Global Zero Trust Security Market, By Authentication Type (Single-Factor Authentication, Multi-Factor Authentication), Solution Type (Data Security, Endpoint Security, API Security, Security Analytics, Security Policy Management), Deployment (On-Premises, Cloud), Organization Size (SME, Large Enterprise), Vertical (Banking, Financial Services and Insurance, IT and Telecom, Government and Defense, Energy and Utilities, Healthcare, Retail and E-commerce, Others), Country (U.S., Canada, Mexico, Brazil, Argentina, Rest of South America, Germany, France, Italy, U.K., Belgium, Spain, Russia, Turkey, Netherlands, Switzerland, Rest of Europe, Japan, China, India, South Korea, Australia, Singapore, Malaysia, Thailand, Indonesia, Philippines, Rest of Asia-Pacific, U.A.E, Saudi Arabia, Egypt, South Africa, Israel, Rest of Middle East and Africa) - Industry Trends and Forecast to 2029.
Market Analysis and Insights of Zero Trust Security Market
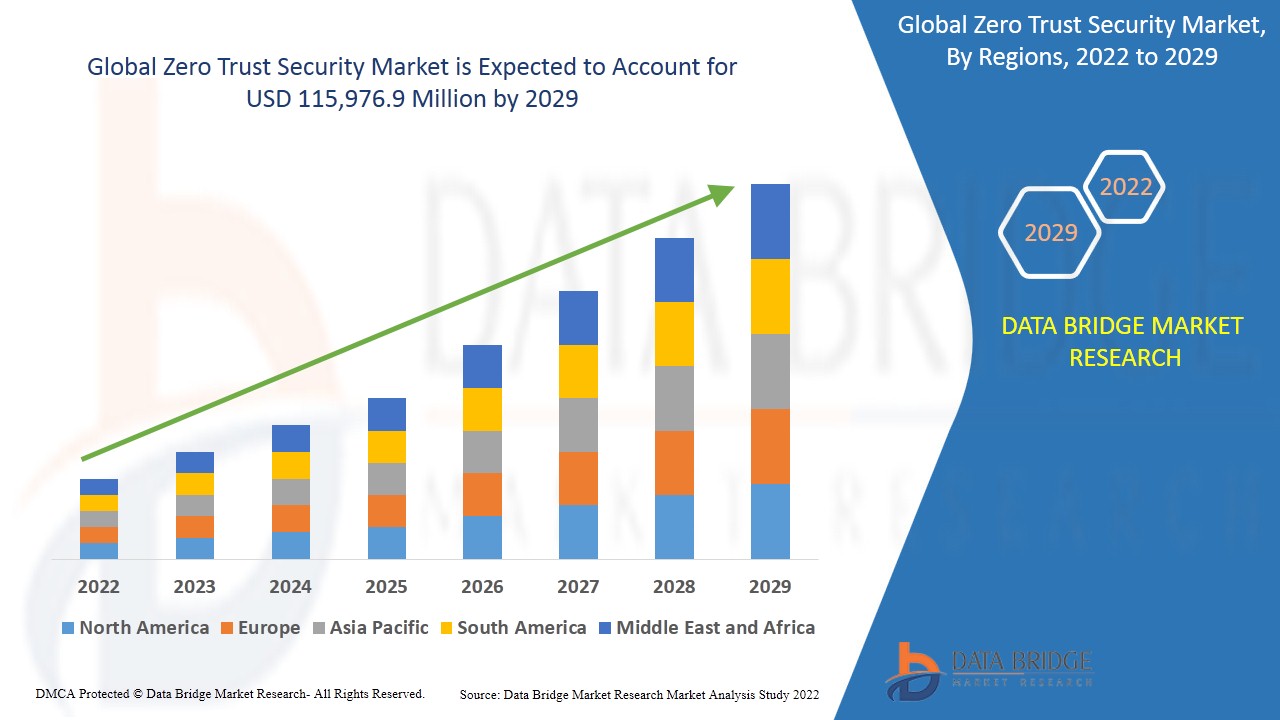
Zero trust security market is expected to gain market growth in the forecast period of 2022 to 2029. Data Bridge Market Research analyses the market to rise up to USD 115,976.9 million by 2029 and is growing at a CAGR of 15.20% in the above-mentioned forecast period.
Zero trust refers to a security model that is based on the principle of strict access controls and not trusting anyone by default, even those who are already inside the network's perimeter. The model is set up in such a way that every person and device attempting to access resources on a private network must pass strict identity verification, regardless of whether they are inside or outside the network perimeter. It is a comprehensive approach to network security that incorporates a variety of technologies.
The factors such as increased adoption of zero-trust security solutions, rising digitalization and rising number of cyber vulnerabilities due to the adoption of cloud-based services are expected to emerge as the significant factors accelerating the growth of zero trust security market. In addition to this, the factors such as the increasing awareness and investment in zero trust security solutions, increasing government regulations such as the upcoming CCPA regulations, increasing penetration of the IoT technologies and the companies choosing third-party vendors, increasing number of cyber risks, rising frequency of target-based cyberattacks and increasing regulations for data protection and information security will further aggravate the growth of the zero trust security market in the above-mentioned forecast period. However, the increasing budgetary constraints among small and emerging start-ups in developing economies results as a growth restraint for the market.
The increased demand for better visibility due to the rising IoT traffic among enterprises, rising need for cloud-based zero trust security solutions among SMEs and rising technological advancements and modernization in the techniques used are also anticipated to generate lucrative opportunities for the zero trust security market in the forecast period of 2022 to 2029. The rising design and implementation constraints to deploy zero trust security solutions will pose as a challenge for the zero trust security market.
This zero trust security market report provides details of new recent developments, trade regulations, import export analysis, production analysis, value chain optimization, market share, impact of domestic and localized market players, analyses opportunities in terms of emerging revenue pockets, changes in market regulations, strategic market growth analysis, market size, category market growths, application niches and dominance, product approvals, product launches, geographical expansions, technological innovations in the market. To gain more info on zero trust security market contact Data Bridge Market Research for an Analyst Brief, our team will help you take an informed market decision to achieve market growth.
Global Zero Trust Security Market Scope and Market Size
The zero trust security market is segmented on the basis of authentication type, solution type, deployment, organization size and vertical. The growth amongst the different segments helps you in attaining the knowledge related to the different growth factors expected to be prevalent throughout the market and formulate different strategies to help identify core application areas and the difference in your target market.
- On the basis of authentication type, the zero trust security market is segmented into single-factor authentication and multi-factor authentication.
- On the basis of solution type, the zero trust security market is segmented into data security, endpoint security, API security, security analytics and security policy management.
- On the basis of deployment, the zero trust security market is segmented into on-premises and cloud.
- On the basis of organization size, the zero trust security market is segmented into SME and large enterprise.
The zero trust security market is also segmented on the basis of vertical into banking, financial services and insurance, IT and telecom, government and defense, energy and utilities, healthcare, retail and E-commerce and others.
Zero Trust Security Market Country Level Analysis
The zero trust security market is segmented on the basis of authentication type, solution type, deployment, organization size and vertical.
The countries covered in the zero trust security market report are U.S., Canada, Mexico, Brazil, Argentina, Rest of South America, Germany, France, Italy, U.K., Belgium, Spain, Russia, Turkey, Netherlands, Switzerland, Rest of Europe, Japan, China, India, South Korea, Australia, Singapore, Malaysia, Thailand, Indonesia, Philippines, Rest of Asia-Pacific, U.A.E, Saudi Arabia, Egypt, South Africa, Israel, Rest of Middle East and Africa.
North America dominates the zero trust security market during the forecast period owing to the high adoption of digital transformation with large volumes of critical data being generated, rising need for zero-trust security solutions, rising digitalization, increasing awareness and investment in zero trust security solutions and increasing government regulations such as the upcoming CCPA regulations in this region in the forecast period of 2022 to 2029. On the other hand, Asia-Pacific is expected to show a lucrative growth due to the high number of cyber risks due to the adoption of cloud-based services in this region.
The country section of the zero trust security market report also provides individual market impacting factors and changes in regulation in the market domestically that impacts the current and future trends of the market. Data points such as consumption volumes, production sites and volumes, import export analysis, price trend analysis, cost of raw materials, down-stream and upstream value chain analysis are some of the major pointers used to forecast the market scenario for individual countries. Also, presence and availability of global brands and their challenges faced due to large or scarce competition from local and domestic brands, impact of domestic tariffs and trade routes are considered while providing forecast analysis of the country data.
Competitive Landscape and Zero Trust Security Market Share Analysis
The zero trust security market competitive landscape provides details by competitor. Details included are company overview, company financials, revenue generated, market potential, investment in research and development, new market initiatives, global presence, production sites and facilities, production capacities, company strengths and weaknesses, product launch, product width and breadth, application dominance. The above data points provided are only related to the companies' focus related to zero trust security market.
Some of the major players operating in the zero trust security market report are Cisco, IBM, Akamai Technologies, Check Point Software Technologies Ltd, Pulse Secure, LLC, Palo Alto Networks, Cyxtera Technologies, Inc., Broadcom, Okta, Cloudflare, Inc, Forcepoint, Centrify Corporation., FireEye, Cyxtera Technologies, Inc., Illumio, Sophos Ltd and Microsoft among others.
Recent Developments
- In September 2020, Check Point acquired Odo Security's cloud-based technology for providing secure remote access. Check Point combined this technology with its Infinity architecture to provide the simplest and safest solution for businesses seeking secure remote access to any application.
SKU-
Obtenha acesso online ao relatório sobre a primeira nuvem de inteligência de mercado do mundo
- Painel interativo de análise de dados
- Painel de análise da empresa para oportunidades de elevado potencial de crescimento
- Acesso de analista de pesquisa para personalização e customização. consultas
- Análise da concorrência com painel interativo
- Últimas notícias, atualizações e atualizações Análise de tendências
- Aproveite o poder da análise de benchmark para um rastreio abrangente da concorrência
Metodologia de Investigação
A recolha de dados e a análise do ano base são feitas através de módulos de recolha de dados com amostras grandes. A etapa inclui a obtenção de informações de mercado ou dados relacionados através de diversas fontes e estratégias. Inclui examinar e planear antecipadamente todos os dados adquiridos no passado. Da mesma forma, envolve o exame de inconsistências de informação observadas em diferentes fontes de informação. Os dados de mercado são analisados e estimados utilizando modelos estatísticos e coerentes de mercado. Além disso, a análise da quota de mercado e a análise das principais tendências são os principais fatores de sucesso no relatório de mercado. Para saber mais, solicite uma chamada de analista ou abra a sua consulta.
A principal metodologia de investigação utilizada pela equipa de investigação do DBMR é a triangulação de dados que envolve a mineração de dados, a análise do impacto das variáveis de dados no mercado e a validação primária (especialista do setor). Os modelos de dados incluem grelha de posicionamento de fornecedores, análise da linha de tempo do mercado, visão geral e guia de mercado, grelha de posicionamento da empresa, análise de patentes, análise de preços, análise da quota de mercado da empresa, normas de medição, análise global versus regional e de participação dos fornecedores. Para saber mais sobre a metodologia de investigação, faça uma consulta para falar com os nossos especialistas do setor.
Personalização disponível
A Data Bridge Market Research é líder em investigação formativa avançada. Orgulhamo-nos de servir os nossos clientes novos e existentes com dados e análises que correspondem e atendem aos seus objetivos. O relatório pode ser personalizado para incluir análise de tendências de preços de marcas-alvo, compreensão do mercado para países adicionais (solicite a lista de países), dados de resultados de ensaios clínicos, revisão de literatura, mercado remodelado e análise de base de produtos . A análise de mercado dos concorrentes-alvo pode ser analisada desde análises baseadas em tecnologia até estratégias de carteira de mercado. Podemos adicionar quantos concorrentes necessitar de dados no formato e estilo de dados que procura. A nossa equipa de analistas também pode fornecer dados em tabelas dinâmicas de ficheiros Excel em bruto (livro de factos) ou pode ajudá-lo a criar apresentações a partir dos conjuntos de dados disponíveis no relatório.