, 2020-2029 (USD MILLION)
TABLE 20 GCC CYBER SECURITY MARKET, BY APPLICATION, 2020-2029 (USD MILLION)
TABLE 21 GCC CYBER SECURITY MARKET, BY SECURITY TYPE, 2020-2029 (USD MILLION)
TABLE 22 GCC PHYSICAL SECURITY MARKET, BY DEPLOYMENT MODEL, 2020-2029 (USD MILLION)
TABLE 23 GCC CYBER SECURITY MARKET, BY DEPLOYMENT MODEL, 2020-2029 (USD MILLION)
TABLE 24 GCC PHYSICAL SECURITY MARKET, BY ENTERPRISE SIZE, 2020-2029 (USD MILLION)
TABLE 25 GCC CYBER SECURITY MARKET, BY ENTERPRISE SIZE, 2020-2029 (USD MILLION)
TABLE 26 GCC LARGE SIZED ENTERPRISES IN PHYSICAL SECURITY MARKET, BY DEPLOYMENT MODEL, 2020-2029 (USD MILLION)
TABLE 27 GCC LARGE SIZED ENTERPRISES IN CYBER SECURITY MARKET, BY DEPLOYMENT MODEL, 2020-2029 (USD MILLION)
TABLE 28 GCC SMALL AND MEDIUM-SIZED ENTERPRISES IN PHYSICAL SECURITY MARKET, BY DEPLOYMENT MODEL, 2020-2029 (USD MILLION)
TABLE 29 GCC SMALL AND MEDIUM-SIZED ENTERPRISES IN CYBER SECURITY MARKET, BY DEPLOYMENT MODEL, 2020-2029 (USD MILLION)
TABLE 30 GCC PHYSICAL SECURITY MARKET, BY END USER, 2020-2029 (USD MILLION)
TABLE 31 GCC CYBER SECURITY MARKET, BY END USER, 2020-2029 (USD MILLION)
TABLE 32 GCC COMMERCIAL IN PHYSICAL SECURITY MARKET, BY TYPE, 2020-2029 (USD MILLION)
TABLE 33 GCC COMMERCIAL IN CYBER SECURITY MARKET, BY TYPE, 2020-2029 (USD MILLION)
TABLE 34 GCC INDUSTRIAL IN PHYSICAL SECURITY MARKET, BY TYPE 2020-2029 (USD MILLION)
TABLE 35 GCC INDUSTRIAL IN CYBER SECURITY MARKET, BY TYPE 2020-2029 (USD MILLION)
TABLE 36 GCC RESIDENTIAL IN PHYSICAL SECURITY MARKET, BY TYPE 2020-2029 (USD MILLION)
TABLE 37 GCC RESIDENTIAL IN CYBER SECURITY MARKET, BY TYPE 2020-2029 (USD MILLION)
List of Figure
FIGURE 1 GCC PHYSICAL AND CYBER SECURITY MARKET: SEGMENTATION
FIGURE 2 GCC PHYSICAL AND CYBER SECURITY MARKET: DATA TRIANGULATION
FIGURE 3 GCC PHYSICAL AND CYBER SECURITY MARKET: DROC ANALYSIS
FIGURE 4 GCC PHYSICAL SECURITY MARKET: GLOBAL VS REGIONAL ANALYSIS
FIGURE 5 GCC CYBER SECURITY MARKET: GLOBAL VS REGIONAL ANALYSIS
FIGURE 6 GCC PHYSICAL AND CYBER SECURITY MARKET: COMPANY RESEARCH ANALYSIS
FIGURE 7 GCC PHYSICAL AND CYBER SECURITY MARKET: INTERVIEW DEMOGRAPHICS
FIGURE 8 GCC PHYSICAL SECURITY MARKET: DBMR MARKET POSITION GRID
FIGURE 9 GCC CYBER SECURITY MARKET: DBMR MARKET POSITION GRID
FIGURE 10 GCC CYBER SECURITY MARKET: VENDOR SHARE ANALYSIS
FIGURE 11 GCC PHYSICAL SECURITY MARKET: VENDOR SHARE ANALYSIS
FIGURE 12 GCC PHYSICAL SECURITY MARKET: MARKET END USER COVERAGE GRID
FIGURE 13 GCC CYBER SECURITY MARKET: MARKET END USER COVERAGE GRID
FIGURE 14 GCC CYBER SECURITY MARKET: SEGMENTATION
FIGURE 15 GCC PHYSICAL SECURITY MARKET: SEGMENTATION
FIGURE 16 EMERGENCE OF SMART INTERCONNECTED BUILDING/HOME IS EXPECTED TO DRIVE GCC PHYSICAL SECURITY MARKET IN THE FORECAST PERIOD OF 2022 TO 2029
FIGURE 17 EMERGENCE OF SMART INTERCONNECTED BUILDING/HOME IS EXPECTED TO DRIVE GCC CYBER SECURITY MARKET IN THE FORECAST PERIOD OF 2022 TO 2029
FIGURE 18 SERVICES SEGMENT IS EXPECTED TO ACCOUNT FOR THE LARGEST SHARE OF GCC CYBER SECURITY MARKET IN THE FORECASTED PERIOD OF 2022 & 2029
FIGURE 19 HARDWARE SEGMENT IS EXPECTED TO ACCOUNT FOR THE LARGEST SHARE OF GCC PHYSICAL SECURITY MARKET IN THE FORECASTED PERIOD OF 2022 & 2029
FIGURE 20 VALUE CHAIN FOR PHYSICAL AND CYBER SECURITY MARKET
FIGURE 21 PORTERS FIVE FORCES ANALYSIS FOR PHYSICAL AND CYBER SECURITY MARKET
FIGURE 22 PESTLE ANALYSIS FOR PHYSICAL AND CYBER SECURITY MARKET
FIGURE 23 DRIVERS, RESTRAINTS, OPPORTUNITIES, AND CHALLENGES OF GCC PHYSICAL AND CYBER SECURITY MARKET
FIGURE 24 KEY STATS OF REMOTE WORK
FIGURE 25 GROWING PREVALENCE OF BIOMETRIC SOLUTIONS AMONG CONSUMER
FIGURE 26 TECHNOLOGY AMALGAMATION IN SMART HOME/ BUILDINGS
FIGURE 27 IMPACT OF CYBER SECURITY THREAT
FIGURE 28 PHISHING ATTACKS REPORTED IN RESPECTIVE COUNTRIES IN Q2, 2021
FIGURE 29 GCC CYBER SECURITY MARKET, BY OFFERING, 2021
FIGURE 30 GCC PHYSICAL SECURITY MARKET, BY COMPONENT, 2021
FIGURE 31 GCC PHYSICAL SECURITY MARKET, BY AUTHENTICATION, 2021
FIGURE 32 GCC CYBER SECURITY MARKET: BY APPLICATION, 2021
FIGURE 33 GCC CYBER SECURITY MARKET: BY SECURITY TYPE, 2021
FIGURE 34 GCC PHYSICAL SECURITY MARKET, BY DEPLOYMENT MODEL, 2021
FIGURE 35 GCC CYBER SECURITY MARKET, BY DEPLOYMENT MODEL, 2021
FIGURE 36 GCC PHYSICAL SECURITY MARKET, BY ENTERPRISE SIZE, 2021
FIGURE 37 GCC CYBER SECURITY MARKET, BY ENTERPRISE SIZE, 2021
FIGURE 38 GCC PHYSICAL SECURITY MARKET: BY END USER, 2021
FIGURE 39 GCC CYBER SECURITY MARKET: BY END USER, 2021
FIGURE 40 GCC CYBER SECURITY MARKET: COMPANY SHARE 2021 (%)
FIGURE 41 GCC PHYSICAL SECURITY MARKET: COMPANY SHARE 2021 (%)
Research Methodology
Data collection and base year analysis are done using data collection modules with large sample sizes. The stage includes obtaining market information or related data through various sources and strategies. It includes examining and planning all the data acquired from the past in advance. It likewise envelops the examination of information inconsistencies seen across different information sources. The market data is analysed and estimated using market statistical and coherent models. Also, market share analysis and key trend analysis are the major success factors in the market report. To know more, please request an analyst call or drop down your inquiry.
The key research methodology used by DBMR research team is data triangulation which involves data mining, analysis of the impact of data variables on the market and primary (industry expert) validation. Data models include Vendor Positioning Grid, Market Time Line Analysis, Market Overview and Guide, Company Positioning Grid, Patent Analysis, Pricing Analysis, Company Market Share Analysis, Standards of Measurement, Global versus Regional and Vendor Share Analysis. To know more about the research methodology, drop in an inquiry to speak to our industry experts.
Customization Available
Data Bridge Market Research is a leader in advanced formative research. We take pride in servicing our existing and new customers with data and analysis that match and suits their goal. The report can be customized to include price trend analysis of target brands understanding the market for additional countries (ask for the list of countries), clinical trial results data, literature review, refurbished market and product base analysis. Market analysis of target competitors can be analyzed from technology-based analysis to market portfolio strategies. We can add as many competitors that you require data about in the format and data style you are looking for. Our team of analysts can also provide you data in crude raw excel files pivot tables (Fact book) or can assist you in creating presentations from the data sets available in the report.