السوق العالمية لأمن الثقة الصفرية، حسب نوع المصادقة (مصادقة أحادية العامل، مصادقة متعددة العوامل)، نوع الحل ( أمن البيانات ، أمن نقطة النهاية، أمن واجهة برمجة التطبيقات، تحليلات الأمان، إدارة سياسة الأمان)، النشر (محليًا، سحابيًا)، حجم المنظمة (الشركات الصغيرة والمتوسطة، المؤسسات الكبيرة)، العمودي ( الخدمات المصرفية، الخدمات المالية والتأمين ، تكنولوجيا المعلومات والاتصالات، الحكومة والدفاع، الطاقة والمرافق، الرعاية الصحية، التجزئة والتجارة الإلكترونية، أخرى)، الدولة (الولايات المتحدة وكندا والمكسيك والبرازيل والأرجنتين وبقية أمريكا الجنوبية وألمانيا وفرنسا وإيطاليا والمملكة المتحدة وبلجيكا وإسبانيا وروسيا وتركيا وهولندا وسويسرا وبقية أوروبا واليابان والصين والهند وكوريا الجنوبية وأستراليا وسنغافورة وماليزيا وتايلاند وإندونيسيا والفلبين وبقية آسيا والمحيط الهادئ والإمارات العربية المتحدة والمملكة العربية السعودية ومصر وجنوب إفريقيا وإسرائيل وبقية الشرق الأوسط وأفريقيا) - اتجاهات الصناعة والتوقعات حتى عام 2029.
تحليل السوق ورؤى سوق الأوراق المالية ذات الثقة الصفرية
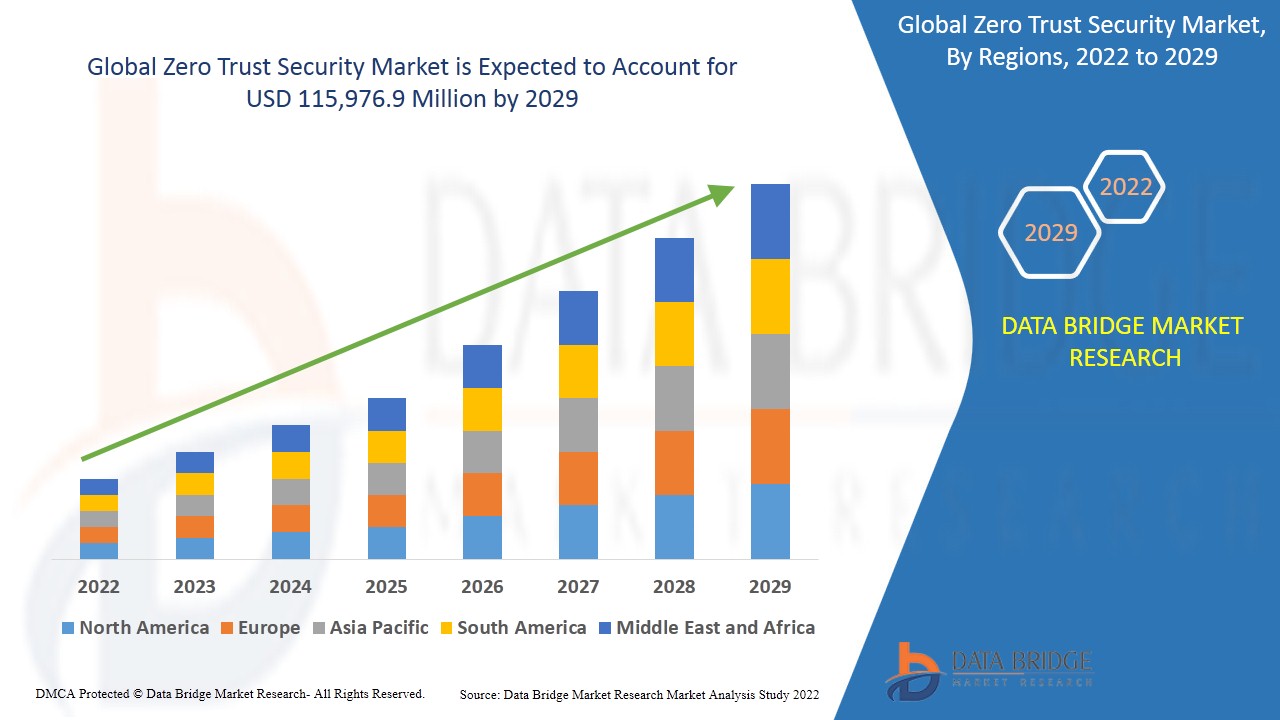
من المتوقع أن يحقق سوق أمن الثقة الصفرية نموًا في السوق في الفترة المتوقعة من 2022 إلى 2029. تحلل شركة Data Bridge Market Research السوق لترتفع إلى 115،976.9 مليون دولار أمريكي بحلول عام 2029 وتنمو بمعدل نمو سنوي مركب قدره 15.20٪ في الفترة المتوقعة المذكورة أعلاه.
تشير الثقة الصفرية إلى نموذج أمان يقوم على مبدأ ضوابط الوصول الصارمة وعدم الثقة في أي شخص بشكل افتراضي، حتى أولئك الموجودين بالفعل داخل محيط الشبكة. تم إعداد النموذج بطريقة تجعل كل شخص وجهاز يحاول الوصول إلى الموارد على شبكة خاصة يجب أن يجتاز التحقق الصارم من الهوية، بغض النظر عما إذا كانوا داخل محيط الشبكة أو خارجه. إنه نهج شامل لأمن الشبكة يشتمل على مجموعة متنوعة من التقنيات.
من المتوقع أن تظهر عوامل مثل زيادة اعتماد حلول الأمان القائمة على الثقة الصفرية، وارتفاع الرقمنة، وارتفاع عدد نقاط الضعف السيبرانية بسبب اعتماد الخدمات المستندة إلى السحابة ، كعوامل مهمة لتسريع نمو سوق الأمان القائمة على الثقة الصفرية. بالإضافة إلى ذلك، فإن عوامل مثل زيادة الوعي والاستثمار في حلول الأمان القائمة على الثقة الصفرية، وزيادة اللوائح الحكومية مثل لوائح CCPA القادمة، وزيادة انتشار تقنيات إنترنت الأشياء والشركات التي تختار البائعين من جهات خارجية، وزيادة عدد المخاطر السيبرانية، وارتفاع وتيرة الهجمات السيبرانية القائمة على الأهداف، وزيادة اللوائح الخاصة بحماية البيانات وأمن المعلومات، من شأنها أن تزيد من تفاقم نمو سوق الأمان القائمة على الثقة الصفرية في فترة التنبؤ المذكورة أعلاه. ومع ذلك، فإن القيود الميزانية المتزايدة بين الشركات الناشئة الصغيرة والناشئة في الاقتصادات النامية تؤدي إلى تقييد نمو السوق.
ومن المتوقع أيضًا أن يؤدي الطلب المتزايد على رؤية أفضل بسبب ارتفاع حركة إنترنت الأشياء بين الشركات، والحاجة المتزايدة إلى حلول أمان الثقة الصفرية المستندة إلى السحابة بين الشركات الصغيرة والمتوسطة الحجم والتقدم التكنولوجي المتزايد والتحديث في التقنيات المستخدمة إلى توليد فرص مربحة لسوق أمان الثقة الصفرية في الفترة المتوقعة من 2022 إلى 2029. ستشكل قيود التصميم والتنفيذ المتزايدة لنشر حلول أمان الثقة الصفرية تحديًا لسوق أمان الثقة الصفرية.
يقدم تقرير سوق أمن الثقة الصفرية هذا تفاصيل عن التطورات الحديثة الجديدة واللوائح التجارية وتحليل الاستيراد والتصدير وتحليل الإنتاج وتحسين سلسلة القيمة وحصة السوق وتأثير اللاعبين المحليين والمحليين في السوق وتحليل الفرص من حيث جيوب الإيرادات الناشئة والتغيرات في لوائح السوق وتحليل نمو السوق الاستراتيجي وحجم السوق ونمو سوق الفئات ومنافذ التطبيق والهيمنة وموافقات المنتجات وإطلاق المنتجات والتوسعات الجغرافية والابتكارات التكنولوجية في السوق. للحصول على مزيد من المعلومات حول سوق أمن الثقة الصفرية، اتصل بـ Data Bridge Market Research للحصول على موجز محلل ، سيساعدك فريقنا في اتخاذ قرار سوقي مستنير لتحقيق نمو السوق.
نطاق وحجم سوق الأوراق المالية العالمية القائمة على الثقة الصفرية
يتم تقسيم سوق أمن الثقة الصفرية على أساس نوع المصادقة ونوع الحل والنشر وحجم المنظمة والقطاع. يساعدك النمو بين القطاعات المختلفة في اكتساب المعرفة المتعلقة بعوامل النمو المختلفة المتوقع انتشارها في جميع أنحاء السوق وصياغة استراتيجيات مختلفة للمساعدة في تحديد مجالات التطبيق الأساسية والاختلاف في السوق المستهدفة.
- على أساس نوع المصادقة، يتم تقسيم سوق أمان الثقة الصفرية إلى مصادقة أحادية العامل ومصادقة متعددة العوامل.
- على أساس نوع الحل، يتم تقسيم سوق أمان الثقة الصفرية إلى أمان البيانات، وأمان نقطة النهاية، وأمان واجهة برمجة التطبيقات، وتحليلات الأمان، وإدارة سياسة الأمان.
- على أساس النشر، يتم تقسيم سوق أمان الثقة الصفرية إلى محلي وسحابي.
- على أساس حجم المنظمة، يتم تقسيم سوق أمن الثقة الصفرية إلى الشركات الصغيرة والمتوسطة والمؤسسات الكبيرة.
يتم تقسيم سوق أمن الثقة الصفرية أيضًا على أساس عمودي إلى الخدمات المصرفية والخدمات المالية والتأمين وتكنولوجيا المعلومات والاتصالات والحكومة والدفاع والطاقة والمرافق والرعاية الصحية وتجارة التجزئة والتجارة الإلكترونية وغيرها.
تحليل على مستوى الدولة لسوق الأوراق المالية القائمة على الثقة الصفرية
يتم تقسيم سوق أمان الثقة الصفرية على أساس نوع المصادقة ونوع الحل والنشر وحجم المنظمة والقطاع الرأسي.
الدول التي يغطيها تقرير سوق أمن الثقة الصفرية هي الولايات المتحدة وكندا والمكسيك والبرازيل والأرجنتين وبقية أمريكا الجنوبية وألمانيا وفرنسا وإيطاليا والمملكة المتحدة وبلجيكا وإسبانيا وروسيا وتركيا وهولندا وسويسرا وبقية أوروبا واليابان والصين والهند وكوريا الجنوبية وأستراليا وسنغافورة وماليزيا وتايلاند وإندونيسيا والفلبين وبقية دول آسيا والمحيط الهادئ والإمارات العربية المتحدة والمملكة العربية السعودية ومصر وجنوب إفريقيا وإسرائيل وبقية دول الشرق الأوسط وأفريقيا.
تهيمن أمريكا الشمالية على سوق أمن الثقة الصفرية خلال فترة التنبؤ بسبب الاعتماد الكبير على التحول الرقمي مع توليد كميات كبيرة من البيانات الهامة، والحاجة المتزايدة إلى حلول أمن الثقة الصفرية، والرقمنة المتزايدة، وزيادة الوعي والاستثمار في حلول أمن الثقة الصفرية وزيادة اللوائح الحكومية مثل لوائح CCPA القادمة في هذه المنطقة في فترة التنبؤ من 2022 إلى 2029. من ناحية أخرى، من المتوقع أن تشهد منطقة آسيا والمحيط الهادئ نموًا مربحًا بسبب العدد الكبير من المخاطر الإلكترونية بسبب اعتماد الخدمات المستندة إلى السحابة في هذه المنطقة.
يقدم قسم الدولة في تقرير سوق الأوراق المالية ذات الثقة الصفرية أيضًا عوامل التأثير الفردية على السوق والتغيرات في التنظيم في السوق محليًا والتي تؤثر على الاتجاهات الحالية والمستقبلية للسوق. تعد نقاط البيانات مثل أحجام الاستهلاك ومواقع الإنتاج والكميات وتحليل الصادرات والواردات وتحليل اتجاه الأسعار وتكلفة المواد الخام وتحليل سلسلة القيمة النهائية والعليا من بين المؤشرات الرئيسية المستخدمة للتنبؤ بسيناريو السوق للدول الفردية. كما يتم النظر في وجود وتوافر العلامات التجارية العالمية والتحديات التي تواجهها بسبب المنافسة الكبيرة أو النادرة من العلامات التجارية المحلية والمحلية وتأثير التعريفات الجمركية المحلية وطرق التجارة أثناء تقديم تحليل توقعات لبيانات الدولة.
تحليل المشهد التنافسي وحصة سوق الأوراق المالية القائمة على الثقة الصفرية
يوفر المشهد التنافسي لسوق أمن الثقة الصفرية تفاصيل حسب المنافس. تتضمن التفاصيل نظرة عامة على الشركة، والبيانات المالية للشركة، والإيرادات المولدة، وإمكانات السوق، والاستثمار في البحث والتطوير، ومبادرات السوق الجديدة، والحضور العالمي، ومواقع الإنتاج والمرافق، والقدرات الإنتاجية، ونقاط القوة والضعف في الشركة، وإطلاق المنتج، وعرض المنتج ونطاقه، وهيمنة التطبيق. ترتبط نقاط البيانات المذكورة أعلاه فقط بتركيز الشركات فيما يتعلق بسوق أمن الثقة الصفرية.
بعض اللاعبين الرئيسيين العاملين في تقرير سوق أمان الثقة الصفرية هم Cisco و IBM و Akamai Technologies و Check Point Software Technologies Ltd و Pulse Secure، LLC و Palo Alto Networks و Cyxtera Technologies، Inc. و Broadcom و Okta و Cloudflare، Inc و Forcepoint و Centrify Corporation و FireEye و Cyxtera Technologies، Inc. و Illumio و Sophos Ltd و Microsoft من بين آخرين.
التطورات الأخيرة
- في سبتمبر 2020، استحوذت Check Point على تقنية Odo Security المستندة إلى السحابة لتوفير الوصول عن بُعد الآمن. قامت Check Point بدمج هذه التقنية مع بنية Infinity الخاصة بها لتوفير أبسط وأكثر الحلول أمانًا للشركات التي تسعى إلى الوصول عن بُعد الآمن إلى أي تطبيق.
SKU-
احصل على إمكانية الوصول عبر الإنترنت إلى التقرير الخاص بأول سحابة استخبارات سوقية في العالم
- لوحة معلومات تحليل البيانات التفاعلية
- لوحة معلومات تحليل الشركة للفرص ذات إمكانات النمو العالية
- إمكانية وصول محلل الأبحاث للتخصيص والاستعلامات
- تحليل المنافسين باستخدام لوحة معلومات تفاعلية
- آخر الأخبار والتحديثات وتحليل الاتجاهات
- استغل قوة تحليل المعايير لتتبع المنافسين بشكل شامل
منهجية البحث
يتم جمع البيانات وتحليل سنة الأساس باستخدام وحدات جمع البيانات ذات أحجام العينات الكبيرة. تتضمن المرحلة الحصول على معلومات السوق أو البيانات ذات الصلة من خلال مصادر واستراتيجيات مختلفة. تتضمن فحص وتخطيط جميع البيانات المكتسبة من الماضي مسبقًا. كما تتضمن فحص التناقضات في المعلومات التي شوهدت عبر مصادر المعلومات المختلفة. يتم تحليل بيانات السوق وتقديرها باستخدام نماذج إحصائية ومتماسكة للسوق. كما أن تحليل حصة السوق وتحليل الاتجاهات الرئيسية هي عوامل النجاح الرئيسية في تقرير السوق. لمعرفة المزيد، يرجى طلب مكالمة محلل أو إرسال استفسارك.
منهجية البحث الرئيسية التي يستخدمها فريق بحث DBMR هي التثليث البيانات والتي تتضمن استخراج البيانات وتحليل تأثير متغيرات البيانات على السوق والتحقق الأولي (من قبل خبراء الصناعة). تتضمن نماذج البيانات شبكة تحديد موقف البائعين، وتحليل خط زمني للسوق، ونظرة عامة على السوق ودليل، وشبكة تحديد موقف الشركة، وتحليل براءات الاختراع، وتحليل التسعير، وتحليل حصة الشركة في السوق، ومعايير القياس، وتحليل حصة البائعين على المستوى العالمي مقابل الإقليمي. لمعرفة المزيد عن منهجية البحث، أرسل استفسارًا للتحدث إلى خبراء الصناعة لدينا.
التخصيص متاح
تعد Data Bridge Market Research رائدة في مجال البحوث التكوينية المتقدمة. ونحن نفخر بخدمة عملائنا الحاليين والجدد بالبيانات والتحليلات التي تتطابق مع هدفهم. ويمكن تخصيص التقرير ليشمل تحليل اتجاه الأسعار للعلامات التجارية المستهدفة وفهم السوق في بلدان إضافية (اطلب قائمة البلدان)، وبيانات نتائج التجارب السريرية، ومراجعة الأدبيات، وتحليل السوق المجدد وقاعدة المنتج. ويمكن تحليل تحليل السوق للمنافسين المستهدفين من التحليل القائم على التكنولوجيا إلى استراتيجيات محفظة السوق. ويمكننا إضافة عدد كبير من المنافسين الذين تحتاج إلى بيانات عنهم بالتنسيق وأسلوب البيانات الذي تبحث عنه. ويمكن لفريق المحللين لدينا أيضًا تزويدك بالبيانات في ملفات Excel الخام أو جداول البيانات المحورية (كتاب الحقائق) أو مساعدتك في إنشاء عروض تقديمية من مجموعات البيانات المتوفرة في التقرير.