Global Industrial Cybersecurity Market
Tamanho do mercado em biliões de dólares
CAGR :
% 
 USD
17.66 Billion
USD
30.57 Billion
2024
2032
USD
17.66 Billion
USD
30.57 Billion
2024
2032
| 2025 –2032 | |
| USD 17.66 Billion | |
| USD 30.57 Billion | |
|
|
|
|
Mercado global de segurança cibernética industrial, por componente (soluções, serviços), tipo de segurança (segurança de endpoint, segurança de rede, segurança de aplicativos, segurança de nuvem, outros), implantação (local, nuvem) e usuário final (fabricação industrial, transporte e logística, energia e serviços públicos, outros) – Tendências do setor e previsão até 2032.
Tamanho do mercado de segurança cibernética industrial
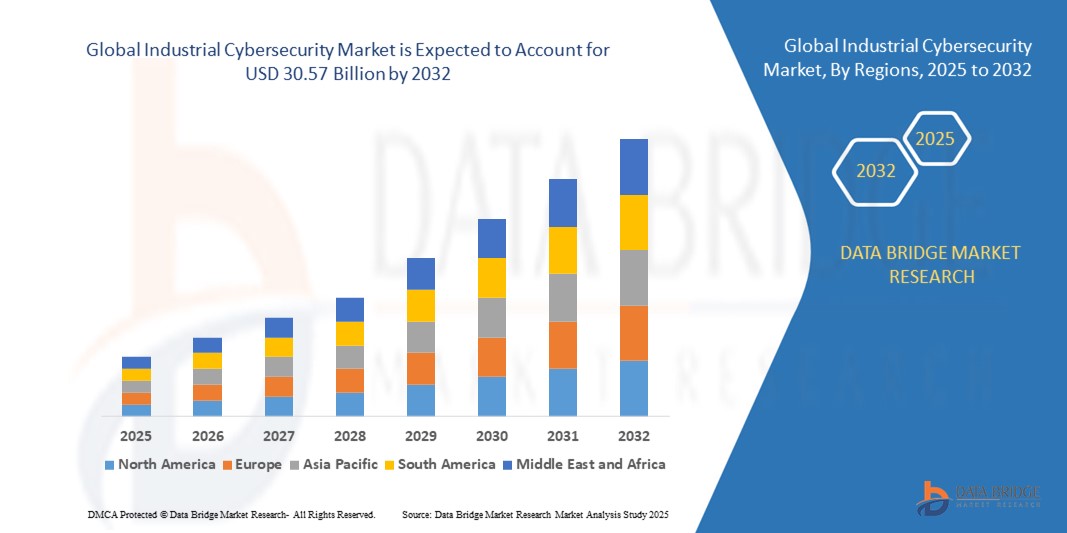
- O tamanho do mercado global de segurança cibernética industrial foi avaliado em US$ 17,66 bilhões em 2024 e deve atingir US$ 30,57 bilhões até 2032 , com um CAGR de 7,10% durante o período previsto.
- O crescimento do mercado é impulsionado principalmente pela frequência crescente de ameaças cibernéticas, pela adoção de tecnologias da Indústria 4.0 e pela crescente necessidade de transformação digital segura nos setores industriais.
- A crescente conscientização sobre os riscos de segurança cibernética e os requisitos de conformidade regulatória entre as organizações industriais está impulsionando ainda mais a demanda por soluções e serviços avançados de segurança cibernética em vários setores
Análise de Mercado de Segurança Cibernética Industrial
- O mercado de segurança cibernética industrial está experimentando um crescimento robusto devido à crescente adoção de dispositivos IoT, automação e sistemas industriais conectados, que aumentam a vulnerabilidade a ataques cibernéticos
- A crescente demanda de setores de infraestrutura crítica, como energia, manufatura e transporte, está incentivando os fornecedores a inovar com soluções avançadas de detecção de ameaças, resposta a incidentes e segurança de confiança zero.
- A América do Norte dominou o mercado de segurança cibernética industrial com a maior participação na receita de 32,9% em 2024, impulsionada por um setor industrial maduro, estruturas regulatórias rigorosas e alta adoção de tecnologias avançadas de segurança cibernética.
- Espera-se que a Ásia-Pacífico seja a região de crescimento mais rápido durante o período previsto, impulsionada pela rápida industrialização, pela crescente adoção de tecnologias de fabricação inteligentes e pela crescente conscientização sobre segurança cibernética em países como China, Índia e Japão.
- O segmento de soluções dominou a maior fatia de mercado de 37,9% em 2024, impulsionado pela necessidade crítica de soluções integradas de segurança cibernética, como firewalls e sistemas de detecção de intrusão para proteger ambientes industriais de ameaças crescentes.
Escopo do Relatório e Segmentação do Mercado de Segurança Cibernética Industrial
|
Atributos |
Principais insights de mercado sobre segurança cibernética industrial |
|
Segmentos abrangidos |
|
|
Países abrangidos |
América do Norte
Europa
Ásia-Pacífico
Oriente Médio e África
Ámérica do Sul
|
|
Principais participantes do mercado |
|
|
Oportunidades de mercado |
|
|
Conjuntos de informações de dados de valor agregado |
Além de insights de mercado, como valor de mercado, taxa de crescimento, segmentos de mercado, cobertura geográfica, participantes do mercado e cenário de mercado, o relatório de mercado selecionado pela equipe de pesquisa de mercado da Data Bridge inclui análise aprofundada de especialistas, análise de importação/exportação, análise de preços, análise de consumo de produção e análise pilão. |
Tendências do mercado de segurança cibernética industrial
Integração crescente de IA e aprendizado de máquina em soluções de segurança cibernética
- O mercado global de segurança cibernética industrial está vivenciando uma tendência significativa de integração de Inteligência Artificial (IA) e Aprendizado de Máquina (ML) em soluções de segurança cibernética
- Essas tecnologias permitem detecção avançada de ameaças, monitoramento em tempo real e análise preditiva, fornecendo insights mais profundos sobre vulnerabilidades potenciais e padrões de ataque em sistemas industriais.
- Plataformas de segurança cibernética com tecnologia de IA podem identificar e mitigar ameaças de forma proativa antes que elas causem interrupções operacionais ou violações de dados, aumentando a resiliência do sistema
- Por exemplo, as empresas estão a desenvolver soluções baseadas em IA que analisam o tráfego da rede e o comportamento do sistema para detetar anomalias, como acesso não autorizado ou malware, e otimizar as respostas de segurança para indústrias como a indústria transformadora e a energia.
- Esta tendência está a aumentar a adopção de sistemas inteligentes de cibersegurança, tornando-os mais apelativos para os operadores industriais que procuram proteger infra-estruturas críticas.
- Os algoritmos de IA e ML podem analisar vastos conjuntos de dados, incluindo registros do sistema, tráfego de rede e comportamento do usuário, para identificar padrões indicativos de ameaças cibernéticas, como ransomware, phishing ou ataques de negação de serviço distribuída (DDoS).
Dinâmica do Mercado de Segurança Cibernética Industrial
Motorista
Crescente demanda por sistemas de controle industrial seguros e proteção de infraestrutura crítica
- A crescente dependência de dispositivos de Internet Industrial das Coisas (IIoT), automação e sistemas interconectados está impulsionando a demanda por soluções robustas de segurança cibernética no setor industrial
- Os sistemas de segurança cibernética aumentam a segurança operacional ao fornecer recursos como detecção de ameaças em tempo real, prevenção de intrusão e acesso remoto seguro a sistemas de controle industrial (ICS)
- As regulamentações governamentais, como o NIST Cybersecurity Framework na América do Norte e a Diretiva NIS da UE, estão exigindo medidas de segurança cibernética mais rigorosas para infraestrutura crítica, impulsionando ainda mais o crescimento do mercado
- A proliferação da tecnologia 5G e da IoT está permitindo uma transmissão de dados mais rápida e menor latência, dando suporte a aplicações avançadas de segurança cibernética, como monitoramento e resposta em tempo real em ambientes industriais.
- Os operadores industriais estão adotando cada vez mais soluções integradas de segurança cibernética como padrão para atender aos requisitos regulatórios e proteger ativos críticos em setores como manufatura, energia e transporte.
Restrição/Desafio
Altos custos de implementação e preocupações com a privacidade de dados
- O investimento inicial significativo necessário para hardware, software e integração de segurança cibernética em sistemas industriais existentes pode ser uma barreira importante, especialmente para pequenas e médias empresas (PMEs) em mercados emergentes.
- A integração de soluções de segurança cibernética em sistemas de controle industrial legados costuma ser complexa e dispendiosa, exigindo conhecimento especializado e atualizações de infraestrutura.
- As preocupações com a privacidade e a segurança dos dados são um desafio crítico, uma vez que os sistemas de segurança cibernética industrial coletam e processam dados operacionais e pessoais sensíveis, aumentando os riscos de violações ou uso indevido.
- O cenário regulatório fragmentado entre os países, com padrões variados para proteção de dados e conformidade com a segurança cibernética, complica as operações de fabricantes e provedores de serviços globais
- Esses fatores podem impedir a adoção, especialmente em regiões com alta sensibilidade a custos ou rigorosa conscientização sobre privacidade de dados, limitando a expansão do mercado.
Escopo do mercado de segurança cibernética industrial
O mercado é segmentado com base no componente, tipo de segurança, implantação e usuário final.
- Por componente
Com base nos componentes, o mercado global de segurança cibernética industrial é segmentado em soluções e serviços. O segmento de soluções dominou a maior fatia de mercado, com 37,9% em 2024, impulsionado pela necessidade crítica de soluções integradas de segurança cibernética, como firewalls e sistemas de detecção de intrusão, para proteger ambientes industriais de ameaças crescentes.
Espera-se que o segmento de serviços testemunhe a maior taxa de crescimento entre 2025 e 2032. Isso é impulsionado pela crescente complexidade e frequência de ataques cibernéticos, o que aumenta a demanda por serviços profissionais e gerenciados, como detecção de ameaças, resposta a incidentes e gerenciamento de conformidade.
- Por tipo de segurança
Com base no tipo de segurança, o mercado global de cibersegurança industrial é segmentado em segurança de endpoints, segurança de rede, segurança de aplicações, segurança em nuvem, entre outros. Espera-se que o segmento de segurança de rede detenha a maior fatia de mercado em 2024. Isso se deve à crescente adoção de sistemas industriais interconectados, o que torna essencial proteger o fluxo de dados e impedir acessos não autorizados.
Espera-se que o segmento de segurança em nuvem testemunhe um crescimento significativo entre 2025 e 2032. Isso é impulsionado pela rápida adoção de serviços em nuvem e pela mudança para modelos de trabalho remoto, o que exige soluções de segurança robustas para proteger aplicativos e dados nativos da nuvem.
- Por implantação
Com base na implantação, o mercado global de segurança cibernética industrial é segmentado em local e na nuvem. Espera-se que o segmento local detenha a maior participação de mercado, principalmente devido à preferência de certos setores em manter o controle direto sobre seus dados confidenciais e estruturas de segurança personalizadas.
Espera-se que o segmento de nuvem testemunhe o crescimento mais rápido entre 2025 e 2032, impulsionado pela necessidade de soluções de segurança flexíveis, escaláveis e econômicas. Plataformas baseadas em nuvem permitem que as organizações se adaptem rapidamente às ameaças em evolução e otimizem o gerenciamento dos sistemas de segurança.
- Por usuário final
Com base no usuário final, o mercado global de segurança cibernética industrial é segmentado em manufatura industrial, transporte e logística, energia e serviços públicos, entre outros. Espera-se que o segmento de manufatura industrial detenha a maior participação de mercado, impulsionado pela crescente digitalização das operações de manufatura, incluindo o uso de fábricas inteligentes e a Internet Industrial das Coisas (IIoT), que expande a superfície de ataque e aumenta a necessidade de segurança abrangente.
Espera-se que o segmento de energia e serviços públicos experimente um crescimento robusto de 2025 a 2032. Isso se deve à natureza crítica dessas infraestruturas, tornando-as alvos principais de ataques cibernéticos e gerando investimentos significativos em segurança cibernética para garantir a continuidade operacional e a segurança pública.
Análise regional do mercado de segurança cibernética industrial
- A América do Norte domina o mercado de segurança cibernética industrial com a maior participação de receita de 32,9% em 2024, impulsionada por um setor industrial maduro, estruturas regulatórias rigorosas e alta adoção de tecnologias avançadas de segurança cibernética.
- Consumidores e indústrias priorizam soluções de segurança cibernética para proteger infraestruturas críticas, garantir a continuidade operacional e mitigar ameaças cibernéticas sofisticadas, especialmente em regiões com alta digitalização.
- O crescimento é apoiado por avanços em soluções de segurança orientadas por IA, plataformas baseadas em nuvem e adoção crescente em segmentos de implantação local e em nuvem em vários setores
Visão do mercado de segurança cibernética industrial dos EUA
O mercado de cibersegurança industrial dos EUA capturou a maior fatia de receita, de 78,5%, em 2024, na América do Norte, impulsionado por investimentos significativos em infraestrutura de cibersegurança e pela crescente conscientização sobre ameaças cibernéticas a setores críticos, como energia e manufatura. A tendência de conformidade regulatória com padrões como as iniciativas NIST e CISA impulsiona ainda mais a expansão do mercado. A integração de soluções avançadas de cibersegurança em sistemas de controle industrial (ICS) e ambientes de tecnologia operacional (OT) sustenta um ecossistema de mercado robusto.
Visão do mercado de segurança cibernética industrial na Europa
Espera-se que o mercado europeu de cibersegurança industrial testemunhe um crescimento significativo, apoiado por regulamentações rigorosas como o GDPR e pelo aumento das ameaças cibernéticas direcionadas aos setores industriais. As empresas buscam soluções que aprimorem a segurança da rede e garantam a conformidade, mantendo a eficiência operacional. O crescimento é proeminente tanto em novas instalações quanto em projetos de modernização, com países como Alemanha e França demonstrando uma adesão significativa devido às suas fortes bases industriais e foco na transformação digital.
Visão do mercado de segurança cibernética industrial do Reino Unido
Espera-se que o mercado britânico de cibersegurança industrial testemunhe um rápido crescimento, impulsionado pela crescente demanda por sistemas industriais seguros e pela maior conscientização sobre riscos cibernéticos em ambientes urbanos e industriais. A adoção de soluções avançadas, como detecção de ameaças por IA e plataformas de segurança baseadas em nuvem, está em ascensão. Regulamentações em evolução, como as da Comissão Europeia, influenciam o equilíbrio entre medidas robustas de cibersegurança e conformidade.
Visão do mercado de segurança cibernética industrial da Alemanha
Espera-se que a Alemanha testemunhe um rápido crescimento no mercado de segurança cibernética industrial, atribuído ao seu avançado setor de manufatura e ao forte foco na proteção de infraestrutura crítica. As indústrias alemãs preferem soluções tecnologicamente avançadas, como segurança de rede e proteção de endpoints, para proteger a tecnologia operacional e reduzir vulnerabilidades. A integração da segurança cibernética em sistemas industriais premium e serviços de pós-venda sustenta o crescimento sustentado do mercado.
Visão do mercado de segurança cibernética industrial da Ásia-Pacífico
Espera-se que a região Ásia-Pacífico testemunhe a maior taxa de crescimento, impulsionada pela rápida industrialização, pela crescente adoção de IoT e dispositivos conectados e pelo aumento das iniciativas governamentais de segurança cibernética em países como China, Índia e Japão. A crescente conscientização sobre ameaças cibernéticas e a necessidade de estruturas de segurança robustas nos setores de manufatura e energia impulsionam a demanda. Investimentos em soluções baseadas em nuvem e detecção de ameaças baseada em IA aceleram ainda mais o crescimento do mercado.
Visão do mercado de segurança cibernética industrial do Japão
Espera-se que o mercado de segurança cibernética industrial do Japão testemunhe um rápido crescimento devido à forte preferência do consumidor e da indústria por soluções avançadas de segurança cibernética de alta qualidade que aprimorem a segurança e a resiliência operacional. A presença de grandes players industriais e a integração da segurança cibernética à tecnologia operacional aceleram a penetração no mercado. O crescente interesse em serviços de segurança cibernética pós-venda também contribui para o crescimento.
Visão do mercado de segurança cibernética industrial da China
A China detém a maior fatia do mercado de segurança cibernética industrial da Ásia-Pacífico, impulsionada pela rápida digitalização, pelo aumento da automação industrial e pela crescente demanda por soluções de infraestrutura seguras. A expansão da base industrial do país e o foco na manufatura inteligente impulsionam a adoção de soluções avançadas de segurança cibernética. A forte inovação nacional e os preços competitivos aumentam a acessibilidade e o crescimento do mercado.
Participação no mercado de segurança cibernética industrial
O setor de segurança cibernética industrial é liderado principalmente por empresas bem estabelecidas, incluindo:
- Fortinet, Inc. (EUA)
- Cisco Systems, Inc. (EUA)
- Juniper Networks, Inc. (EUA)
- Palo Alto Networks, Inc. (EUA)
- IBM Corporation (EUA)
- Check Point Software Technologies Ltd. (Israel)
- F5, Inc. (EUA)
- Splunk, Inc. (EUA)
- Mandiant, Inc. (EUA)
- Broadcom, Inc. (EUA)
- Oracle Corporation (EUA)
- Microsoft Corporation (EUA)
- Intel Corporation (EUA)
- Imperva, Inc. (EUA)
- Cyberark Software Ltd. (EUA)
- RSA Security LLC (EUA)
Quais são os desenvolvimentos recentes no mercado global de segurança cibernética industrial?
- Em setembro de 2023, a Cisco Systems, Inc. anunciou sua intenção de adquirir a Splunk, empresa líder em segurança cibernética e observabilidade, por um valor patrimonial total de 1,2 bilhão. A aquisição, uma das maiores do ano, visa aprimorar significativamente os negócios de software da Cisco e acelerar sua estratégia de fornecer soluções de segurança e observabilidade habilitadas por IA. Ao combinar os recursos de análise de dados da Splunk com a infraestrutura de rede e segurança cibernética da Cisco, o acordo visa ajudar as organizações a passar da detecção e resposta a ameaças para a previsão e prevenção de ameaças, marcando uma grande mudança no cenário da segurança cibernética.
- Em agosto de 2023, a Johnson Controls emitiu um Aviso de Segurança de Produto referente a uma vulnerabilidade em seus produtos American Dynamics VideoEdge, identificada como CVE-2023-3749. A falha permite que um usuário local modifique o arquivo de configuração do VideoEdge, potencialmente interrompendo as operações do sistema. Todas as versões anteriores à 6.1.1 foram afetadas. Para mitigar o risco, a Johnson Controls recomendou aos clientes a atualização para a versão 6.1.1, disponível no portal de suporte da American Dynamics. Este aviso ressalta a importância de atualizações regulares de segurança e controle de acesso para proteger os sistemas de controle industrial e a infraestrutura de videovigilância.
- Em maio de 2023, a Agência de Segurança Cibernética e de Infraestrutura (CISA) divulgou seu Plano Estratégico para 2023-2025, marcando seu primeiro roteiro abrangente desde sua fundação em 2018. O plano define quatro objetivos principais: Defesa Cibernética, Redução de Riscos e Resiliência, Colaboração Operacional e Unificação da Agência. Ele enfatiza uma abordagem proativa e unificada para a segurança cibernética, com o objetivo de fortalecer a resiliência da infraestrutura crítica dos EUA por meio de uma colaboração estreita com agências federais e parceiros do setor privado. A estratégia da CISA reflete um compromisso progressista com a prevenção de ameaças, o compartilhamento de informações e a prontidão para a segurança nacional em um cenário digital cada vez mais complexo.
- Em abril de 2023, a Akamai Technologies, Inc. anunciou sua intenção de adquirir a Neosec, uma plataforma privada de detecção e resposta de APIs baseada em dados e análises comportamentais. A aquisição visa aprimorar o portfólio de segurança de aplicações e APIs da Akamai, proporcionando aos clientes maior visibilidade da atividade das APIs e permitindo que detectem ameaças em tempo real. A tecnologia da Neosec ajuda as organizações a descobrir APIs, avaliar riscos e responder a vulnerabilidades, abordando os crescentes desafios de segurança cibernética impostos por arquiteturas baseadas em APIs. Este movimento estratégico posiciona a Akamai na vanguarda da segurança de APIs orientada por IA, um segmento em rápida expansão na defesa digital.
- Em fevereiro de 2023, a Accenture adquiriu a Morphus, provedora brasileira de serviços de defesa cibernética, gestão de riscos e inteligência contra ameaças cibernéticas. A aquisição traz mais de 230 profissionais de segurança cibernética para a Accenture e quase dobra sua presença em segurança no Brasil, além de expandir sua presença na América Latina. A expertise da Morphus em serviços de equipes vermelhas e azuis, governança e serviços de segurança gerenciada fortalece a capacidade da Accenture de ajudar seus clientes a construir negócios ciber-resilientes. A mudança também marca o lançamento de uma Prática de Cibersegurança na região, reforçando o compromisso da Accenture com a liderança global em segurança cibernética.
SKU-
Obtenha acesso online ao relatório sobre a primeira nuvem de inteligência de mercado do mundo
- Painel interativo de análise de dados
- Painel de análise da empresa para oportunidades de elevado potencial de crescimento
- Acesso de analista de pesquisa para personalização e customização. consultas
- Análise da concorrência com painel interativo
- Últimas notícias, atualizações e atualizações Análise de tendências
- Aproveite o poder da análise de benchmark para um rastreio abrangente da concorrência
Metodologia de Investigação
A recolha de dados e a análise do ano base são feitas através de módulos de recolha de dados com amostras grandes. A etapa inclui a obtenção de informações de mercado ou dados relacionados através de diversas fontes e estratégias. Inclui examinar e planear antecipadamente todos os dados adquiridos no passado. Da mesma forma, envolve o exame de inconsistências de informação observadas em diferentes fontes de informação. Os dados de mercado são analisados e estimados utilizando modelos estatísticos e coerentes de mercado. Além disso, a análise da quota de mercado e a análise das principais tendências são os principais fatores de sucesso no relatório de mercado. Para saber mais, solicite uma chamada de analista ou abra a sua consulta.
A principal metodologia de investigação utilizada pela equipa de investigação do DBMR é a triangulação de dados que envolve a mineração de dados, a análise do impacto das variáveis de dados no mercado e a validação primária (especialista do setor). Os modelos de dados incluem grelha de posicionamento de fornecedores, análise da linha de tempo do mercado, visão geral e guia de mercado, grelha de posicionamento da empresa, análise de patentes, análise de preços, análise da quota de mercado da empresa, normas de medição, análise global versus regional e de participação dos fornecedores. Para saber mais sobre a metodologia de investigação, faça uma consulta para falar com os nossos especialistas do setor.
Personalização disponível
A Data Bridge Market Research é líder em investigação formativa avançada. Orgulhamo-nos de servir os nossos clientes novos e existentes com dados e análises que correspondem e atendem aos seus objetivos. O relatório pode ser personalizado para incluir análise de tendências de preços de marcas-alvo, compreensão do mercado para países adicionais (solicite a lista de países), dados de resultados de ensaios clínicos, revisão de literatura, mercado remodelado e análise de base de produtos . A análise de mercado dos concorrentes-alvo pode ser analisada desde análises baseadas em tecnologia até estratégias de carteira de mercado. Podemos adicionar quantos concorrentes necessitar de dados no formato e estilo de dados que procura. A nossa equipa de analistas também pode fornecer dados em tabelas dinâmicas de ficheiros Excel em bruto (livro de factos) ou pode ajudá-lo a criar apresentações a partir dos conjuntos de dados disponíveis no relatório.