伊拉克物理安全市场,按组件(硬件、服务和软件)、身份验证(单因素身份验证、双因素身份验证和三因素身份验证)、部署模型(本地和云)、企业规模(大型企业和中小型企业)、最终用户(商业、政府、工业和住宅)划分 - 行业趋势和预测到 2029 年。
伊拉克实体安全市场分析及规模
物理安全措施保护建筑物及其内部设备。换句话说,它们阻止非法入侵者进入,并允许授权人员进入。虽然网络和网络安全至关重要,但防范物理安全漏洞和威胁是确保技术、数据以及任何有权访问该设施的工作人员或教职员工安全的唯一方法。它可以防御恐怖主义、火灾、抢劫、破坏和自然灾害。
Data Bridge Market Research 分析称,预计到 2029 年,伊拉克实体安全市场价值将达到 5.0444 亿美元,预测期内复合年增长率为 7.9%。实体安全市场报告还全面涵盖了定价、专利和技术进步。
|
报告指标 |
细节 |
|
预测期 |
2022 至 2029 年 |
|
基准年 |
2021 |
|
历史岁月 |
2020 (可定制为 2019-2014) |
|
定量单位 |
收入(百万美元),定价(美元) |
|
涵盖的领域 |
按组件(硬件、服务和软件)、身份验证(单因素身份验证、双因素身份验证和三因素身份验证)、部署模型(本地和云)、企业规模(大型企业和中小型企业)、最终用户(商业、政府、工业和住宅) |
|
涵盖的市场参与者 |
泰雷兹、HID Global Corporation、Bosch Sicherheitssysteme GmbH、杭州海康威视数字技术股份有限公司、Pelco(摩托罗拉解决方案公司旗下子公司)、思科系统公司、Axis Communications AB、江森自控、Aware, Inc.、IDEMIA |
市场定义
物理安全是一种安全服务,旨在保护人员、硬件、软件、网络和数据免受可能对组织、企业、机构或机构造成严重损失的物理行为和事件的影响。这些安全服务包括防火、防洪、防自然灾害、防盗窃、防破坏和防恐怖主义。安全人员、闭路电视摄像机、锁、安全屏障、访问控制协议和其他类似工具都包含在其各个层级中,这些层级包含相互依赖的系统。
伊拉克实体安全市场动态
本节旨在了解市场驱动因素、优势、机遇、限制和挑战。下面将详细讨论所有这些内容:
驱动程序
- 智能互联建筑/家居的出现
最近,智能家居/智能建筑在消费者中越来越受欢迎。智能家居/智能建筑是指使用联网设备实现远程监控、门禁解决方案以及家电和系统管理(例如智能照明、智能锁、智能生物识别等)的住宅。
此外,智能家居设备高效节能,可减少能源费用。智能家居设备具有创新功能、内置运动探测器、互联网连接以及通过智能手机、笔记本电脑和其他设备进行控制,让消费者感到安全、舒适和安心。
- 物理生物识别解决方案在所有行业中的重要性迅速增长
基于生物识别技术的物理安全设备正在全球各个地区不断增加。指纹、物理门禁系统、视频监控系统和面部识别系统与笔记本电脑、手机和其他智能手持设备等电子设备集成在一起。智能方法还使用这些门禁门锁、安全系统、家庭自动化、物联网、汽车、游戏机和移动设备。
有了门禁门锁,人们就可以通过增强安全功能快速识别和进入房屋或组织。各公司正在进行许多研究活动,以将先进的物理生物识别系统整合到设备中,以确保安全。
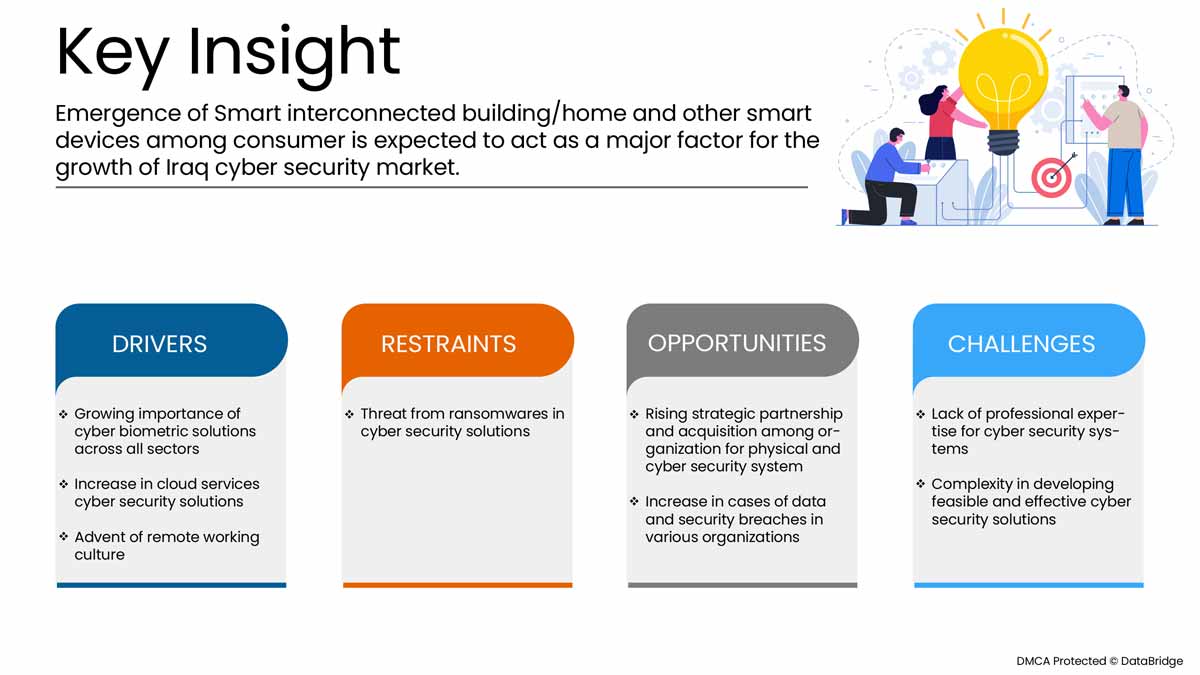
机会
- 物理和网络安全系统组织之间的战略伙伴关系和收购增加
协调和投资项目对于实现物理安全市场的持续改善至关重要。因此,政府和其他私人组织正在努力通过合作和收购来加速行业的发展。这有助于为组织建立知名度和利润,从而为行业的新发明创造空间。此外,公司可以通过合作在先进技术上投入更多资金,以提供更安全可靠的物理安全市场服务和解决方案。
扩大业务可以让更多人接触到公司的产品和服务。通过扩大客户群,他们将能够吸引更多客户并提高销售额。这有助于提高知名度,增加组织的利润,并为可持续增长创造空间。此外,这还能让公司在高端市场获得认可。
限制/挑战
- 物理和网络安全解决方案中网络安全威胁和勒索软件的增加
由于 COVID-19,2020 年网络犯罪和网络安全问题增加了 600%。网络安全漏洞是黑客利用来在系统内执行未经授权的操作的弱点。根据 Purple Sec LLC 的数据,2018 年,针对移动设备的移动恶意软件变种增加了 54%,其中 98% 的移动恶意软件针对 Android 设备。据估计,25% 的企业成为加密劫持的受害者。各种公司还包括安全行业。
- 各种物理安全系统集成的复杂性
集成安全系统涉及将逻辑和物理安全应用程序(例如生物识别程序和访问控制)组合成一个包罗万象的计划。例如,如果访问控制和入侵警报系统相连,则可以对访问控制系统进行编程,使其根据系统确定入侵者时发出的警报声音类型锁定设施。但是,必须从同一家供应商处购买所有组件。如果供应商仅提供最低限度的支持,客户可能会被一个无法满足其需求的系统所困扰。此外,重新设计和重新部署基于 Web 和移动的应用程序可能会变得繁琐且耗时。
新冠肺炎疫情对伊拉克实体安防市场的影响
由于封锁规定和制造工厂的关闭,COVID-19 对物理安全市场产生了负面影响。
COVID-19 疫情在一定程度上对实体安防市场产生了积极影响。全球各行业对视频监控系统的需求激增,推动了市场在疫情期间的增长。此外,由于商业和工业环境中越来越多地采用访问控制协议,自 COVID-19 疫情后市场开放以来,增长一直很高。
解决方案提供商正在制定各种战略决策,以在新冠疫情后实现复苏。参与者正在进行多项研发活动,以改进物理安全技术。借助这些技术,这些公司将把先进技术推向市场。此外,政府使用自动化技术的举措也推动了市场的增长。
最新动态
- 2021 年 10 月,霍尼韦尔与 IDEMIA 合作开发智能建筑产品。根据合作伙伴关系,产品已针对建筑出入进行设置,将霍尼韦尔安全和建筑管理系统与 IDEMIA 的基于生物识别的出入控制系统集成在一起。这有助于该公司实现产品组合多元化,并在建筑出入控制市场开辟新市场
- 2020 年 8 月,摩托罗拉系统公司以 1.1 亿美元收购了 Pelco 公司。此次收购旨在将 Pelco 提供的视频管理解决方案国际化。此外,摩托罗拉系统公司使 Pelco 公司成为物理安全市场的主要子公司之一。通过这种方式,两家公司通过为消费者提供创新解决方案进一步增强了其市场影响力
伊拉克物理安全市场范围
伊拉克物理安全市场根据组件、身份验证、部署模型、企业规模和最终用户进行细分。这些细分市场之间的增长将帮助您分析行业中增长微弱的细分市场,并为用户提供有价值的市场概览和市场洞察,帮助他们做出战略决策,确定核心市场应用。
成分
- 硬件
- 服务
- 软件
根据组成部分,伊拉克物理安全市场分为硬件、服务和软件。
验证
- 单因素身份验证
- 双重身份验证
- 三因素身份验证
根据身份验证,伊拉克物理安全市场细分为单因素身份验证、双因素身份验证和三因素身份验证。
部署模型
- 本地
- 云
根据部署模式,伊拉克物理安全市场分为本地和云端。
企业规模
- 大型企业
- 中小企业
根据企业规模,伊拉克实体安全市场分为大型企业和中小型企业。
最终用户
- 商业的
- 政府
- 工业的
- 住宅
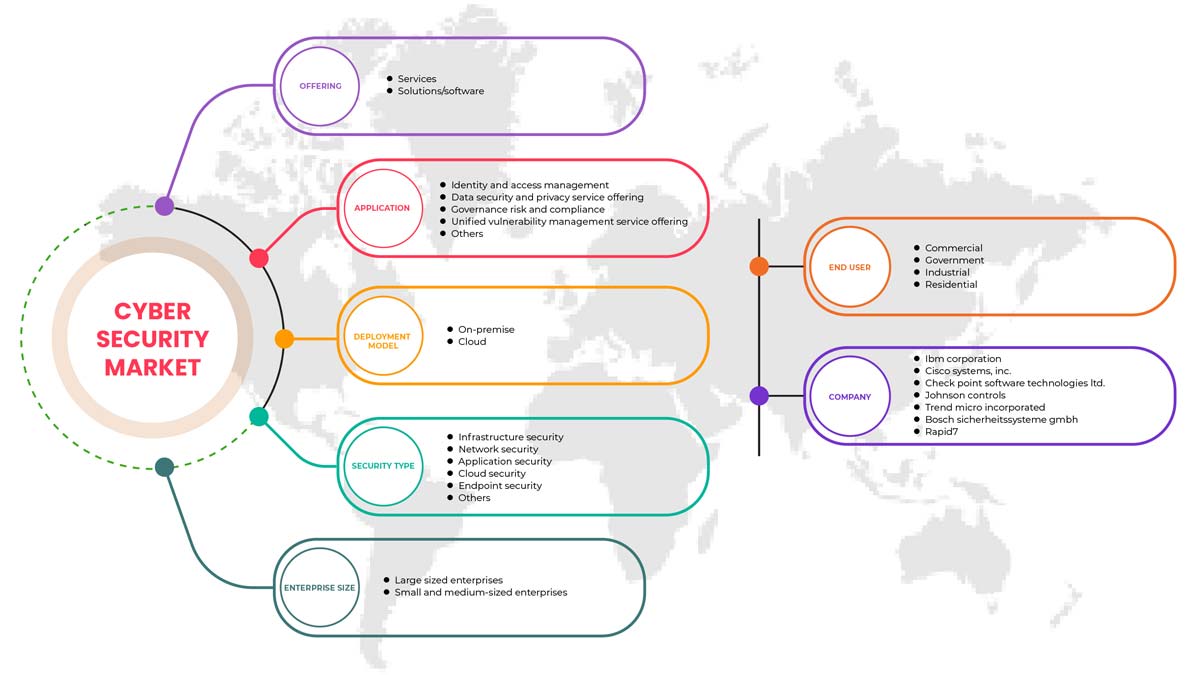
根据最终用户,伊拉克物理安全市场分为商业、政府、工业和住宅。
伊拉克物理安全市场区域分析/见解
对伊拉克物理安全市场进行了分析,并按国家、组件、身份验证、部署类型、企业规模和最终用户提供了市场规模洞察和趋势,如上所述。
报告的国家部分还提供了影响市场当前和未来趋势的各个市场影响因素和市场监管变化。下游和上游价值链分析、技术趋势、波特五力分析和案例研究等数据点是用于预测各个国家市场情景的一些指标。此外,在提供国家数据的预测分析时,还考虑了伊拉克品牌的存在和可用性以及由于来自本地和国内品牌的大量或稀缺竞争而面临的挑战、国内关税的影响和贸易路线。
竞争格局和伊拉克物理安全市场份额分析
伊拉克实体安全市场竞争格局提供了竞争对手的详细信息。 其中包括公司概况、公司财务状况、收入、市场潜力、研发投资、新市场计划、伊拉克业务、生产基地和设施、生产能力、公司优势和劣势、产品发布、产品宽度和广度、应用主导地位。 以上提供的数据点仅与公司对实体安全市场的关注有关。
伊拉克物理安全市场的一些主要参与者包括泰雷兹公司、HID Global Corporation、博世安全系统有限公司、杭州海康威视数字技术股份有限公司、派尔高公司(摩托罗拉解决方案公司旗下子公司)、思科系统公司、安讯士公司、江森自控、Aware 公司、IDEMIA 等。
SKU-
Get online access to the report on the World's First Market Intelligence Cloud
- Interactive Data Analysis Dashboard
- Company Analysis Dashboard for high growth potential opportunities
- Research Analyst Access for customization & queries
- Competitor Analysis with Interactive dashboard
- Latest News, Updates & Trend analysis
- Harness the Power of Benchmark Analysis for Comprehensive Competitor Tracking
目录
1 INTRODUCTION
1.1 OBJECTIVES OF THE STUDY
1.2 MARKET DEFINITION
1.3 OVERVIEW OF IRAQ PHYSICAL AND CYBER SECURITY MARKET
1.4 CURRENCY AND PRICING
1.5 LIMITATIONS
1.6 MARKETS COVERED
2 MARKET SEGMENTATION
2.1 MARKETS COVERED
2.2 GEOGRAPHICAL SCOPE
2.3 YEARS CONSIDERED FOR THE STUDY
2.4 DBMR TRIPOD DATA VALIDATION MODEL
2.5 PRIMARY INTERVIEWS WITH KEY OPINION LEADERS
2.6 DBMR MARKET POSITION GRID
2.7 VENDOR SHARE ANALYSIS
2.8 MARKET END USER COVERAGE GRID
2.9 MULTIVARIATE MODELING
2.1 COMPONENT TIMELINE CURVE
2.11 OFFERING TIMELINE CURVE
2.12 SECONDARY SOURCES
2.13 ASSUMPTIONS
3 EXECUTIVE SUMMARY
4 PREMIUM INSIGHTS
4.1 INVESTMENT POLICY
4.1 CASE STUDY
4.1.1 SECURE SOFTWARE DEVELOPMENT INFRASTRUCTURE
4.1.2 SOC-AS-A-PLATFORM (SOCAAP)
4.1.3 RANSOMWARE & FORENSICS ANALYSIS
4.1.4 WISCONSIN'S DEER DISTRICT SECURITY PLAN
4.1.5 LICENSE PLATE READERS IN SCHOOLS
4.1.6 K-12 SCHOOLS
4.2 VALUE CHAIN ANALYSIS
4.3 PORTERS FIVE FORCES
4.4 PESTLE ANALYSIS
4.5 TECHNOLOGICAL LANDSCAPE
4.5.1 AI AND MACHINE LEARNING
4.5.2 IOT
4.5.3 BLOCKCHAIN
4.6 REGULATORY STANDARDS
4.6.1 CYBER SECURITY
4.6.2 PHYSICAL SECURITY
4.7 LOCAL PLAYERS LIST
5 MARKET OVERVIEW
5.1 DRIVERS
5.1.1 ADVENT OF REMOTE WORKING CULTURE
5.1.2 INCREASE IN CLOUD SERVICES CYBER AND PHYSICAL SECURITY SOLUTIONS
5.1.3 GROWING IMPORTANCE OF PHYSICAL BIOMETRIC SOLUTIONS ACROSS ALL SECTORS
5.1.4 EMERGENCE OF SMART INTERCONNECTED BUILDING/HOME
5.2 RESTRAINTS
5.2.1 RISE IN CYBER SECURITY THREAT AND RANSOMWARE IN PHYSICAL AND CYBER SECURITY SOLUTIONS
5.3 OPPORTUNITIES
5.3.1 RISING STRATEGIC PARTNERSHIP AND ACQUISITION AMONG ORGANIZATIONS FOR PHYSICAL AND CYBER SECURITY SYSTEM
5.3.2 EMERGENCE OF VARIOUS DISRUPTIVE TECHNOLOGY SUCH AS IOT AND AI FOR VARIOUS INDUSTRIES
5.3.3 INCREASE IN CASES OF DATA AND SECURITY BREACHES IN VARIOUS ORGANIZATIONS
5.4 CHALLENGES
5.4.1 LACK OF PROFESSIONAL EXPERTISE FOR CYBER SECURITY SYSTEMS
5.4.2 COMPLEXITY ASSOCIATED WITH THE INTEGRATION OF VARIOUS PHYSICAL SECURITY SYSTEMS
6 IRAQ CYBER SECURITY MARKET, BY OFFERING
6.1 OVERVIEW
6.2 SERVICES
6.3 SOLUTIONS/SOFTWARE
7 IRAQ PHYSICAL SECURITY MARKET, BY COMPONENT
7.1 OVERVIEW
7.2 HARDWARE
7.2.1 VIDEO SURVEILLANCE SYSTEM
7.2.1.1 CAMERAS
7.2.1.2 RECORDERS
7.2.2 PHYSICAL ACCESS CONTROL SYSTEM
7.2.2.1 BIOMETRICS
7.2.2.2 LOCKS
7.2.2.2.1 ELECTRONIC LOCKS
7.3 SERVICES
7.3.1 MANAGED SERVICES
7.3.2 PROFESSIONAL SERVICES
7.4 SOFTWARE
8 IRAQ PHYSICAL SECURITY MARKET, BY AUTHENTICATION
8.1 OVERVIEW
8.2 SINGLE- FACTOR AUTHENTICATION
8.3 TWO- FACTOR AUTHENTICATION
8.4 THREE- FACTOR AUTHENTICATION
9 IRAQ CYBER SECURITY MARKET, BY APPLICATION
9.1 OVERVIEW
9.2 IDENTITY AND ACCESS MANAGEMENT
9.3 DATA SECURITY AND PRIVACY SERVICE OFFERING
9.4 GOVERNANCE RISK AND COMPLIANCE
9.5 UNIFIED VULNERABILITY MANAGEMENT SERVICE OFFERING
9.6 OTHERS
10 IRAQ CYBER SECURITY MARKET, BY SECURITY TYPE
10.1 OVERVIEW
10.2 INFRASTRUCTURE SECURITY
10.3 NETWORK SECURITY
10.4 APPLICATION SECURITY
10.5 CLOUD SECURITY
10.6 ENDPOINT SECURITY
10.7 OTHERS
11 IRAQ PHYSICAL AND CYBER SECURITY MARKET, BY DEPLOYMENT MODEL
11.1 OVERVIEW
11.2 ON-PREMISE
11.3 CLOUD
12 IRAQ PHYSICAL AND CYBER SECURITY MARKET, BY ENTERPRISE SIZE
12.1 OVERVIEW
12.2 LARGE SIZED ENTERPRISES
12.3 SMALL AND MEDIUM-SIZED ENTERPRISES
13 IRAQ PHYSICAL AND CYBER SECURITY MARKET, BY END USER
13.1 OVERVIEW
13.2 COMMERCIAL
13.3 GOVERNMENT
13.4 INDUSTRIAL
13.5 RESIDENTIAL
14 IRAQ CYBER SECURITY MARKET, COMPANY LANDSCAPE
14.1 COMPANY SHARE ANALYSIS: IRAQ
15 IRAQ PHYSICAL SECURITY MARKET, COMPANY LANDSCAPE
15.1 COMPANY SHARE ANALYSIS: IRAQ
16 SWOT ANALYSIS
16.1 DBMR ANALYSIS
16.1.1 STRENGTH
16.1.2 WEAKNESS
16.1.3 THREATS
16.1.4 OPPORTUNITY
17 COMPANY PROFILE
17.1 THALES GROUP
17.1.1 COMPANY SNAPSHOT
17.1.2 REVENUE ANALYSIS
17.1.3 PRODUCTS PORTFOLIO
17.1.4 RECENT DEVELOPMENTS
17.2 HANGZHOU HIKVISION DIGITAL TECHNOLOGY CO., LTD
17.2.1 COMPANY SNAPSHOT
17.2.2 REVENUE ANALYSIS
17.2.3 PRODUCT PORTFOLIO
17.2.4 RECENT DEVELOPMENTS
17.3 ACCENTURE
17.3.1 COMPANY SNAPSHOT
17.3.2 REVENUE ANALYSIS
17.3.3 SERVICE PORTFOLIO
17.3.4 RECENT DEVELOPMENTS
17.4 IDEMIA
17.4.1 COMPANY SNAPSHOT
17.4.2 PRODUCT PORTFOLIO
17.4.3 RECENT DEVELOPMENTS
17.5 BAE SYSTEMS
17.5.1 COMPANY SNAPSHOT
17.5.2 REVENUE ANALYSIS
17.5.3 SERVICE PORTFOLIO
17.5.4 RECENT DEVELOPMENT
17.6 FORTINET, INC.
17.6.1 COMPANY SNAPSHOT
17.6.2 REVENUE ANALYSIS
17.6.3 SERVICE PORTFOLIO
17.6.4 RECENT DEVELOPMENTS
17.7 PALO ALTO NETWORKS
17.7.1 COMPANY SNAPSHOT
17.7.2 REVENUE ANALYSIS
17.7.3 PRODUCT PORTFOLIO
17.7.4 RECENT DEVELOPMENT
17.8 AWARE, INC.
17.8.1 COMPANY SNAPSHOT
17.8.2 REVENUE ANALYSIS
17.8.3 PRODUCT PORTFOLIO
17.8.4 RECENT DEVELOPMENTS
17.9 AXIS COMMUNICATIONS AB
17.9.1 COMPANY SNAPSHOT
17.9.2 REVENUE ANALYSIS
17.9.3 PRODUCT PORTFOLIO
17.9.4 RECENT DEVELOPMENT
17.1 BOSCH SICHERHEITSSYSTEME GMBH
17.10.1 COMPANY SNAPSHOT
17.10.2 REVENUE ANALYSIS
17.10.3 PRODUCTS PORTFOLIO
17.10.4 RECENT DEVELOPMENT
17.11 CHECK POINT SOFTWARE TECHNOLOGIES LTD.
17.11.1 COMPANY SNAPSHOT
17.11.2 REVENUE ANALYSIS
17.11.3 PRODUCTS PORTFOLIO
17.11.4 RECENT DEVELOPMENTS
17.12 CISCO SYSTEMS, INC.
17.12.1 COMPANY SNAPSHOT
17.12.2 REVENUE ANALYSIS
17.12.3 PRODUCTS PORTFOLIO
17.12.4 RECENT DEVELOPMENTS
17.13 HEXAGON AB
17.13.1 COMPANY SNAPSHOT
17.13.2 REVENUE ANALYSIS
17.13.3 OFFERING PORTFOLIO
17.13.4 RECENT DEVELOPMENT
17.14 HID GLOBAL CORPORATION
17.14.1 COMPANY SNAPSHOT
17.14.2 PRODUCT PORTFOLIO
17.14.3 RECENT DEVELOPMENT
17.15 IBM CORPORATION
17.15.1 COMPANY SNAPSHOT
17.15.2 REVENUE ANALYSIS
17.15.3 PRODUCTS PORTFOLIO
17.15.4 RECENT DEVELOPMENTS
17.16 JOHNSON CONTROL
17.16.1 COMPANY SNAPSHOT
17.16.2 REVENUE ANALYSIS
17.16.3 PRODUCTS PORTFOLIO
17.16.4 RECENT DEVELOPMENTS
17.17 JUNIPER NETWORKS, INC.
17.17.1 COMPANY SNAPSHOT
17.17.2 REVENUE ANALYSIS
17.17.3 PRODUCTS PORTFOLIO
17.17.4 RECENT DEVELOPMENTS
17.18 MCAFEE, LLC
17.18.1 COMPANY SNAPSHOT
17.18.2 REVENUE ANALYSIS
17.18.3 PRODUCTS PORTFOLIO
17.18.4 RECENT DEVELOPMENTS
17.19 MICRO FOCUS
17.19.1 COMPANY SNAPSHOT
17.19.2 REVENUE ANALYSIS
17.19.3 PRODUCT PORTFOLIO
17.19.4 RECENT DEVELOPMENT
17.2 MICROSOFT
17.20.1 COMPANY SNAPSHOT
17.20.2 REVENUE ANALYSIS
17.20.3 PRODUCT PORTFOLIO
17.20.4 RECENT DEVELOPMENTS
17.21 ORACLE
17.21.1 COMPANY SNAPSHOT
17.21.2 REVENUE ANALYSIS
17.21.3 SERVICE CATEGORY
17.21.4 RECENT DEVELOPMENT
17.22 PELCO CORPORATIONS
17.22.1 COMPANY SNAPSHOT
17.22.2 REVENUE ANALYSIS
17.22.3 PRODUCTS PORTFOLIO
17.22.4 RECENT DEVELOPMENTS
17.23 RAPID7
17.23.1 COMPANY SNAPSHOT
17.23.2 REVENUE ANALYSIS
17.23.3 PRODUCT PORTFOLIO
17.23.4 RECENT DEVELOPMENTS
17.24 SPLUNK INC.
17.24.1 COMPANY SNAPSHOT
17.24.2 REVENUE ANALYSIS
17.24.3 PRODUCTS PORTFOLIO
17.24.4 RECENT DEVELOPMENT
17.25 TREND MICRO INCORPORATED
17.25.1 COMPANY SNAPSHOT
17.25.2 REVENUE ANALYSIS
17.25.3 PRODUCTS PORTFOLIO
17.25.4 RECENT DEVELOPMENTS
18 QUESTIONNAIRE
19 RELATED REPORTS
表格列表
TABLE 1 LIST OF LOCAL CYBER SECURITY PLAYERS
TABLE 2 LIST OF LOCAL PHYSICAL SECURITY PLAYERS
TABLE 3 IRAQ CYBER SECURITY MARKET, BY OFFERING, 2020-2029 (USD MILLION)
TABLE 4 IRAQ SERVICES IN CYBER SECURITY MARKET, BY TYPE, 2020-2029 (USD MILLION)
TABLE 5 IRAQ SOLUTIONS/SOFTWARE IN CYBER SECURITY MARKET, BY TYPE, 2020-2029 (USD MILLION)
TABLE 6 IRAQ PHYSICAL SECURITY MARKET, BY COMPONENT, 2020-2029 (USD MILLION)
TABLE 7 IRAQ HARWARE IN PHYSICAL SECURITY MARKET, BY TYPE, 2020-2029 (USD MILLION)
TABLE 8 IRAQ VIDEO SURVEILLANCE SYSTEM IN HARDWRAE PHYSICAL SECURITY MARKET, BY TYPE, 2020-2029 (USD MILLION)
TABLE 9 IRAQ CAMERAS IN VIDEO SURVEILLANCE SYSTEM PHYSICAL SECURITY MARKET, BY TYPE, 2020-2029 (USD MILLION)
TABLE 10 IRAQ RECORDERS IN VIDEO SURVEILLANCE SYSTEM PHYSICAL SECURITY MARKET, BY TYPE, 2020-2029 (USD MILLION)
TABLE 11 IRAQ PHYSICAL ACCESS CONTROL SYSTEM IN PHYSICAL SECURITY MARKET, BY TYPE, 2020-2029 (USD MILLION)
TABLE 12 IRAQ BIOMETRICS IN PHYSICAL ACCESS CONTROL SYSTEM PHYSICAL SECURITY MARKET, BY TYPE, 2020-2029 (USD MILLION)
TABLE 13 IRAQ LOCKS IN PHYSICAL ACCESS CONTROL SYSTEM PHYSICAL SECURITY MARKET, BY TYPE, 2020-2029 (USD MILLION)
TABLE 14 IRAQ ELECTRONIC LOCKS IN LOCKS PHYSICAL SECURITY MARKET, BY TYPE, 2020-2029 (USD MILLION)
TABLE 15 IRAQ SERVICES IN PHYSICAL SECURITY MARKET, BY TYPE, 2020-2029 (USD MILLION)
TABLE 16 IRAQ MANAGED SERVICES IN SERVICES PHYSICAL SECURITY MARKET, BY TYPE, 2020-2029 (USD MILLION)
TABLE 17 IRAQ PROFESSIONAL SERVICES IN SERVICES PHYSICAL SECURITY MARKET, BY TYPE, 2020-2029 (USD MILLION)
TABLE 18 IRAQ SOFTWARE IN PHYSICAL SECURITY MARKET, BY TYPE, 2020-2029 (USD MILLION)
TABLE 19 IRAQ PHYSICAL SECURITY MARKET, BY AUTHENTICATION, 2020-2029 (USD MILLION)
TABLE 20 IRAQ CYBER SECURITY MARKET, BY APPLICATION, 2020-2029 (USD MILLION)
TABLE 21 IRAQ CYBER SECURITY MARKET, BY SECURITY TYPE, 2020-2029 (USD MILLION)
TABLE 22 IRAQ PHYSICAL SECURITY MARKET, BY DEPLOYMENT MODEL, 2020-2029 (USD MILLION)
TABLE 23 IRAQ CYBER SECURITY MARKET, BY DEPLOYMENT MODEL, 2020-2029 (USD MILLION)
TABLE 24 IRAQ PHYSICAL SECURITY MARKET, BY ENTERPRISE SIZE, 2020-2029 (USD MILLION)
TABLE 25 IRAQ CYBER SECURITY MARKET, BY ENTERPRISE SIZE, 2020-2029 (USD MILLION)
TABLE 26 IRAQ LARGE SIZED ENTERPRISES IN PHYSICAL SECURITY MARKET, BY DEPLOYMENT MODEL, 2020-2029 (USD MILLION)
TABLE 27 IRAQ LARGE SIZED ENTERPRISES IN CYBER SECURITY MARKET, BY DEPLOYMENT MODEL, 2020-2029 (USD MILLION)
TABLE 28 IRAQ SMALL AND MEDIUM-SIZED ENTERPRISES IN PHYSICAL SECURITY MARKET, BY DEPLOYMENT MODEL, 2020-2029 (USD MILLION)
TABLE 29 IRAQ SMALL AND MEDIUM-SIZED ENTERPRISES IN CYBER SECURITY MARKET, BY DEPLOYMENT MODEL, 2020-2029 (USD MILLION)
TABLE 30 IRAQ PHYSICAL SECURITY MARKET, BY END USER, 2020-2029 (USD MILLION)
TABLE 31 IRAQ CYBER SECURITY MARKET, BY END USER, 2020-2029 (USD MILLION)
TABLE 32 IRAQ COMMERCIAL IN PHYSICAL SECURITY MARKET, BY TYPE, 2020-2029 (USD MILLION)
TABLE 33 IRAQ COMMERCIAL IN CYBER SECURITY MARKET, BY TYPE, 2020-2029 (USD MILLION)
TABLE 34 IRAQ INDUSTRIAL IN PHYSICAL SECURITY MARKET, BY TYPE 2020-2029 (USD MILLION)
TABLE 35 IRAQ INDUSTRIAL IN CYBER SECURITY MARKET, BY TYPE 2020-2029 (USD MILLION)
TABLE 36 IRAQ RESIDENTIAL IN PHYSICAL SECURITY MARKET, BY TYPE 2020-2029 (USD MILLION)
TABLE 37 IRAQ RESIDENTIAL IN CYBER SECURITY MARKET, BY TYPE 2020-2029 (USD MILLION)
图片列表
FIGURE 1 IRAQ PHYSICAL AND CYBER SECURITY MARKET: SEGMENTATION
FIGURE 2 IRAQ PHYSICAL AND CYBER SECURITY MARKET: DATA TRIANGULATION
FIGURE 3 IRAQ PHYSICAL AND CYBER SECURITY MARKET: DROC ANALYSIS
FIGURE 4 IRAQ PHYSICAL SECURITY MARKET: REGIONAL VS COUNTRY ANALYSIS
FIGURE 5 IRAQ CYBER SECURITY MARKET: REGIONAL VS COUNTRY ANALYSIS
FIGURE 6 IRAQ PHYSICAL AND CYBER SECURITY MARKET: COMPANY RESEARCH ANALYSIS
FIGURE 7 IRAQ PHYSICAL AND CYBER SECURITY MARKET: INTERVIEW DEMOGRAPHICS
FIGURE 8 IRAQ PHYSICAL SECURITY MARKET: DBMR MARKET POSITION GRID
FIGURE 9 IRAQ CYBER SECURITY MARKET: DBMR MARKET POSITION GRID
FIGURE 10 IRAQ CYBER SECURITY MARKET: VENDOR SHARE ANALYSIS
FIGURE 11 IRAQ PHYSICAL SECURITY MARKET: VENDOR SHARE ANALYSIS
FIGURE 12 IRAQ PHYSICAL SECURITY MARKET: MARKET END USER COVERAGE GRID
FIGURE 13 IRAQ CYBER SECURITY MARKET: MARKET END USER COVERAGE GRID
FIGURE 14 IRAQ CYBER SECURITY MARKET: SEGMENTATION
FIGURE 15 IRAQ PHYSICAL SECURITY MARKET: SEGMENTATION
FIGURE 16 AN INCREASE IN CLOUD SERVICES CYBER AND PHYSICAL SECURITY SOLUTIONS IS EXPECTED TO DRIVE IRAQ PHYSICAL SECURITY MARKET IN THE FORECAST PERIOD OF 2022 TO 2029
FIGURE 17 EMERGENCE OF SMART INTERCONNECTED BUILDING/HOME IS EXPECTED TO DRIVE IRAQ CYBER SECURITY MARKET IN THE FORECAST PERIOD OF 2022 TO 2029
FIGURE 18 SERVICES SEGMENT IS EXPECTED TO ACCOUNT FOR THE LARGEST SHARE OF IRAQ CYBER SECURITY MARKET IN THE FORECASTED PERIOD OF 2022 & 2029
FIGURE 19 HARDWARE SEGMENT IS EXPECTED TO ACCOUNT FOR THE LARGEST SHARE OF IRAQ PHYSICAL SECURITY MARKET IN THE FORECASTED PERIOD OF 2022 & 2029
FIGURE 20 VALUE CHAIN FOR PHYSICAL AND CYBER SECURITY MARKET
FIGURE 21 PORTERS FIVE FORCES ANALYSIS FOR PHYSICAL AND CYBER SECURITY MARKET
FIGURE 22 PESTLE ANALYSIS FOR PHYSICAL AND CYBER SECURITY MARKET
FIGURE 23 DRIVERS, RESTRAINTS, OPPORTUNITIES, AND CHALLENGES OF IRAQ PHYSICAL AND CYBER SECURITY MARKET
FIGURE 24 KEY STATS OF REMOTE WORK
FIGURE 25 GROWING PREVALENCE OF BIOMETRIC SOLUTIONS AMONG CONSUMER
FIGURE 26 TECHNOLOGY AMALGAMATION IN SMART HOME/ BUILDINGS
FIGURE 27 IMPACT OF CYBER SECURITY THREAT
FIGURE 28 PHISHING ATTACKS REPORTED IN RESPECTIVE COUNTRIES IN Q2, 2021
FIGURE 29 IRAQ CYBER SECURITY MARKET, BY OFFERING, 2021
FIGURE 30 IRAQ PHYSICAL SECURITY MARKET, BY COMPONENT, 2021
FIGURE 31 IRAQ PHYSICAL SECURITY MARKET, BY AUTHENTICATION, 2021
FIGURE 32 IRAQ CYBER SECURITY MARKET: BY APPLICATION, 2021
FIGURE 33 IRAQ CYBER SECURITY MARKET: BY SECURITY TYPE, 2021
FIGURE 34 IRAQ PHYSICAL SECURITY MARKET, BY DEPLOYMENT MODEL, 2021
FIGURE 35 IRAQ CYBER SECURITY MARKET, BY DEPLOYMENT MODEL, 2021
FIGURE 36 IRAQ PHYSICAL SECURITY MARKET, BY ENTERPRISE SIZE, 2021
FIGURE 37 IRAQ CYBER SECURITY MARKET, BY ENTERPRISE SIZE, 2021
FIGURE 38 IRAQ PHYSICAL SECURITY MARKET: BY END USER, 2021
FIGURE 39 IRAQ CYBER SECURITY MARKET: BY END USER, 2021
FIGURE 40 IRAQ CYBER SECURITY MARKET: COMPANY SHARE 2021 (%)
FIGURE 41 IRAQ PHYSICAL SECURITY MARKET: COMPANY SHARE 2021 (%)
研究方法
数据收集和基准年分析是使用具有大样本量的数据收集模块完成的。该阶段包括通过各种来源和策略获取市场信息或相关数据。它包括提前检查和规划从过去获得的所有数据。它同样包括检查不同信息源中出现的信息不一致。使用市场统计和连贯模型分析和估计市场数据。此外,市场份额分析和关键趋势分析是市场报告中的主要成功因素。要了解更多信息,请请求分析师致电或下拉您的询问。
DBMR 研究团队使用的关键研究方法是数据三角测量,其中包括数据挖掘、数据变量对市场影响的分析和主要(行业专家)验证。数据模型包括供应商定位网格、市场时间线分析、市场概览和指南、公司定位网格、专利分析、定价分析、公司市场份额分析、测量标准、全球与区域和供应商份额分析。要了解有关研究方法的更多信息,请向我们的行业专家咨询。
可定制
Data Bridge Market Research 是高级形成性研究领域的领导者。我们为向现有和新客户提供符合其目标的数据和分析而感到自豪。报告可定制,包括目标品牌的价格趋势分析、了解其他国家的市场(索取国家列表)、临床试验结果数据、文献综述、翻新市场和产品基础分析。目标竞争对手的市场分析可以从基于技术的分析到市场组合策略进行分析。我们可以按照您所需的格式和数据样式添加您需要的任意数量的竞争对手数据。我们的分析师团队还可以为您提供原始 Excel 文件数据透视表(事实手册)中的数据,或者可以帮助您根据报告中的数据集创建演示文稿。