Overview
The corporate sector, encompassing small and medium enterprises (SMEs), large enterprises, and various industry verticals, is facing an unprecedented increase in cyber-attacks. This escalation, accompanied by a surge in phishing activities, adversely impacts organizational reputation and erodes customer trust. This paper explores the scope, impact, and mitigation strategies for the growing cyber threats within the corporate digital ecosystem, providing an in-depth analysis of the challenges and recommending comprehensive solutions to safeguard digital assets.
The digital revolution has radically transformed the corporate landscape, offering new avenues for growth, efficiency, and innovation. However, this digitalization has also exposed organizations to significant cyber risks. Cyber-attacks, including data breaches, ransomware, and phishing, have become more frequent and sophisticated, targeting vulnerable systems across various industry verticals. The consequences are severe, affecting not only the financial stability of companies but also their reputation and customer trust.
This white paper aims to provide a detailed analysis of the rising threat of cyber-attacks on the corporate digital ecosystem. It will examine the current landscape of cyber threats, their impact on different sectors, the rise of phishing activities, and the adverse effects on organizational reputation and customer trust. Finally, it will discuss mitigation strategies that organizations can adopt to enhance their cybersecurity posture.
The Current Landscape of Cyber-Attacks
Increasing Frequency and Sophistication
Cyber-attacks are becoming increasingly common and sophisticated. According to the 2023 Data Breach Investigations Report by Verizon, the number of cyber incidents has grown exponentially over the past decade. Attackers are employing advanced tactics, techniques, and procedures (TTPs) to infiltrate corporate networks. The advent of technologies like artificial intelligence (AI) and machine learning (ML) has further empowered cybercriminals to conduct more sophisticated and targeted attacks.
Types of Cyber-Attacks
Fig 1: Types of Cyber-Attacks
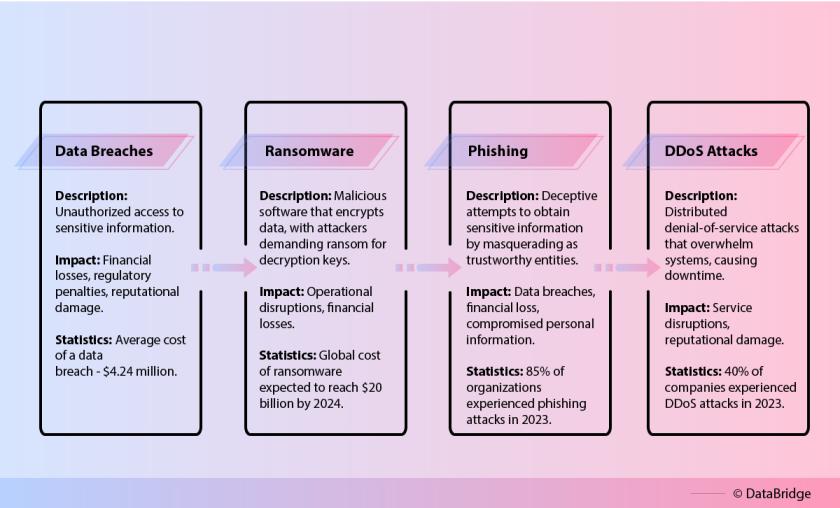
- Data Breaches: Unauthorized access to sensitive information, leading to financial losses and regulatory penalties. Data breaches are one of the most common forms of cyber-attacks, often resulting in significant reputational damage and loss of customer trust. According to IBM Security’s 2023 Cost of a Data Breach Report, the average cost of a data breach has reached $4.24 million.
- Ransomware: Malicious software that encrypts data, with attackers demanding ransom for decryption keys. Ransomware attacks have surged in recent years, targeting organizations across all sectors. These attacks can cripple business operations and result in substantial financial losses. The global cost of ransomware is expected to reach $20 billion by 2024, according to McAfee’s Global Threat Intelligence Report.
- Phishing: Deceptive attempts to obtain sensitive information by masquerading as trustworthy entities. Phishing remains one of the most prevalent and effective cyber-attack vectors. Modern phishing attacks are highly sophisticated, using social engineering techniques to deceive even the most cautious users.
- DDoS Attacks: Distributed denial-of-service attacks that overwhelm systems, causing downtime and service disruptions. DDoS attacks can be highly disruptive, impacting the availability of critical services and damaging an organization’s reputation.
Emerging Threats
The evolving threat landscape is characterized by the emergence of new and more sophisticated cyber threats. These include:
- Supply Chain Attacks: Cybercriminals target vulnerabilities in the supply chain to gain access to multiple organizations through a single attack. These attacks can have widespread and devastating effects, as demonstrated by the SolarWinds attack in 2020.
- IoT Vulnerabilities: The proliferation of Internet of Things (IoT) devices has introduced new security challenges. Many IoT devices lack robust security measures, making them attractive targets for cybercriminals.
- AI and ML-based Attacks: Attackers are leveraging AI and ML to develop more sophisticated and targeted attacks. These technologies enable cybercriminals to automate and scale their attacks, making them more effective and harder to detect.
Impact on Different Sectors
Small and Medium Enterprises (SMEs)
SMEs often lack the robust cybersecurity infrastructure of larger enterprises, making them attractive targets for cybercriminals. According to a report by the Ponemon Institute, 60% of small businesses that experience a cyber-attack go out of business within six months. The financial impact of a cyber-attack on an SME can be devastating, potentially leading to business closure. SMEs face several challenges in managing cybersecurity, including limited resources, lack of expertise, and inadequate security measures.
Large Enterprises
While large enterprises may have more resources to invest in cybersecurity, they are also prime targets due to the vast amount of data they hold. A successful attack on a large enterprise can result in significant financial losses, operational disruptions, and long-term reputational damage. For example, the Equifax data breach in 2017 exposed the personal information of 147 million people, resulting in a $1.4 billion settlement and irreparable damage to the company’s reputation.
Fig 2: Impact on different sectors
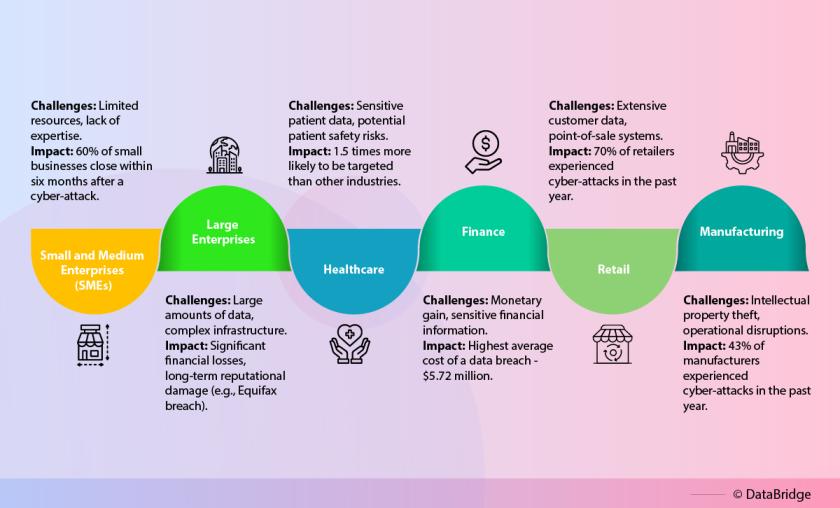
Industry Verticals
Different industry verticals face unique cyber threats:
- Healthcare: The healthcare sector is targeted for sensitive patient data, with attacks potentially jeopardizing patient safety. According to the 2023 Healthcare Cybersecurity Report by Symantec, healthcare organizations are 1.5 times more likely to be targeted by cyber-attacks than other industries.
- Finance: The financial sector is a prime target for cybercriminals due to the potential for monetary gain and access to sensitive financial information. Financial institutions face a range of cyber threats, including data breaches, ransomware, and DDoS attacks. The 2023 Financial Services Cybersecurity Report by McAfee highlights that the financial sector experiences the highest average cost of a data breach, at $5.72 million.
- Retail: The retail sector is vulnerable due to extensive customer data and point-of-sale systems. Cyber-attacks on retailers can result in significant financial losses and damage to customer trust. The 2023 Retail Cybersecurity Report by IBM Security found that 70% of retailers experienced a cyber-attack in the past year.
- Manufacturing: The manufacturing sector faces risks including intellectual property theft and operational disruptions. Cyber-attacks on manufacturing facilities can result in significant production downtime and financial losses. The 2023 Manufacturing Cybersecurity Report by Symantec highlights that 43% of manufacturers experienced a cyber-attack in the past year.
The Rise of Phishing Activities
Phishing remains one of the most prevalent and effective cyber-attack vectors. Modern phishing attacks are highly sophisticated, using social engineering techniques to deceive even the most cautious users. The rise of phishing can be attributed to several factors, including the increasing use of digital communication channels, the growing sophistication of phishing techniques, and the widespread availability of phishing kits on the dark web.
Types of Phishing Attacks
- Email Phishing: The most common form of phishing, where attackers send deceptive emails to trick recipients into providing sensitive information or clicking on malicious links.
- Spear Phishing: A targeted form of phishing that involves personalized emails aimed at specific individuals or organizations. Spear phishing attacks are more sophisticated and harder to detect than traditional phishing attacks.
- Whaling: A type of spear phishing that targets high-profile individuals, such as executives and senior management. Whaling attacks often involve significant research and social engineering to craft convincing messages.
- Clone Phishing: Attackers create a replica of a legitimate email, replacing links or attachments with malicious ones. This type of phishing is particularly effective because it leverages the trust established by previous communications.
- Vishing and Smishing: Phishing attacks conducted via voice calls (vishing) or SMS messages (smishing). These attacks exploit the growing use of mobile devices and the trust users place in voice and text communications.
Adverse Effects on Organizational Reputation and Customer Trust
Organizational Reputation
A cyber-attack can severely damage an organization's reputation. News of a breach can erode stakeholder confidence, affect stock prices, and lead to loss of business partnerships. The public perception of a company's ability to safeguard data is crucial in maintaining a competitive edge. The reputational damage caused by a cyber-attack can have long-lasting effects, impacting an organization’s ability to attract and retain customers, employees, and investors.
For instance,
- The Equifax data breach in 2017 serves as a prime example of the reputational damage that can result from a cyber-attack. The breach exposed the personal information of 147 million people, leading to widespread public outrage and a significant decline in the company’s reputation. Equifax’s stock price plummeted by more than 30% in the immediate aftermath of the breach, and the company faced numerous lawsuits and regulatory penalties.
Customer Trust
Customers entrust organizations with their personal and financial information. A breach of this trust can lead to a loss of customer loyalty and a decline in business. Companies must demonstrate a commitment to cybersecurity to retain and attract customers in an increasingly digital world. The loss of customer trust can have significant financial implications, as customers may choose to take their business to competitors perceived as more secure.
For instance,
- The 2023 Consumer Trust Survey by PwC found that 85% of consumers would not do business with a company if they were concerned about its security practices. This highlights the importance of maintaining robust cybersecurity measures to protect customer data and preserve trust. Organizations must prioritize transparency and communication in the event of a cyber-attack, providing timely and accurate information to affected customers and stakeholders.
Mitigation Strategies
Enhancing Cybersecurity Measures
- Investment in Technology: Deploying advanced security technologies such as AI, ML, and blockchain to detect and prevent cyber threats. AI and ML can be used to identify patterns and anomalies in network traffic, enabling organizations to detect and respond to threats in real-time. Blockchain technology can enhance security by providing a tamper-proof ledger of transactions and data.
- Employee Training: Educating employees on cybersecurity best practices and phishing awareness is critical. Employees are often the first line of defense against cyber threats, and comprehensive training programs can help them recognize and respond to potential threats. Regularly updating training materials and conducting simulated phishing exercises can reinforce these practices and ensure employees remain vigilant.
- Incident Response Plans: Developing and regularly updating incident response strategies to quickly and effectively respond to cyber incidents. An effective incident response plan should include clear protocols for detecting, reporting, and mitigating cyber threats, as well as guidelines for communication and coordination among internal and external stakeholders. Regularly testing and refining the plan through tabletop exercises and simulations can improve an organization’s readiness to handle real-world cyber incidents.
- Network Segmentation: Implementing network segmentation to limit the spread of cyber threats within an organization. By dividing the network into smaller, isolated segments, organizations can contain and mitigate the impact of cyber-attacks, reducing the risk of widespread data breaches and operational disruptions.
- Endpoint Security: Enhancing endpoint security by deploying advanced security solutions, such as next-generation antivirus, endpoint detection and response (EDR) systems, and mobile device management (MDM) tools. These solutions can help organizations monitor and protect endpoints, such as laptops, smartphones, and tablets, against cyber threats.
- Multi-Factor Authentication (MFA): Implementing MFA to add an extra layer of security to user authentication processes. MFA requires users to provide two or more forms of verification before gaining access to systems and data, making it more difficult for cybercriminals to compromise accounts.
- Zero Trust Architecture: Adopting a zero trust approach to cybersecurity, which assumes that threats can exist both inside and outside the network perimeter. Zero trust architecture requires continuous verification of user identities and strict access controls to ensure that only authorized users can access sensitive data and systems.
- Regular Security Audits and Assessments: Conducting regular security audits and assessments to identify and address vulnerabilities in an organization’s cybersecurity posture. These assessments can help organizations stay ahead of emerging threats and ensure compliance with industry standards and regulatory requirements.
Regulatory Compliance
Adhering to regulatory requirements and industry standards is crucial for maintaining a strong cybersecurity posture. Organizations should stay informed about the latest regulations and ensure compliance to avoid penalties and enhance security. Key regulations and standards include:
- General Data Protection Regulation (GDPR): A comprehensive data protection regulation that applies to organizations operating in the European Union (EU) or processing the personal data of EU residents. GDPR mandates strict data protection measures and imposes significant penalties for non-compliance.
- Health Insurance Portability and Accountability Act (HIPAA): A U.S. regulation that sets standards for the protection of sensitive patient data in the healthcare sector. HIPAA requires healthcare organizations to implement robust security measures to safeguard patient information and ensure data privacy.
- Payment Card Industry Data Security Standard (PCI DSS): A set of security standards designed to protect payment card information. Organizations that process, store, or transmit payment card data must comply with PCI DSS requirements to ensure the security of cardholder data.
- Sarbanes-Oxley Act (SOX): A U.S. regulation that imposes strict financial reporting and data protection requirements on publicly traded companies. SOX mandates the implementation of internal controls and security measures to protect financial data and ensure the integrity of financial reporting.
- NIST Cybersecurity Framework: A voluntary framework developed by the National Institute of Standards and Technology (NIST) to help organizations manage and reduce cybersecurity risk. The framework provides a set of best practices and guidelines for improving cybersecurity posture and enhancing resilience.
Collaboration and Information Sharing
Participating in industry-wide collaborations and information-sharing initiatives can help organizations stay ahead of emerging threats. Sharing threat intelligence and best practices can strengthen the collective cybersecurity resilience of the corporate sector. Key initiatives and organizations include:
- Information Sharing and Analysis Centers (ISACs): Industry-specific organizations that facilitate the sharing of cybersecurity threat information and best practices among member organizations. ISACs play a crucial role in enhancing situational awareness and promoting collaboration within industry sectors.
- Cybersecurity and Infrastructure Security Agency (CISA): A U.S. government agency that provides cybersecurity resources, tools, and information to help organizations protect their critical infrastructure. CISA offers a range of services, including threat intelligence, incident response support, and cybersecurity training.
- Center for Internet Security (CIS): A nonprofit organization that develops best practices, guidelines, and tools to help organizations improve their cybersecurity posture. CIS offers a range of resources, including the CIS Controls and CIS Benchmarks, which provide actionable guidance for enhancing security.
- Cyber Threat Alliance (CTA): A consortium of cybersecurity companies that share threat intelligence and collaborate on efforts to combat cyber threats. The CTA aims to improve the overall cybersecurity landscape by promoting cooperation and information sharing among its members.
Conclusion
The increasing number of cyber-attacks on the corporate digital ecosystem poses significant risks to organizations across all sectors. The rise in phishing activities exacerbates these threats, adversely affecting organizational reputation and reducing customer trust. To combat these challenges, organizations must invest in advanced cybersecurity measures, foster a culture of security awareness, comply with regulatory standards, and collaborate with industry peers. By adopting a proactive and comprehensive approach to cybersecurity, businesses can protect their digital assets, maintain customer trust, and safeguard their reputation in an increasingly digital world.

