Global Industrial Cybersecurity Market
Размер рынка в млрд долларов США
CAGR :
% 
 USD
17.66 Billion
USD
30.57 Billion
2024
2032
USD
17.66 Billion
USD
30.57 Billion
2024
2032
| 2025 –2032 | |
| USD 17.66 Billion | |
| USD 30.57 Billion | |
|
|
|
|
Глобальный рынок промышленной кибербезопасности по компонентам (решения, услуги), типу безопасности (безопасность конечных точек, сетевая безопасность, безопасность приложений, облачная безопасность и другие), развертыванию (локально, облако) и конечному пользователю (промышленное производство, транспорт и логистика, энергетика и коммунальные услуги и другие) — тенденции отрасли и прогноз до 2032 года.
Размер рынка промышленной кибербезопасности
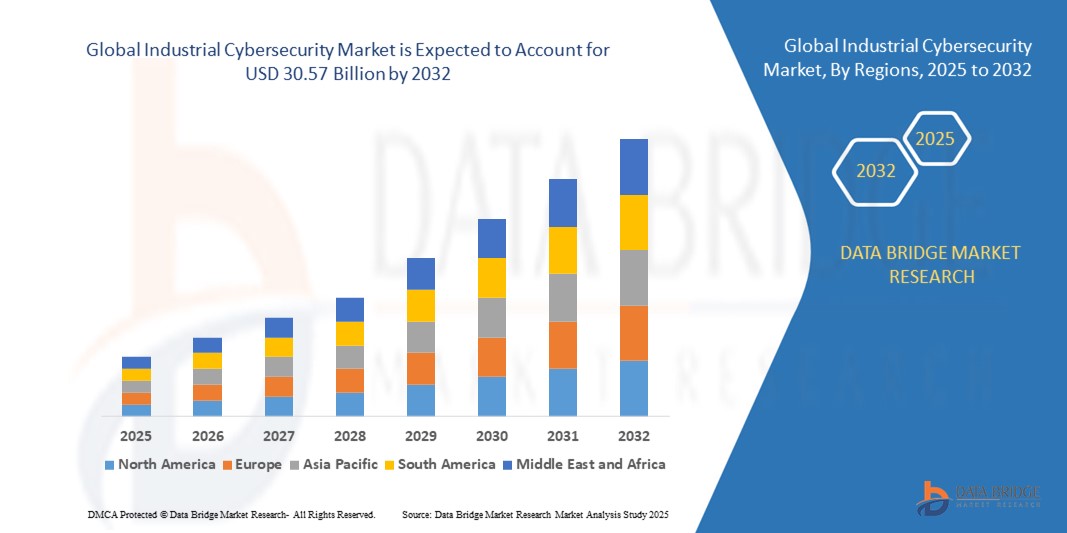
- Объем мирового рынка промышленной кибербезопасности в 2024 году оценивался в 17,66 млрд долларов США , а к 2032 году , как ожидается, он достигнет 30,57 млрд долларов США при среднегодовом темпе роста 7,10% в прогнозируемый период.
- Рост рынка обусловлен, прежде всего, увеличением частоты киберугроз, внедрением технологий Индустрии 4.0 и растущей потребностью в безопасной цифровой трансформации в промышленных секторах.
- Растущая осведомленность о рисках кибербезопасности и требованиях к соблюдению нормативных требований среди промышленных организаций еще больше стимулирует спрос на передовые решения и услуги в области кибербезопасности в различных отраслях.
Анализ рынка промышленной кибербезопасности
- Рынок промышленной кибербезопасности переживает бурный рост из-за растущего внедрения устройств Интернета вещей, автоматизации и подключенных промышленных систем, которые повышают уязвимость к кибератакам.
- Растущий спрос со стороны критически важных секторов инфраструктуры, таких как энергетика, производство и транспорт, побуждает поставщиков внедрять инновации, предлагая передовые решения для обнаружения угроз, реагирования на инциденты и обеспечения безопасности с нулевым доверием.
- Северная Америка доминировала на рынке промышленной кибербезопасности с наибольшей долей выручки в 32,9% в 2024 году, что обусловлено развитостью промышленного сектора, строгой нормативно-правовой базой и широким внедрением передовых технологий кибербезопасности.
- Ожидается, что Азиатско-Тихоокеанский регион станет самым быстрорастущим регионом в прогнозируемый период, чему будут способствовать быстрая индустриализация, растущее внедрение технологий интеллектуального производства и рост осведомленности о кибербезопасности в таких странах, как Китай, Индия и Япония.
- Сегмент решений занял самую большую долю рынка в 37,9% в 2024 году, что обусловлено острой потребностью в комплексных решениях по кибербезопасности, таких как межсетевые экраны и системы обнаружения вторжений, для защиты промышленных сред от растущих угроз.
Область применения отчета и сегментация рынка промышленной кибербезопасности
|
Атрибуты |
Ключевые аспекты рынка промышленной кибербезопасности |
|
Охваченные сегменты |
|
|
Охваченные страны |
Северная Америка
Европа
Азиатско-Тихоокеанский регион
Ближний Восток и Африка
Южная Америка
|
|
Ключевые игроки рынка |
|
|
Рыночные возможности |
|
|
Информационные наборы данных с добавленной стоимостью |
Помимо таких рыночных данных, как рыночная стоимость, темпы роста, сегменты рынка, географический охват, участники рынка и рыночный сценарий, отчет о рынке, подготовленный командой Data Bridge Market Research, включает в себя углубленный экспертный анализ, анализ импорта/экспорта, анализ цен, анализ потребления продукции и анализ пестицидов. |
Тенденции рынка промышленной кибербезопасности
Растущая интеграция ИИ и машинного обучения в решениях по кибербезопасности
- На мировом рынке промышленной кибербезопасности наблюдается значительная тенденция к интеграции искусственного интеллекта (ИИ) и машинного обучения (МО) в решения по кибербезопасности.
- Эти технологии обеспечивают расширенное обнаружение угроз, мониторинг в реальном времени и прогнозную аналитику, обеспечивая более глубокое понимание потенциальных уязвимостей и моделей атак в промышленных системах.
- Платформы кибербезопасности на базе искусственного интеллекта могут заблаговременно выявлять и нейтрализовать угрозы до того, как они приведут к сбоям в работе или утечкам данных, повышая устойчивость системы.
- Например, компании разрабатывают решения на основе искусственного интеллекта, которые анализируют сетевой трафик и поведение системы для обнаружения аномалий, таких как несанкционированный доступ или вредоносное ПО, а также оптимизируют меры безопасности для таких отраслей, как производство и энергетика.
- Эта тенденция способствует более широкому внедрению интеллектуальных систем кибербезопасности, делая их более привлекательными для промышленных операторов, стремящихся защитить критически важную инфраструктуру.
- Алгоритмы искусственного интеллекта и машинного обучения могут анализировать огромные наборы данных, включая системные журналы, сетевой трафик и поведение пользователей, чтобы выявлять закономерности, указывающие на киберугрозы, такие как программы-вымогатели, фишинг или атаки типа «распределенный отказ в обслуживании» (DDoS).
Динамика рынка промышленной кибербезопасности
Водитель
Растущий спрос на безопасные промышленные системы управления и защиту критической инфраструктуры
- Растущая зависимость от устройств промышленного Интернета вещей (IIoT), автоматизации и взаимосвязанных систем обуславливает спрос на надежные решения по кибербезопасности в промышленном секторе.
- Системы кибербезопасности повышают эксплуатационную безопасность, предоставляя такие функции, как обнаружение угроз в режиме реального времени, предотвращение вторжений и безопасный удаленный доступ к промышленным системам управления (ICS).
- Правительственные постановления, такие как Рамочная программа кибербезопасности NIST в Северной Америке и Директива NIS ЕС, требуют более строгих мер кибербезопасности для критически важной инфраструктуры, что дополнительно стимулирует рост рынка.
- Распространение технологий 5G и Интернета вещей обеспечивает более быструю передачу данных и меньшую задержку, поддерживая передовые приложения кибербезопасности, такие как мониторинг и реагирование в реальном времени в промышленных средах.
- Промышленные операторы все чаще используют интегрированные решения по кибербезопасности в качестве стандарта для соблюдения нормативных требований и защиты критически важных активов в таких секторах, как производство, энергетика и транспорт.
Сдержанность/Вызов
Высокие затраты на внедрение и проблемы с конфиденциальностью данных
- Значительные первоначальные инвестиции, необходимые для оборудования и программного обеспечения кибербезопасности, а также для интеграции в существующие промышленные системы, могут стать серьезным препятствием, особенно для малых и средних предприятий (МСП) на развивающихся рынках.
- Интеграция решений по кибербезопасности в устаревшие промышленные системы управления часто является сложным и дорогостоящим процессом, требующим специальных знаний и модернизации инфраструктуры.
- Вопросы конфиденциальности и безопасности данных представляют собой серьезную проблему, поскольку промышленные системы кибербезопасности собирают и обрабатывают конфиденциальные эксплуатационные и персональные данные, повышая риск нарушений или неправомерного использования.
- Разрозненность нормативно-правовой базы в разных странах, а также различные стандарты защиты данных и соответствия требованиям кибербезопасности усложняют деятельность мировых производителей и поставщиков услуг.
- Эти факторы могут сдерживать внедрение, особенно в регионах с высокой чувствительностью к затратам или строгими требованиями к конфиденциальности данных, что ограничивает расширение рынка.
Рынок промышленной кибербезопасности: сфера применения
Рынок сегментирован по принципу компонента, типа безопасности, развертывания и конечного пользователя.
- По компонентам
По компонентному составу мировой рынок промышленной кибербезопасности сегментируется на решения и услуги. Сегмент решений занял наибольшую долю рынка – 37,9% в 2024 году. Это обусловлено острой потребностью в комплексных решениях кибербезопасности, таких как межсетевые экраны и системы обнаружения вторжений, для защиты промышленных сред от растущих угроз.
Ожидается, что сегмент услуг продемонстрирует самые быстрые темпы роста в период с 2025 по 2032 год. Это обусловлено растущей сложностью и частотой кибератак, что увеличивает спрос на профессиональные и управляемые услуги, такие как обнаружение угроз, реагирование на инциденты и управление соответствием требованиям.
- По типу безопасности
По типу безопасности глобальный рынок промышленной кибербезопасности сегментируется на следующие сегменты: безопасность конечных точек, сетевая безопасность, безопасность приложений, облачная безопасность и другие. Ожидается, что сегмент сетевой безопасности займет наибольшую долю рынка в 2024 году. Это связано с растущим внедрением взаимосвязанных промышленных систем, что делает защиту потоков данных и предотвращение несанкционированного доступа крайне важными.
Ожидается, что сегмент облачной безопасности продемонстрирует значительный рост в период с 2025 по 2032 год. Это обусловлено быстрым внедрением облачных сервисов и переходом на модели удаленной работы, что требует надежных решений по безопасности для защиты облачных приложений и данных.
- По развертыванию
По принципу развертывания глобальный рынок промышленной кибербезопасности сегментируется на локальные и облачные решения. Ожидается, что локальный сегмент займет наибольшую долю рынка, в первую очередь из-за того, что некоторые отрасли предпочитают сохранять прямой контроль над своими конфиденциальными данными и использовать специализированные фреймворки безопасности.
Ожидается, что сегмент облачных технологий будет демонстрировать самые быстрые темпы роста в период с 2025 по 2032 год, что обусловлено потребностью в гибких, масштабируемых и экономичных решениях безопасности. Облачные платформы позволяют организациям быстро адаптироваться к меняющимся угрозам и оптимизировать управление системами безопасности.
- Конечным пользователем
По принципу конечного пользователя глобальный рынок промышленной кибербезопасности сегментируется на промышленное производство, транспорт и логистику, энергетику и коммунальные услуги и другие. Ожидается, что сегмент промышленного производства займет наибольшую долю рынка благодаря растущей цифровизации производственных процессов, включая использование интеллектуальных фабрик и промышленного Интернета вещей (IIoT), что расширяет поверхность атак и повышает потребность в комплексной безопасности.
Ожидается, что сектор энергетики и коммунальных услуг будет демонстрировать устойчивый рост в период с 2025 по 2032 год. Это обусловлено критически важным характером этих инфраструктур, делающим их основными целями для кибератак и влекущим значительные инвестиции в кибербезопасность для обеспечения непрерывности работы и общественной безопасности.
Региональный анализ рынка промышленной кибербезопасности
- Северная Америка доминирует на рынке промышленной кибербезопасности с наибольшей долей выручки в 32,9% в 2024 году, что обусловлено развитостью промышленного сектора, строгой нормативно-правовой базой и широким внедрением передовых технологий кибербезопасности.
- Потребители и отрасли отдают приоритет решениям в области кибербезопасности для защиты критически важной инфраструктуры, обеспечения непрерывности работы и снижения уровня сложных киберугроз, особенно в регионах с высоким уровнем цифровизации.
- Росту способствуют достижения в области решений безопасности на основе искусственного интеллекта, облачных платформ и растущее внедрение как в локальных, так и в облачных сегментах развертывания в различных отраслях.
Обзор рынка промышленной кибербезопасности в США
Рынок промышленной кибербезопасности США в 2024 году занял наибольшую долю выручки в Северной Америке – 78,5%. Этому способствовали значительные инвестиции в инфраструктуру кибербезопасности и растущая осведомлённость о киберугрозах в критически важных секторах, таких как энергетика и производство. Тенденция к соблюдению нормативных требований, таких как инициативы NIST и CISA, дополнительно стимулирует расширение рынка. Интеграция передовых решений в области кибербезопасности как в промышленные системы управления (ICS), так и в среды операционных технологий (OT) способствует формированию устойчивой рыночной экосистемы.
Обзор европейского рынка промышленной кибербезопасности
Ожидается, что европейский рынок промышленной кибербезопасности продемонстрирует значительный рост, чему будут способствовать строгие правила, такие как GDPR, и рост киберугроз, направленных на промышленные секторы. Предприятия ищут решения, которые повышают безопасность сетей и обеспечивают соответствие требованиям, сохраняя при этом эффективность работы. Рост заметен как в сфере новых установок, так и в проектах модернизации, причём такие страны, как Германия и Франция, демонстрируют значительное развитие благодаря своей мощной промышленной базе и ориентации на цифровую трансформацию.
Обзор рынка промышленной кибербезопасности в Великобритании
Ожидается, что рынок промышленной кибербезопасности в Великобритании будет демонстрировать быстрый рост, обусловленный растущим спросом на защищённые промышленные системы и повышением осведомлённости о киберрисках в городских и промышленных условиях. Растёт внедрение передовых решений, таких как системы обнаружения угроз на основе искусственного интеллекта и облачные платформы безопасности. Меняющиеся нормативные акты, например, Европейской комиссии, влияют на баланс между надёжными мерами кибербезопасности и соблюдением требований.
Обзор рынка промышленной кибербезопасности в Германии
Ожидается, что рынок промышленной кибербезопасности в Германии будет стремительно расти благодаря развитому производственному сектору и акценту на защите критически важной инфраструктуры. Немецкая промышленность отдает предпочтение технологически передовым решениям, таким как сетевая безопасность и защита конечных точек, для защиты операционных технологий и снижения уязвимостей. Интеграция кибербезопасности в премиальные промышленные системы и услуги послепродажного обслуживания способствует устойчивому росту рынка.
Обзор рынка промышленной кибербезопасности в Азиатско-Тихоокеанском регионе
Ожидается, что Азиатско-Тихоокеанский регион будет демонстрировать самые высокие темпы роста благодаря стремительной индустриализации, широкому внедрению Интернета вещей и подключенных устройств, а также активизации государственных инициатив в области кибербезопасности в таких странах, как Китай, Индия и Япония. Растущее понимание киберугроз и потребность в надежных системах безопасности в производственном и энергетическом секторах стимулируют спрос. Инвестиции в облачные решения и системы обнаружения угроз на основе искусственного интеллекта дополнительно ускоряют рост рынка.
Обзор рынка промышленной кибербезопасности в Японии
Ожидается, что рынок промышленной кибербезопасности в Японии будет демонстрировать быстрый рост благодаря высокому спросу потребителей и отрасли на высококачественные, передовые решения в области кибербезопасности, повышающие эксплуатационную безопасность и устойчивость. Присутствие крупных промышленных игроков и интеграция кибербезопасности в операционные технологии ускоряют проникновение на рынок. Растущий интерес к услугам кибербезопасности на вторичном рынке также способствует росту.
Обзор рынка промышленной кибербезопасности в Китае
Китай занимает наибольшую долю на рынке промышленной кибербезопасности Азиатско-Тихоокеанского региона, чему способствуют стремительная цифровизация, рост промышленной автоматизации и растущий спрос на безопасные инфраструктурные решения. Расширение промышленной базы страны и ориентация на интеллектуальное производство способствуют внедрению передовых решений в области кибербезопасности. Значительный внутренний инновационный потенциал и конкурентоспособные цены способствуют доступности рынка и его росту.
Доля рынка промышленной кибербезопасности
В отрасли промышленной кибербезопасности лидируют в основном хорошо зарекомендовавшие себя компании, среди которых:
- Fortinet, Inc. (США)
- Cisco Systems, Inc. (США)
- Juniper Networks, Inc. (США)
- Palo Alto Networks, Inc. (США)
- Корпорация IBM (США)
- Check Point Software Technologies Ltd. (Израиль)
- F5, Inc. (США)
- Splunk, Inc. (США)
- Mandiant, Inc. (США)
- Broadcom, Inc. (США)
- Корпорация Oracle (США)
- Корпорация Microsoft (США)
- Корпорация Intel (США)
- Imperva, Inc. (США)
- Cyberark Software Ltd. (США)
- RSA Security LLC (США)
Каковы последние события на мировом рынке промышленной кибербезопасности?
- В сентябре 2023 года компания Cisco Systems, Inc. объявила о намерении приобрести Splunk, ведущую компанию в области кибербезопасности и наблюдения, на общую сумму, эквивалентную стоимости акций. Это приобретение, одно из крупнейших в этом году, призвано значительно расширить бизнес Cisco в области программного обеспечения и ускорить разработку решений по безопасности и наблюдению на основе искусственного интеллекта. Объединяя возможности аналитики данных Splunk с сетевой инфраструктурой и инфраструктурой кибербезопасности Cisco, сделка призвана помочь организациям перейти от обнаружения и реагирования на угрозы к прогнозированию и предотвращению угроз, что ознаменует собой существенный сдвиг в сфере кибербезопасности.
- В августе 2023 года компания Johnson Controls выпустила рекомендации по безопасности продукта, касающиеся уязвимости в своих продуктах American Dynamics VideoEdge, обозначенной как CVE-2023-3749. Эта уязвимость позволяет локальному пользователю изменять файл конфигурации VideoEdge, что потенциально нарушает работу системы. Уязвимости подвержены все версии до 6.1.1. Для снижения риска Johnson Controls рекомендовала клиентам обновиться до версии 6.1.1, доступной на портале поддержки American Dynamics. В рекомендациях подчеркивается важность регулярных обновлений безопасности и контроля доступа для защиты промышленных систем управления и инфраструктуры видеонаблюдения.
- В мае 2023 года Агентство по кибербезопасности и безопасности инфраструктуры (CISA) представило свой Стратегический план на 2023–2025 годы, который стал первой комплексной дорожной картой с момента его основания в 2018 году. В плане обозначены четыре ключевые цели: киберзащита, снижение рисков и повышение устойчивости, оперативное взаимодействие и объединение агентств. В нём особое внимание уделяется проактивному, унифицированному подходу к кибербезопасности, направленному на повышение устойчивости критически важной инфраструктуры США посредством тесного взаимодействия с федеральными агентствами и партнёрами из частного сектора. Стратегия CISA отражает дальновидную приверженность предотвращению угроз, обмену информацией и обеспечению готовности национальной безопасности в условиях всё более сложного цифрового ландшафта.
- В апреле 2023 года компания Akamai Technologies, Inc. объявила о намерении приобрести Neosec, частную платформу обнаружения и реагирования на API, основанную на анализе данных и поведенческой аналитике. Это приобретение призвано расширить портфель решений Akamai для безопасности приложений и API, предоставляя клиентам более полную картину активности API и позволяя им обнаруживать угрозы в режиме реального времени. Технологии Neosec помогают организациям обнаруживать API, оценивать риски и реагировать на уязвимости, решая растущие проблемы кибербезопасности, связанные с архитектурами на основе API. Этот стратегический шаг выводит Akamai на передовые позиции в области безопасности API на основе ИИ — быстрорастущего сегмента цифровой защиты.
- В феврале 2023 года компания Accenture приобрела Morphus, бразильского поставщика услуг киберзащиты, управления рисками и анализа киберугроз. Благодаря этому приобретению в Accenture работает более 230 специалистов по кибербезопасности, что практически удваивает присутствие компании в Бразилии и расширяет её присутствие в Латинской Америке. Опыт Morphus в сфере услуг для команд «красных и синих» команд, управления и услуг по управлению безопасностью укрепляет возможности Accenture по оказанию помощи клиентам в построении киберустойчивого бизнеса. Этот шаг также знаменует собой запуск в регионе киберотраслевой практики, что подтверждает стремление Accenture к глобальному лидерству в области кибербезопасности.
SKU-
Get online access to the report on the World's First Market Intelligence Cloud
- Интерактивная панель анализа данных
- Панель анализа компании для возможностей с высоким потенциалом роста
- Доступ аналитика-исследователя для настройки и запросов
- Анализ конкурентов с помощью интерактивной панели
- Последние новости, обновления и анализ тенденций
- Используйте возможности сравнительного анализа для комплексного отслеживания конкурентов
Методология исследования
Сбор данных и анализ базового года выполняются с использованием модулей сбора данных с большими размерами выборки. Этап включает получение рыночной информации или связанных данных из различных источников и стратегий. Он включает изучение и планирование всех данных, полученных из прошлого заранее. Он также охватывает изучение несоответствий информации, наблюдаемых в различных источниках информации. Рыночные данные анализируются и оцениваются с использованием статистических и последовательных моделей рынка. Кроме того, анализ доли рынка и анализ ключевых тенденций являются основными факторами успеха в отчете о рынке. Чтобы узнать больше, пожалуйста, запросите звонок аналитика или оставьте свой запрос.
Ключевой методологией исследования, используемой исследовательской группой DBMR, является триангуляция данных, которая включает в себя интеллектуальный анализ данных, анализ влияния переменных данных на рынок и первичную (отраслевую экспертную) проверку. Модели данных включают сетку позиционирования поставщиков, анализ временной линии рынка, обзор рынка и руководство, сетку позиционирования компании, патентный анализ, анализ цен, анализ доли рынка компании, стандарты измерения, глобальный и региональный анализ и анализ доли поставщика. Чтобы узнать больше о методологии исследования, отправьте запрос, чтобы поговорить с нашими отраслевыми экспертами.
Доступна настройка
Data Bridge Market Research является лидером в области передовых формативных исследований. Мы гордимся тем, что предоставляем нашим существующим и новым клиентам данные и анализ, которые соответствуют и подходят их целям. Отчет можно настроить, включив в него анализ ценовых тенденций целевых брендов, понимание рынка для дополнительных стран (запросите список стран), данные о результатах клинических испытаний, обзор литературы, обновленный анализ рынка и продуктовой базы. Анализ рынка целевых конкурентов можно проанализировать от анализа на основе технологий до стратегий портфеля рынка. Мы можем добавить столько конкурентов, о которых вам нужны данные в нужном вам формате и стиле данных. Наша команда аналитиков также может предоставить вам данные в сырых файлах Excel, сводных таблицах (книга фактов) или помочь вам в создании презентаций из наборов данных, доступных в отчете.